KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft Defender for Endpoint is currently blocking Office documents from being opened and some executables from launching due to a false positive tagging the files as potentially bundling an Emotet malware payload.
Windows system admins are reporting [1, 2, 3, 4, 5] that this is happening since updating Microsoft’s enterprise endpoint security platform (previously known as Microsoft Defender ATP) definitions to version 1.353.1874.0.
When triggered, Defender for Endpoint will block the file from opening and throw an error mentioning suspicious activity linked to Win32/PowEmotet.SB or Win32/PowEmotet.SC.
“We’re seeing issues with definition update 1.353.1874.0 detecting printing as Win32/PowEmotet.SB this afternoon,” one admin said.
Also Read: Does Personal Data Market About To Become The Next Big Thing
“We are seeing this detected for Excel, any Office app using MSIP.ExecutionHost.exe ( AIP Sensitivity Client ) and splwow64.exe,” another added.
A third one confirmed the issues with today’s definition updates: “We’re seeing the same behavior specifically with v.1.353.1874.0 of the definitions, which was released today, & included a definition for Behavior:Win32/PowEmotet.SB & Behavior:Win32/PowEmotet.SC.”
BleepingComputer was able to trigger the false positive on a Windows 10 virtual machine with the latest Microsoft Defender signatures, as shown below.
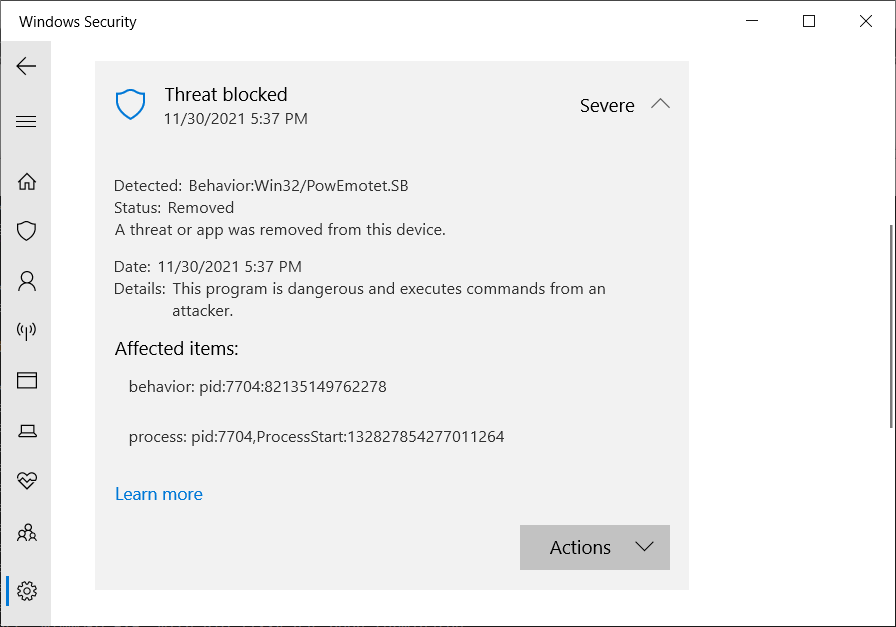
While Microsoft hasn’t yet shared any info on what causes this, the most likely reason is that the company has increased the sensitivity for detecting Emotet-like behavior in updates released today, which makes Defender’s generic behavioral detection engine too sensitive prone to false positives.
Also Read: Data Storage Security Standards: What Storage Professionals Need to Know
The change was likely prompted by the recent revival of the Emotet botnet from two weeks ago, after Emotet research group Cryptolaemus, GData, and Advanced Intel began seeing TrickBot dropping Emotet loaders on infected devices.
Even though this is almost surely not the real thing, the timing is definitely unfortunate with Emotet coming back and most Windows admins already on their toes.
As some of them have reported, they almost took their data centers offline to stop a possible Emotet infection from spreading before realizing that what they were seeing were likely false positives.
Since October 2020, Windows admins had to deal with other Defender for Endpoint including one that showed network devices infected with Cobalt Strike and another that marked Chrome updates as PHP backdoors.
Microsoft has told BleepingComputer that they have fixed the issue for cloud-connected users and working on a fix for everyone else.
“We are working to resolve an issue where some customers may have experienced a series of false-positive detections. This issue has been resolved for cloud-connected customers.” – a Microsoft spokesperson.
Update 11/30/21: Added Microsoft’s statement.