KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







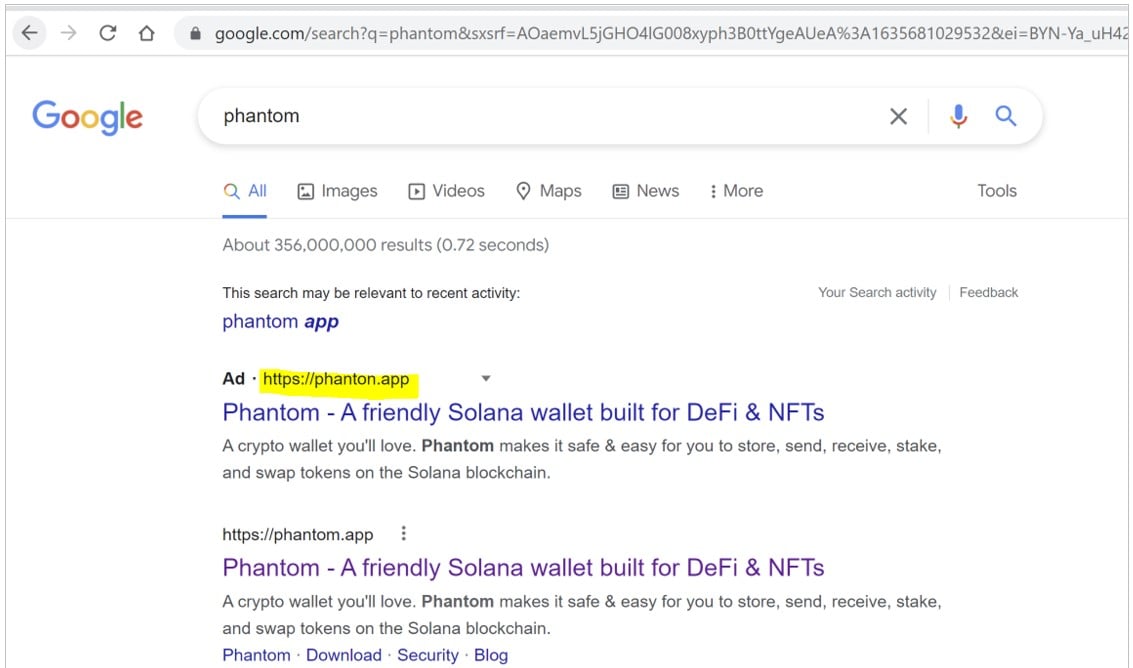
Threat actors are using advertisements in Google Search to promote fake cryptocurrency wallets and DEX platforms to steal user’s cryptocurrency.
These advertisements promote sites that install fake Phantom and MetaMask wallets used for Solana and Ethereum, and fake decentralized exchange (DEX) platforms, such as PancakeSwap and Uniswap.
The deceptive operation is supported by cloned websites that look just like the real ones, so the visitors are convinced they are installing the legitimate wallet or using the correct platform.
Researchers at CheckPoint saw a surge in relevant scamming reports over the past weekend, with numerous ads tricking victims into visiting various typosquatted domains.
Also Read: The DNC Singapore: Looking At 2 Sides Better
The ads promote websites with slight, hard-to-notice differences compared to the official domains, like “phanton.app” or “phantonn.pw,” compared to the legitimate domain of “phantom.app”.
