KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Microsoft has introduced an AI-driven ransomware attack detection system for Microsoft Defender for Endpoint customers that complements existing cloud protection by evaluating risks and blocking actors at the perimeter.
As human-operated ransomware attacks are characterized by a specific set of methods and behaviors, Microsoft believes that they can use a data-driven AI approach to detect these types of attacks.
Attackers typically establish a foothold in the target system by planting a malware binary that provides remote access to the device.
However, not all binaries used in attacks are known to be malicious, and many executables used in attacks are legitimate programs, including built-in Windows commands.
Also Read: PDPA Compliance for MCST: The importance of hiring a DPO
Indicators generated by these binaries may be seen as low priority and ignored by defenders.
Adding an AI-driven adaptive protection system that would detect unusual behavior, even from legitimate binaries, can play a crucial role in preventing further compromise on a device and provide responding teams valuable time to thwart the attacks.
“In a customer environment, the AI-driven adaptive protection feature was especially successful in helping prevent humans from entering the network by stopping the binary that would grant them access,” explained Microsoft about their AI-driven defense system.
“By considering indicators that would otherwise be considered low priority for remediation, adaptive protection stopped the attack chain at an early stage such that the overall impact of the attack was significantly reduced.”
“The threat turned out to be Cridex, a banking trojan commonly used for credential theft and data exfiltration, which are also key components in many cyberattacks including human-operated ransomware.”
Contrary to cloud protection which admins manually adjust, the new system is adaptive, which means that it can automatically ramp the aggressiveness of cloud-delivered blocking verdicts up and down, based on real-time data and machine learning predictions.
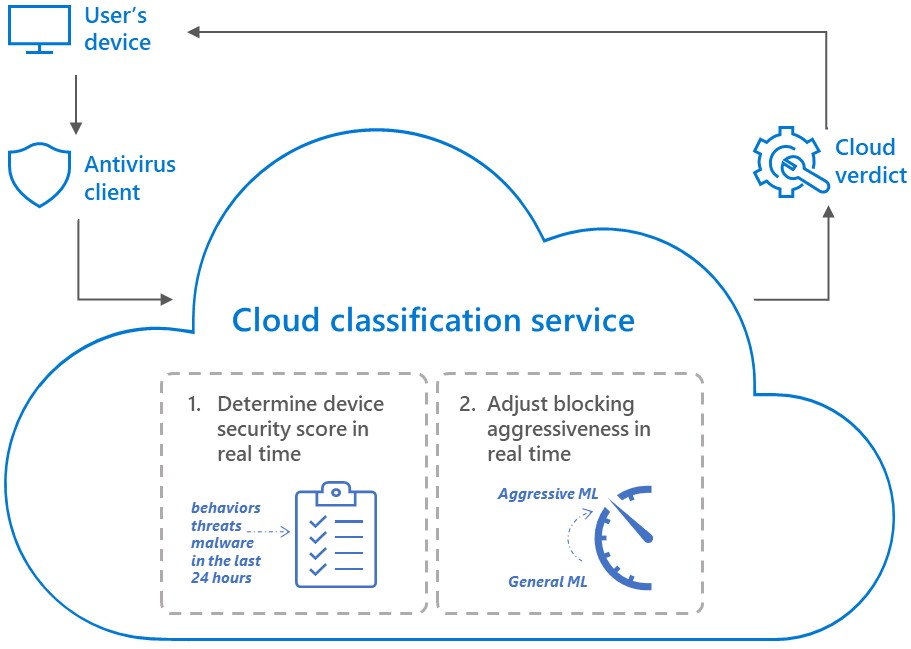
Even if the algorithm fails to evaluate the risk at its real magnitude and a ransomware actor finds a way into the target network, the system will remain an obstacle for them.
Also Read: Spam Control Act: 4 best practices organizations must consider
As Microsoft explains, adaptive protection can detect and block seemingly benign operations such as network enumeration, which ransomware actors use during the reconnaissance phase.
Similarly, open-source tools are commonly abused for lateral movement, or slightly modified commodity malware that doesn’t have an identifiable signature can be detected and blocked.
“Hypothetically, in attacks where early to mid-stage attack activities are not detected and blocked, AI-driven adaptive protection can still demonstrate huge value when it comes to the final ransomware payload.” Microsoft explains
“Given the device is already compromised, our AI-driven adaptive protection system can easily and automatically switch to the most aggressive mode and block the actual ransomware payloads, preventing important files and data from being encrypted so attackers won’t be able to demand ransom for them.”
As defensive mechanisms become more sophisticated, actors are far more likely to attempt to deactivate them instead of trying to evade or circumvent them.
This means that admins should be checking the status of their defensive tools regularly, ensuring that they are always up and running.
Cloud protection is turned on by default, and the AI-driven enhancement is now automatically included in Microsoft Defender for Endpoints as an “always-on” feature.
If any of these features are now disabled, admins should immediately investigate further to determine if they have been compromised.