KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Contestants hacked the Samsung Galaxy S21 smartphone during the second day of the Pwn2Own Austin 2021 competition, as well as routers, NAS devices, speakers, and printers from Cisco, TP-Link, Western Digital, Sonos, Canon, Lexmark, and HP.
So far, Trend Micro’s Zero Day Initiative has awarded $777,500 over the first two days of Pwn2Own Austin, with $415,000 awarded during the second day and $362,500 won during the first day.
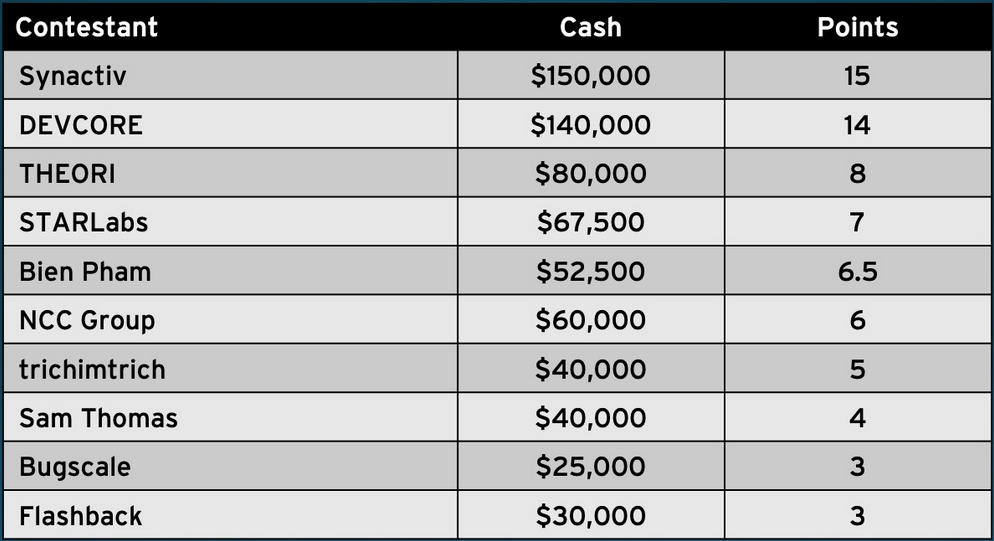
The Synacktiv team maintains a slight lead in the Master of Pwn standings with 15 Master of Pwn points and $150,000 won so far, one point ahead of the DEVCORE team that has 14 points and has earned $140,000.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
The full Pwn2Own Austin 2021 schedule and the results following each challenge are available here.
Yesterday, Mr L and Nguyễn Hoàng Thạch (@hi_im_d4rkn3ss) of STARLabs were able to get code execution on the Samsung Galaxy S21 running the latest Android 11 security updates.
However, despite successfully exploiting a zero-day flaw, the attempt was tagged as a “collision” after it was revealed in the disclosure room that they used a bug known to the vendor.
They still earned $25,000 and 2.5 Master of Pwn points, reaching a total of $75,000 in awards after the first two days of competition.
Samsung Galaxy S21 was also the only device that wasn’t compromised on the first day after F-Secure Labs’ Ken Gannon couldn’t get his zero-day exploit to work within the allotted time.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
At this edition of Pwn2Own (previously known as Pwn2Own Mobile), security researchers are targeting mobile phones, printers, routers, network-attached storage (NAS), smart speakers, TVs, external storage, and other devices, all up to date and in their default configuration.
The only exception to this rule is Western Digital’s 3TB My Cloud Home Personal Cloud NAS device, which still runs a beta software release.
The highest rewards are for devices in the mobile phone category, with cash prizes of up to $150,000.
Researchers can also get a $50,000 bonus if their iPhone or Pixel browser exploits will execute with kernel-level privilege, taking the maximum award for a single challenge to a total of $200,000.
This edition of Pwn2Own Austin’s consumer-focused event is also the first one to be extended to four days after 22 different contestants registered for 58 total entries.