KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






UPDATE: An update has been added to the article reflecting concerns security researchers have with the report.
An advanced hacking group is actively targeting biomanufacturing facilities with a new custom malware called ‘Tardigrade.’
The actor uses the custom malware to spread in compromised networks and exfiltrates data for extensive periods without being noticed.
According to an advisory published by Bioeconomy Information Sharing and Analysis Center (BIO-ISAC) today, the actor has been actively targeting entities in the field since the Spring of 2021.
Also Read: 5 Signs On How to Know if Ransomware is on Your Computer
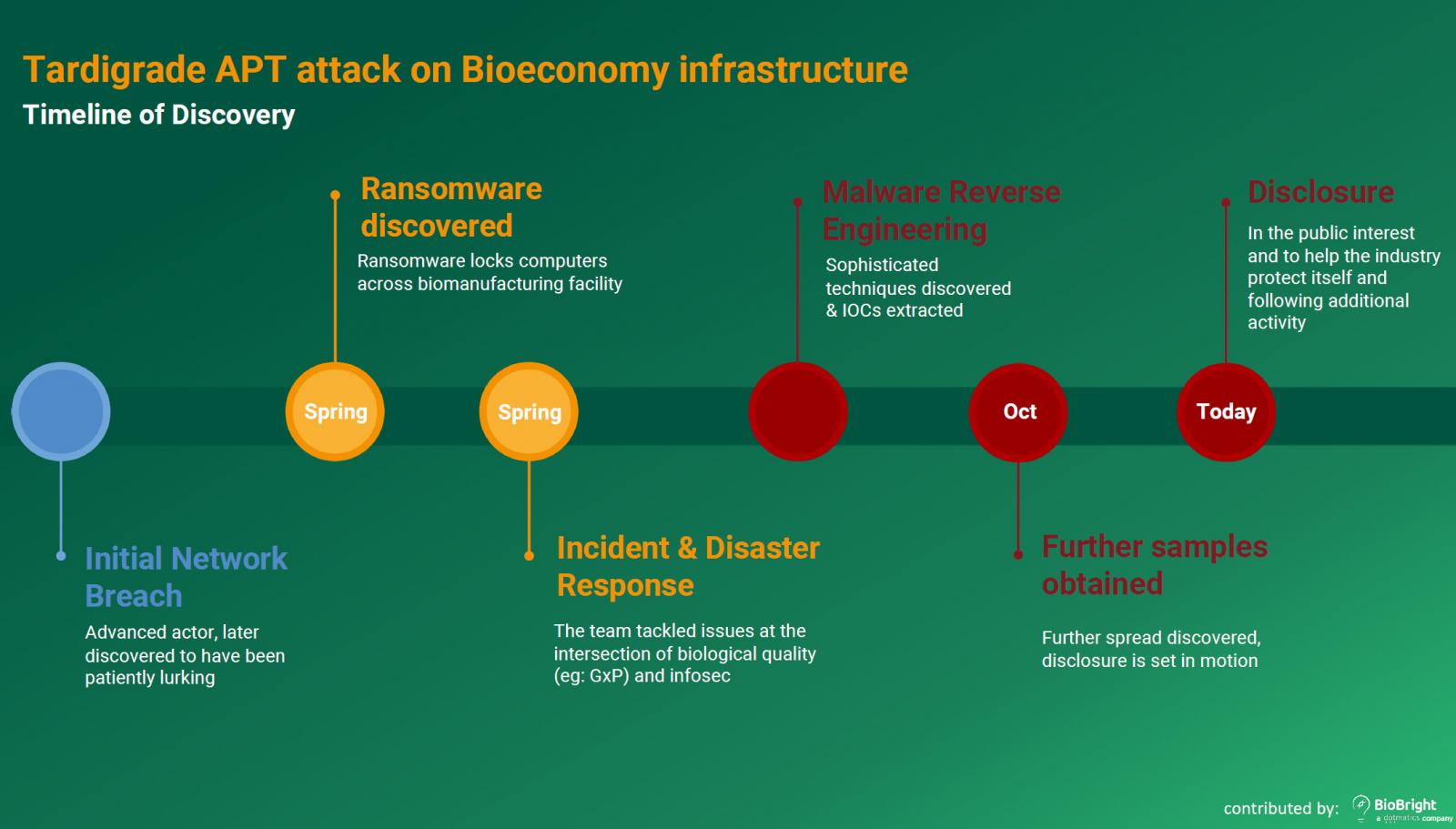
BIO-ISAC member BioBright told Wired that the first noticeable signs of these attacks came in the form of peculiar ransomware infections, where the actors left ransom notes that didn’t indicate a sincere interest in receiving any payments.
