KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are hacking Microsoft Exchange servers using ProxyShell and ProxyLogon exploits to distribute malware and bypass detection using stolen internal reply-chain emails.
When threat actors conduct malicious email campaigns, the hardest part is to trick users into trusting the sender enough so that they open up linked to or included malware-distributing attachments.
TrendMicro researchers have discovered an interesting tactic used of distributing malicious email to a company’s internal users using the victim’s compromised Microsoft exchange servers.
The actors behind this attack are believed to be ‘TR’, a known threat actor who distributes emails with malicious attachments that drop malware, including Qbot, IcedID, Cobalt Strike, and SquirrelWaffle payloads.
Also Read: CCTV Law Singapore Edition: Know Your Rights and Responsibilities
As a way to trick corporate targets into opening malicious attachments, the threat actor exploits Microsoft Exchange servers using the ProxyShell and ProxyLogon vulnerabilities.
The threat actors then uses these compromised Exchange servers to reply to the company’s internal emails in reply-chain attacks containing links to malicious documents that install various malware.
“In the same intrusion, we analyzed the email headers for the received malicious emails, the mail path was internal (between the three internal exchange servers’ mailboxes), indicating that the emails did not originate from an external sender, open mail relay, or any message transfer agent (MTA),” explains Trend Micro’s report.
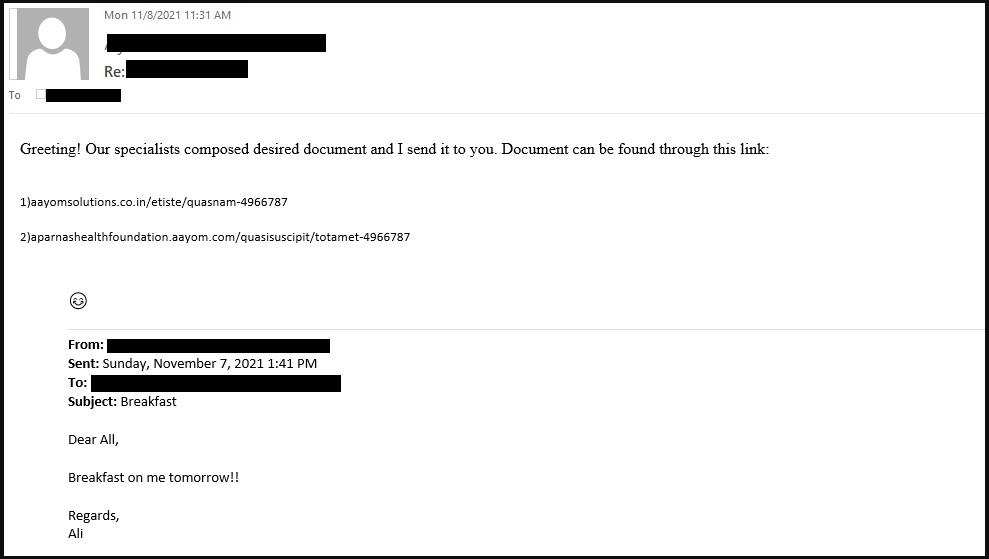
As these emails originate from the same internal network and appear to be a continuation of a previous discussion between two employees, it leads to a greater degree of trust that the email is legitimate and safe.
Not only is this effective against the human recipients, but it’s also excellent for not raising any alarms on the email protection systems used in the target firm.
The attachments that come or are linked to by these emails are your standard malicious Microsoft Excel templates that tell recipients to ‘Enable Content’ to view a protected file.
