KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







There’s some unusual activity brewing on Russian-speaking cybercrime forums, where hackers appear to be reaching out to Chinese counterparts for collaboration.
These attempts to enlist Chinese threat actors are mainly seen on the RAMP hacking forum, which is encouraging Mandarin-speaking actors to participate in conversations, share tips, and collaborate on attacks.
Also Read: The Importance Of DPIA And Its 3 Types Of Processing
According to a new report by Flashpoint, high-ranking users and RAMP administrators are now actively attempting to communicate with new forum members in machine-translated Chinese.
The forum has reportedly had at least thirty new user registrations that appear to come from China, so this could be the beginning of something notable.
The researchers suggest that the most probable cause is that Russian ransomware gangs seek to build alliances with Chinese actors to launch cyber-attacks against U.S. targets, trade vulnerabilities, or even recruit new talent for their Ransomware-as-a-Service (RaaS) operations.
A threat analyst told BleepingComputer earlier this month that this initiative was started by a RAMP admin known as Kajit, who claims to have recently spent some time in China and can speak the language.
In the prior version of RAMP, he had intimated that he would be inviting Chinese threat actors to the forum, which appears to now be taking place.
However, Russian hackers attempting to collaborate with Chinese threat actors is not limited to the RAMP hacking forum as Flashpoint has also seen similar collaboration on the XSS hacking forum.
“In the screenshot below, XSS user “hoffman” greets two forum members who revealed themselves as Chinese,” explains the new research by Flashpoint.
Also Read: Does Personal Data Market About To Become The Next Big Thing
“The threat actor asks them if they could provide information about ransomware and purchasing various kinds of system vulnerabilities. The language seems to be machine-translated Chinese.”
.png)
Based on prior history related to RAMP admins, Flashpoint underlines that there’s always the possibility of this being simply a smokescreen, with no real Chinese users having joined RAMP.
Last month, a RAMP admin known as ‘Orange’ or ‘boriselcin’ and who ran the “Groove” site, published a post calling on threat actors to attack the USA.
After the media covered this post, including BleepingComputer, the Groove actor claimed that the operation was fake from the beginning and was created to troll and manipulate the media and security researchers.
Security researchers from McAfee and Intel 471 believe that this is likely just the threat actor trying to cover up the fact that the actor’s attempted ransomware-as-a-service did not work as planned.
Due to this, the RAMP admin’s prior actions require us to treat anything they say with some skepticism.
However, the Conti ransomware operation recently posted to the RAMP forum to recruit affiliates and buy initial access to networks. In a screenshot shared with BleepingComputer, the gang says they normally only work with Russian-speaking hackers but are making an exception for Chinese-speaking threat actors out of respect for the RAMP admin.
“This ad is in Russian, because we only work with Russian speakers. BUT, out of respect for the admin, we will make an exception for Sino-speaking users and even translate this message in Chinese (you can even duplicate it in Mandarin and Canotonese!)”- Conti ransomware operation.
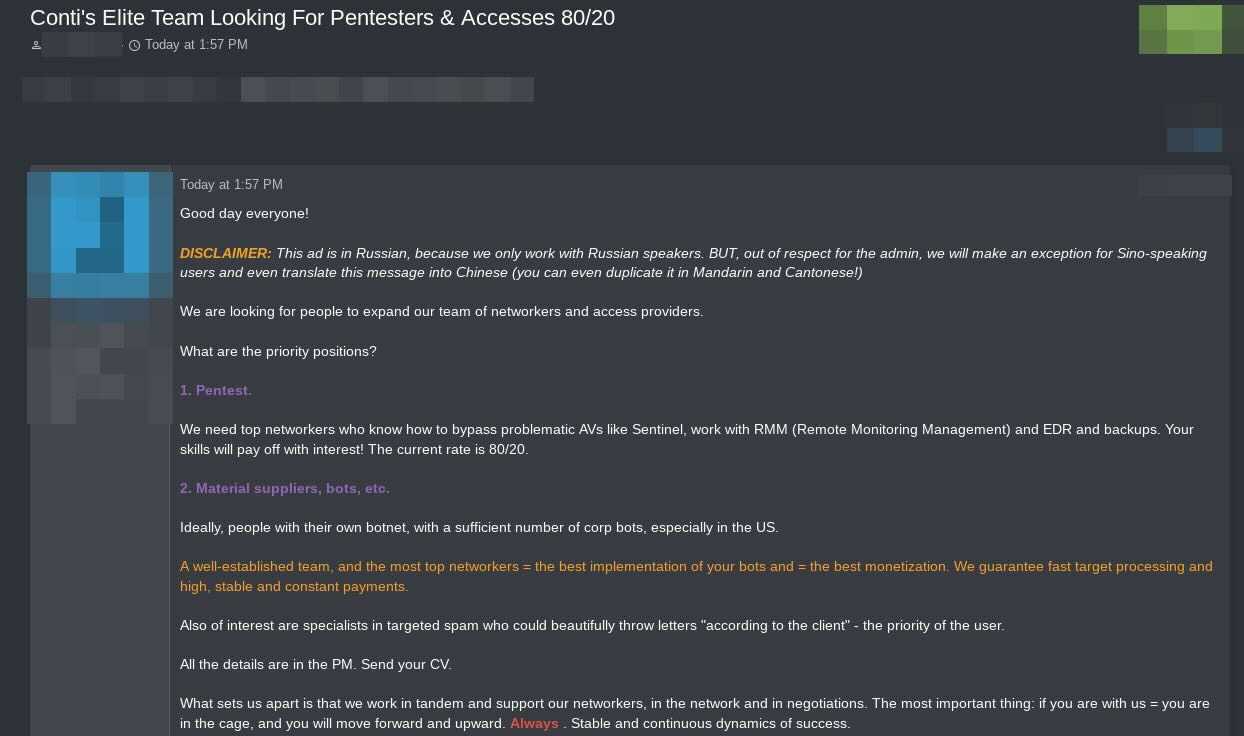
As such, it does appear that the RAMP forum is actively inviting Chinese-speaking threat actors to participate in conversations and attacks.
Now that RAMP is back online, it appears to be steadily growing, despite the DDOSing waves it had sustained soon after its launch.
RAMP was set up last summer by a core member of the original Babuk ransomware gang, aiming to serve as a new place to leak valuable data stolen from cyberattacks and recruit ransomware affiliates.
A notable case of such a leak came in September when a RAMP admin posted 498,908 Fortinet VPN credentials to access 12,856 devices on various corporate networks.
While many of these credentials were old, security researchers stated that many of the credentials were still valid and allowed the RAMP forum to build a reputation in the field.
Flashpoint reports that RAMP has reached its third iteration, using a new .onion domain and is requiring all former users to re-register.
Update 11/17/21: This article originally said that members do not need to verify themselves. This was a temporary situation, and they still need verification.