KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has seen a surge in malware campaigns using HTML smuggling to distribute banking malware and remote access trojans (RAT).
While HTML smuggling is not a new technique, Microsoft is seeing it increasingly used by threat actors to evade detection, including the Nobelium hacking group behind the SolarWinds attacks.
HTML smuggling is a technique used in phishing campaigns that use HTML5 and JavaScript to hide malicious payloads in encoded strings in an HTML attachment or webpage. These strings are then decoded by a browser when a user opens the attachment or clicks a link.
For example, a phishing HTML attachment could include a harmless link to a known website, thus not being seen as malicious. However, when a user clicks on the link, JavaScript will decode an included encrypted or encoded string and convert it into a malicious attachment that is downloaded instead, as shown in the code below.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
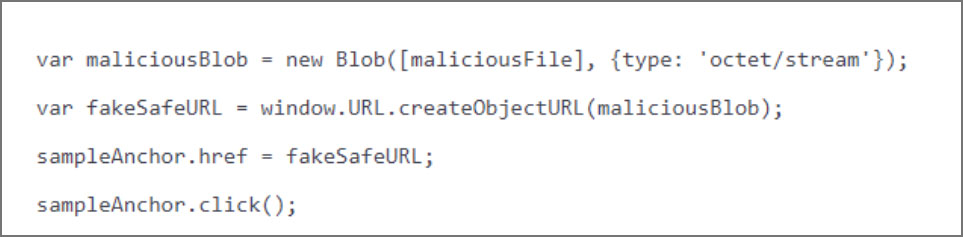
Since the malicious payload is encoded initially, it looks harmless to security software and is not detected as malicious. Furthermore, as JavaScript assembles the payload on the target system, it bypasses any firewalls and security defenses that would usually catch the malicious file at the perimeter.
.jpg)
Microsoft researchers have seen this technique used in Mekotio campaigns that deliver banking trojans and also in highly-targeted NOBELIUM attacks.
HTML smuggling campaigns are also used to drop the AsyncRAT or NJRAT remote access trojans, or the TrickBot trojan used to breach networks and deploy ransomware.
Also Read: The DNC Singapore: Looking At 2 Sides Better
The attacks usually start with a phishing email containing an HTML link in the body of the message or a malicious HTML file as an attachment.
If either is clicked, a ZIP file is dropped using HTML smuggling. This archive contains a JavaScript file downloader that fetches additional files from a command and control server (C2) to install on the victim’s device.
In some cases, the created archives are password-protected for additional detection evasion against endpoint security controls. However, the password to open it is provided in the original HTML attachment, so the victim must enter it manually.
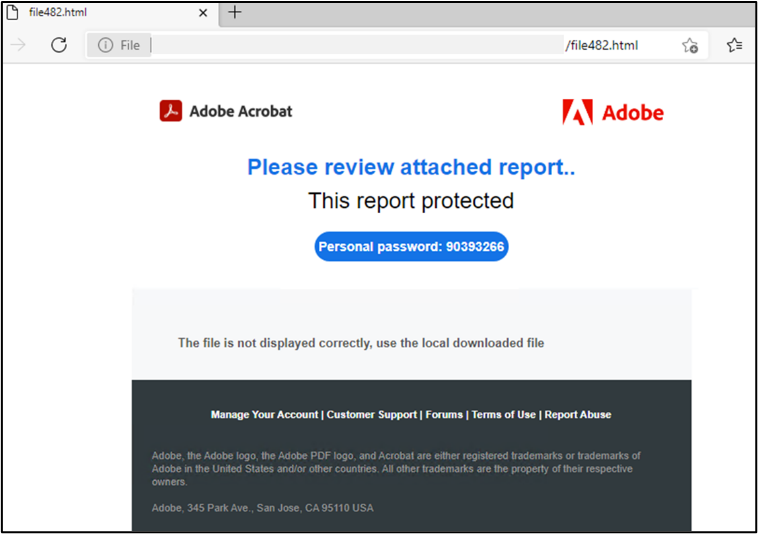
Once the script is launched, a base64-encoded PowerShell command is executed that downloads and installs the TrickBot trojan or other malware.
A 2020 report from Menlo Security also mentions the Duri malware group as one of the actors who actively uses HTML smuggling for payload distribution, but the technique was first seen in the wild since at least 2018.
Microsoft first warned about a sudden uptick in this activity in July 2021, urging admins to raise their defenses against it.
Microsoft suggests admins use behavior rules to check for commonly characteristics of HTML smuggling, including:
For endpoints, admins should block or audit activity associated with HTML smuggling, including:
In addition to the above, users may prevent automatic JavaScript code execution by associating .js and .jse files with a text editor like Notepad.
Ultimately, the best defense is to train users not to open files downloaded via links in emails and attachments. All files downloaded from an email should be treated with caution and checked carefully before being opened.
Furthermore, if an attachment or email link downloads an attachment ending with a .js extension (JavaScript), it should never be opened and automatically be deleted.
Unfortunately, Windows disables the showing of file extensions by default, leading to extensions not being seen in many cases. This is why it is always suggested that users enable the viewing of file extensions to prevent the opening of malicious files.