KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







While mostly hidden in private conversations, details sometimes emerge about the parallel economy of vulnerability exploits on underground forums, revealing just how fat of a wallet some threat actors have.
Some adversaries claim multi-million U.S. dollar budgets for acquiring zero-day exploits but those that don’t have this kind of money may still have a chance to use zero-days if a new ‘exploit-as-a-service’ idea becomes reality.
The dialog about vulnerabilities, both old and new, on cybercriminal communities sometimes includes offers to buy exploits for big money.
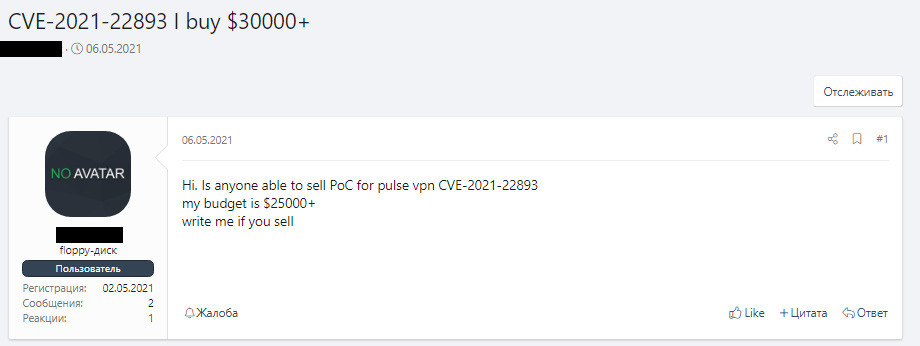
One forum user in early May offered $25,000 for proof-of-concept (PoC) exploit code for CVE-2021-22893, a critical-severity vulnerability in Pulse Secure VPN that had been leveraged by Chinese hackers since at least April.
Also Read: How To Make Effective Purchase Order Template Singapore
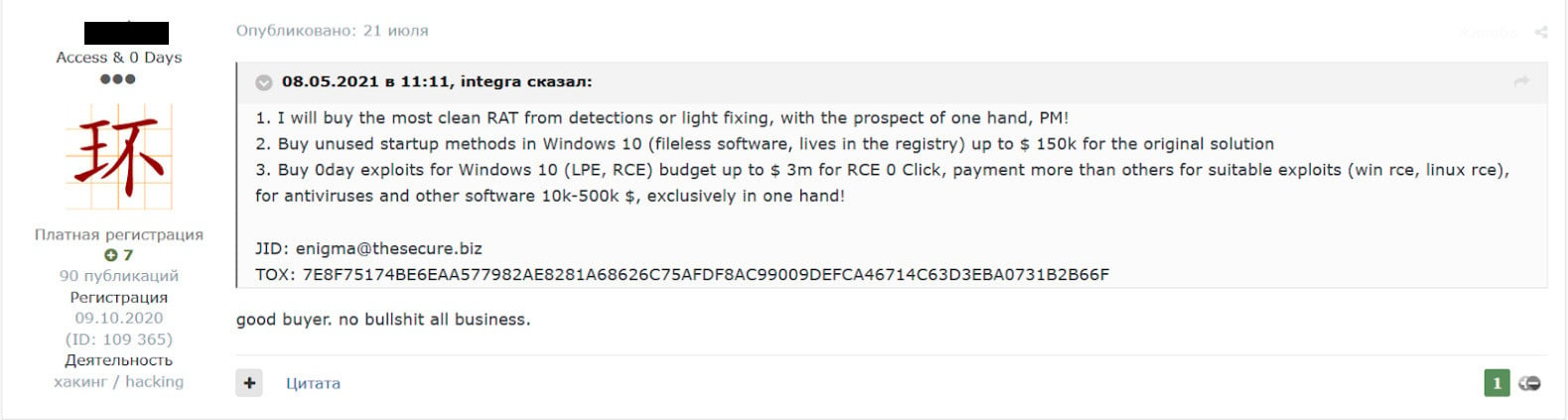
Another actor with deeper pockets claimed a budget of up to $3 million for no-interaction remote code execution (RCE) bugs, the so-called zero-click exploits, for Windows 10 and Linux.
The same user offered up to $150,000 for original solutions for “unused startup methods in Windows 10” so malware would be active every time the system booted.
By comparison, exploit acquisition company Zerodium offers up to $1 million for a zero-click RCE in Windows 10. The highest payout from the broker is up to $2.5 million for a zero-click full-chain persistence in Android, followed by $2 million for the iOS equivalent.
The posts were captured by researchers at risk protection company Digital Shadows, who looked at threat actors’ activity to take advantage of security weaknesses.
During the investigation, they observed some actors engaged in talks about zero-day prices as high as $10 million.
The researchers note that such prices are no longer restricted to nation-state hackers and that cybercriminals, particularly ransomware groups, can also afford them.
Completing a big sale, though, is not easy and may take a long time. If it takes too long, developers may lose the chance to make big money because competitors may come up with an exploit variant, dragging down the price.
For this reason, cybercriminals are now discussing an “exploit-as-a-service” solution that would allow exploit developers to rent out a zero-day exploit to multiple parties.
This alternative could generate huge profits to zero-day exploit developers, while they wait for a definitive buyer, the researchers say.
“Additionally, with this model, renting parties could test the proposed zero-day and later decide whether to purchase the exploit on an exclusive or non-exclusive basis” – Digital Shadows
Just like in the case of malware-as-as-service, renting out the exploits would let less-skilled adversaries deploy more complex attacks and hit more valuable targets.
Also Read: NDA Data Protection: The Importance, Its Meaning And Laws
The report from Digital Shadows highlights that adversaries, financially motivated cybercriminals or state-sponsored hackers, are quick to integrate new attack methods and are constantly looking for new exploit code.
“This scene is bursting with a variety of widespread actors who boast a whole range of technical expertise and motives” – Digital Shadows
Users of various skill levels share knowledge and tools to improve their attacks and build stronger relationships that could prove lucrative in the longer run.
Some users stand out in these communities because of the dialog they generate either on the public or private face of the forum on vulnerability exploitation.
Digital Shadows researchers categorized some of them, admitting that “there can be major crossover” between them:
Threat actor communities are highly active and deeply connected to the infosec technical literature, striving to come up with new attack methods that would give them access to bigger targets.
They are not necessarily looking for new vulnerabilities, although these are the most coveted, but also explore older bugs that did not receive enough attention and could be exploited.