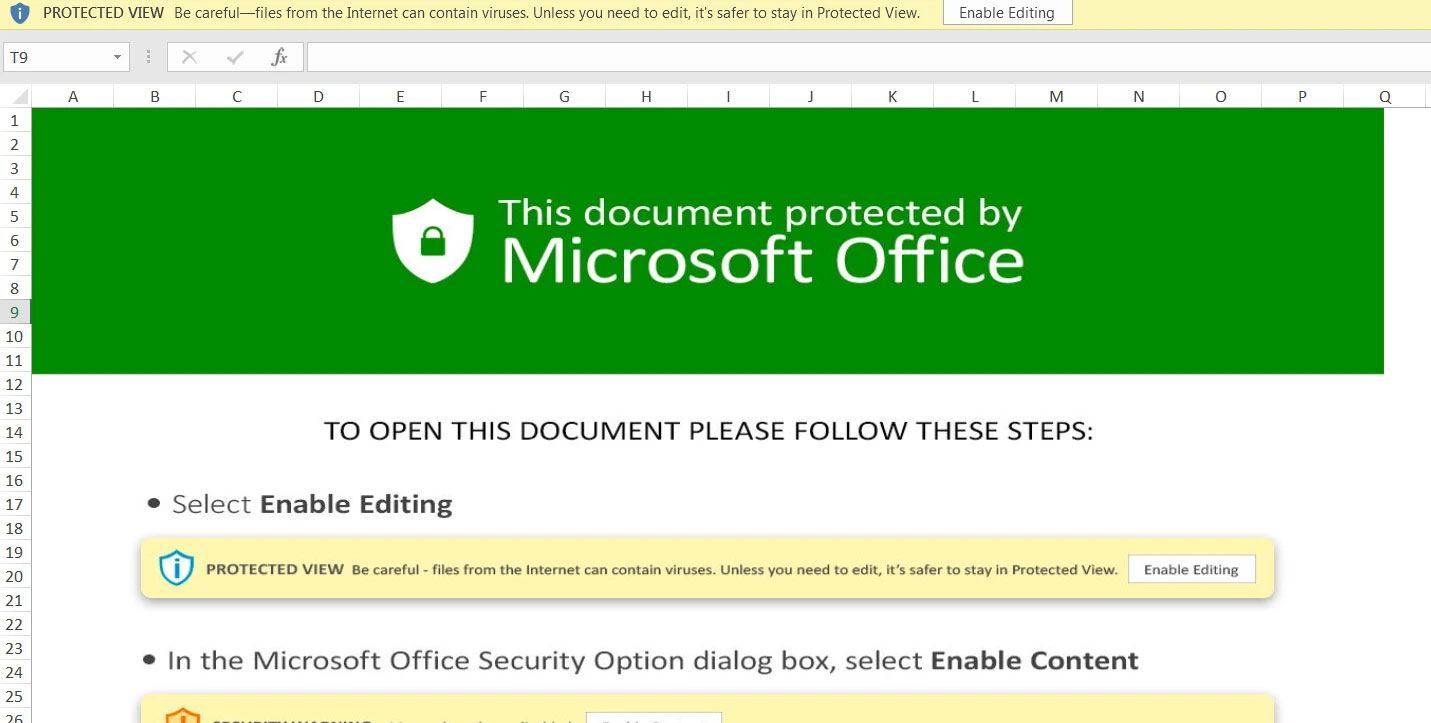
However, once the user enables content, malicious macros are executed to download and install the malware distributed by the attachment, whether that be Qbot, Cobalt Strike, SquirrelWaffle, or another malware.
According to Trend Micro’s report, the researchers said that they have seen these attacks distribute the SquirrelWaffle loader, which then installs Qbot.
However, Cryptolaemus researcher ‘TheAnalyst‘ says that the malicious document used by this threat actor drop both malware as discrete payloads, rather than SquirrelWaffle distributing Qbot.
Microsoft has fixed the ProxyLogon vulnerabilities in March and the ProxyShell vulnerability in April and May, addressing them as zero-days at the time.
Threat actors have abused both vulnerabilities to deploy ransomware or install webshells for later backdoor access. The ProxyLogon attacks got so bad that the FBI removed web shells from compromised US-based Microsoft Exchange servers without first notifying the servers’ owners.
After all this time and the wide media these vulnerabilities have received, not patching Exchange Servers is just an open invitation to hackers.