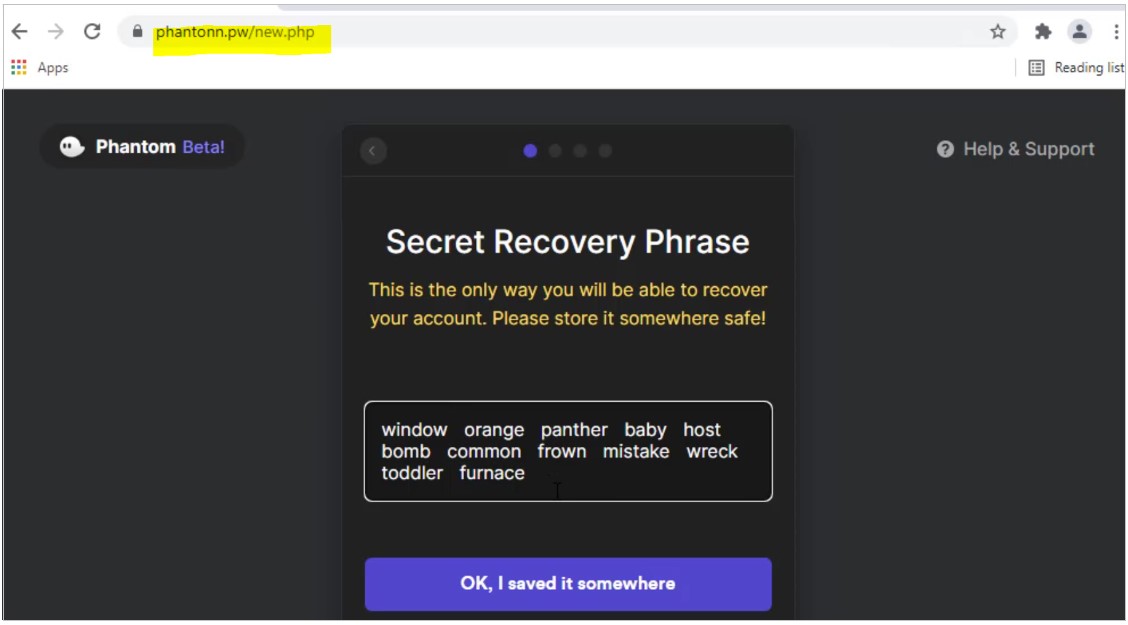
When visiting one of these fake Phantom sites, users will be prompted to create a new wallet, including writing down a recovery phrase used to restore the wallet and a password to access.
Anyone who has this information can add a wallet to their own system and access any cryptocurrency stored within it.
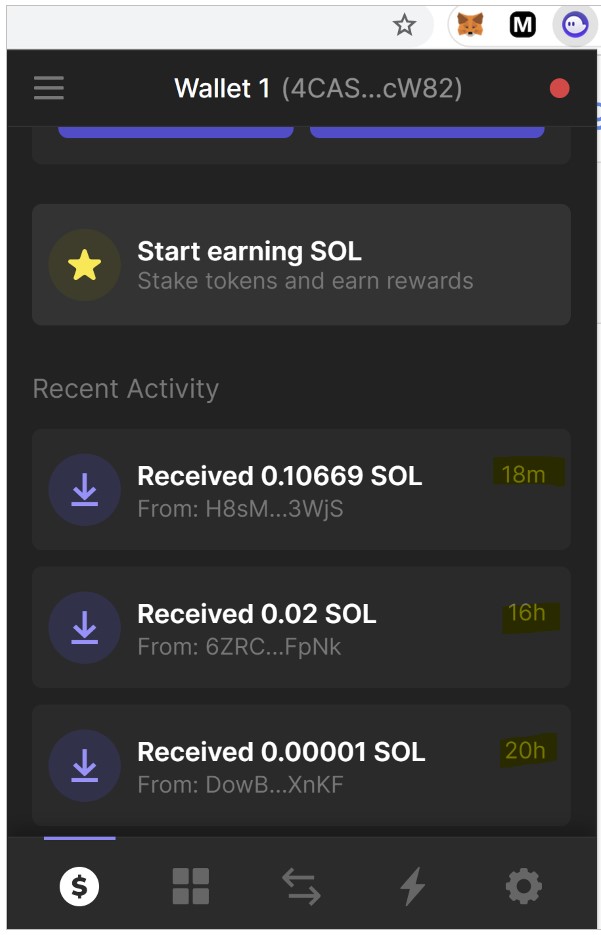
Once the victim finishes the setup process, they are redirected to the real Phantom wallet page, where they install the official Chrome plugin.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
Using the recovery phrase created by the attackers, they log in to the attacker’s wallet through the extension, thinking it’s theirs. Any cryptocurrency transferred into that wallet is now also accessible by the threat actors, who can transfer it to other wallets under their control.
