KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Proof-of-concept exploit code has been released online over the weekend for an actively exploited high severity vulnerability impacting Microsoft Exchange servers.
The security bug tracked as CVE-2021-42321 impacts on-premises Exchange Server 2016 and Exchange Server 2019 (including those used by customers in Exchange Hybrid mode) and was patched by Microsoft during this month’s Patch Tuesday.
Successful exploitation allows authenticated attackers to execute code remotely on vulnerable Exchange servers.
On Sunday, almost two weeks after the CVE-2021-42321 patch was issued, researcher Janggggg published a proof-of-concept exploit for the Exchange post-auth RCE bug.
“This PoC just pop mspaint.exe on the target, can be use to recognize the signature pattern of a successful attack event,” the researcher said.
Also read: What is Pentest Report? Here’s A Walk-through
“We are aware of limited targeted attacks in the wild using one of the vulnerabilities (CVE-2021-42321), which is a post-authentication vulnerability in Exchange 2016 and 2019,” Microsoft said.
“Our recommendation is to install these updates immediately to protect your environment,” the company said, urging Exchange admins to patch the bug exploited in the wild.
If you haven’t yet patched this security vulnerability in your on-premises servers, you can generate a quick inventory of all Exchange servers in your environment that need updating using the latest version of the Exchange Server Health Checker script.
To check if any of your vulnerable Exchange servers have already been hit by CVE-2021-42321 exploitation attempts, you have to run this PowerShell query on each Exchange server to check for specific events in the Event Log:
Get-EventLog -LogName Application -Source "MSExchange Common" -EntryType Error | Where-Object { $_.Message -like "*BinaryFormatter.Deserialize*" }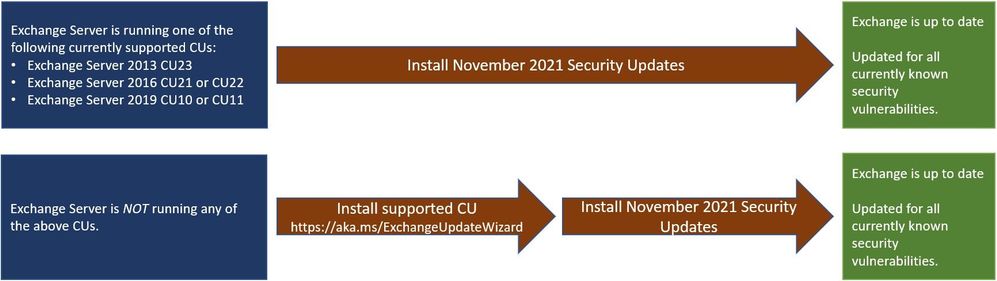
Exchange admins have dealt with two massive waves of attacks since the start of 2021, targeting the ProxyLogon and ProxyShell security vulnerabilities.
State-backed and financially motivated threat actors used ProxyLogon exploits to deploy web shells, cryptominers, ransomware, and other malware starting with early March.
In these attacks, they targeted more than a quarter of a million Microsoft Exchange servers, belonging to tens of thousands of organizations around the world.
Four months later, the US and its allies, including the EU, the UK, and NATO, officially blamed China for these widespread Microsoft Exchange hacking attacks.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
In August, threat actors also began scanning for and breaching Exchange servers by exploiting ProxyShell vulnerabilities after security researchers reproduced a working exploit.
Even though payloads dropped using ProxyShell exploits were harmless in the beginning, attackers later switched to deploying LockFile ransomware payloads across Windows domains hacked using Windows PetitPotam exploits.
With this latest vulnerability (CVE-2021-42321), researchers are already seeing attackers scan for and attempt to compromise vulnerable systems.
As Microsoft Exchange has become a popular target for threat actors to gain initial access to a targets’ networks, it is strongly advised to keep servers up-to-date with the latest security patches.