The purpose of these ransomware deployments was likely to conceal the drop of the actual payload, a metamorphic malware that would nest in the compromised systems, spread like a worm, and exfiltrate files.
BIO-ISAC explains that the threat actors use a custom metamorphic version of ‘SmokeLoader’ named ‘Tartigrade,’ that is delivered via phishing or USB sticks that somehow found their way on the premises of the target organizations.
The malware is particularly interesting in the sense that it can recompile the loader from memory without leaving a consistent signature, so it’s a lot harder to identify, trace, and remove.
The SmokeLoader acts as a stealthy entrance point for the actors, downloading more payloads, manipulating files, and deploying additional modules.
Past SmokeLoader versions relied heavily on external direction, but this variant can operate autonomously and even without a C2 connection.
Even if the C2 is down, the malware continues to move laterally based on internal logic and advanced decision-making abilities, even having the ability to selectively identify files for modification.
Also Read: How COVID-19 Contact Tracing in Singapore Applies at Workplace
As of October 25, 2021, BIO-ISAC reports that SmokeLoader can stay hidden from roughly half of the AV engines used in Virus Total.
The goal of the threat actors is cyber-espionage and possibly also operational disruption, but their malware can be a persistent problem for the infected systems even if it can no longer communicate with command and control servers.
The BIO-ISAC report recommends the following practices to following standard network segmentation practices, keeping offline backups of key biological infrastructure, and inquiring about lead times for critical bio-infrastructure components.
Using security software with strong behavioral analysis capabilities is recommended, so even if SmokeLoader changes signature and exfiltration methods, the suspicious behavior could be detected and raise alarms.
At this time, the attribution remains unclear, so the origin of these attacks is unknown.
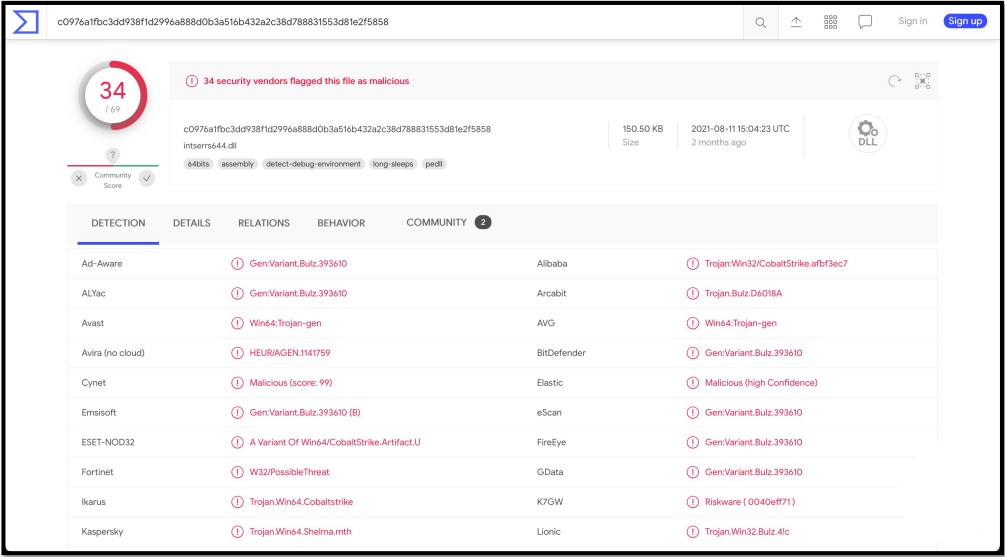
After publishing this article, BleepingComputer was contacted by security researchers who were concerned about the veracity of BIO-ISAC’s report and the technical data presented within it.
As part of the report, BIO-ISAC linked to a intserrs644.dll file submitted to VirusTotal and indicated that this was the new Tardigrade malware loader based on SmokeLoader.
However, Advanced Intel’s Vitali Kremez and other researchers who have spoken to BleepingComputer state that this DLL is actually a Cobalt Strike HTTP beacon packed using Conti’s crypter, and has no relation to SmokeLoader.
BleepingComputer has emailed BIO-ISAC and BioBright with questions about sample shared in the report and have not heard back at this time.
Update 11/23/21: Updated story with clarifications from BioBright that the malware is named ‘Tartigrade’ and that their included timeline of attacks are not those attributed to the threat actor. We have revised our story accordingly.
A new section has also been added with concerns security researchers have regarding the report.