CheckPoint discovered that the actors created several wallets under the same account, corresponding to multiple victims, and received notable amounts every couple of hours.
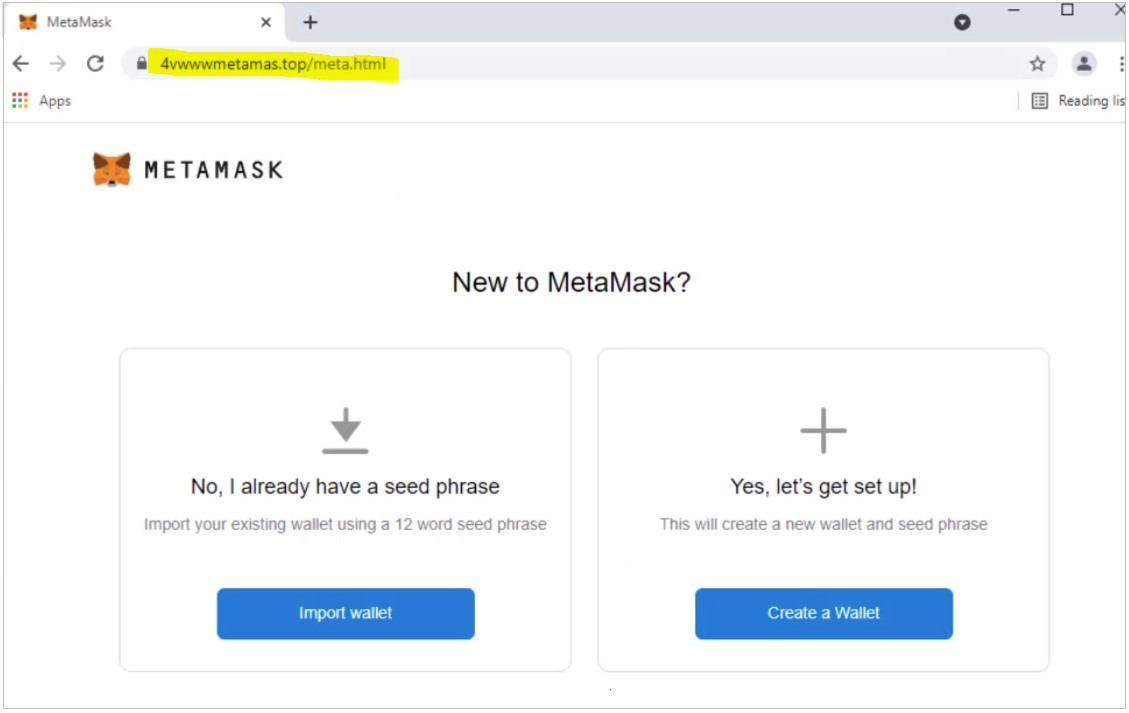
In a malicious advertising campaign that impersonates MetaMask, the actors aren’t only trying to divert Ethereum transactions to their wallets and target any assets the victims may already hold.
For this purpose, the cloned websites offer an additional “Import wallet” function, which is attempts to steal the victim’s private key, which is all that’s needed for the actors to take control of the wallet.
Similarly, the advertisements were also promoting fake decentralized exchanges, such as Uniswap that would prompt users to connect their wallet and enter their recovery phrase.
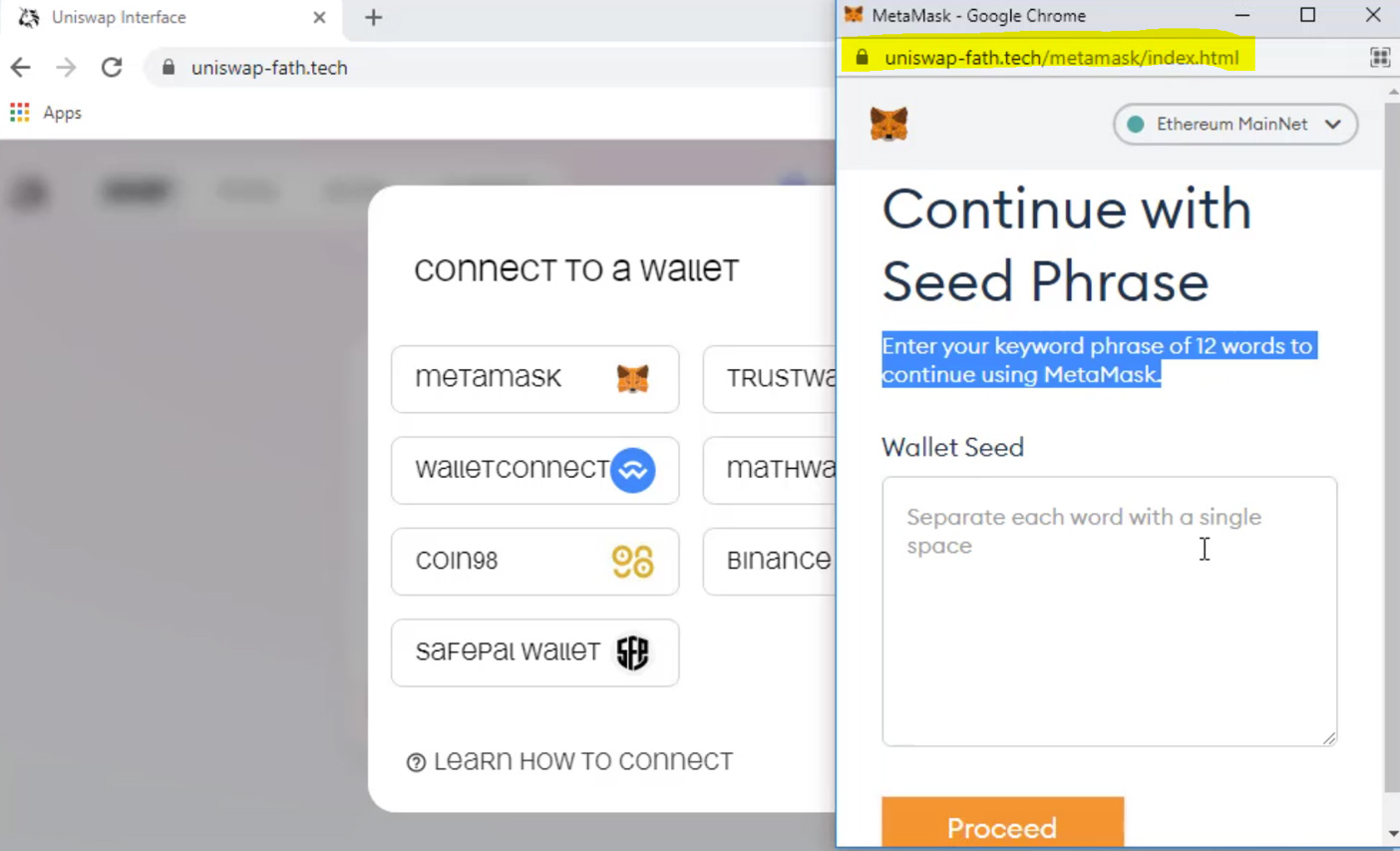
Like the MetaMask scam, once a user enters their recovery phrase, the threat actors would import the wallet into their own systems and its stored cryptocurrency.
While these advertisements have since been taken down by Google, there is nothing to say that new ones will not be added in the future.
For this reason, to keep your investments safe from these scams, you should follow these basic guidelines:
Unfortunately, if you fall for one of these scams, there is no way to recover cryptocurrency stolen in this manner. Therefore, you must pay close attention to the above guidelines to safeguard your funds and prevent them from being stolen.