KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Mobile phishing attacks targeting employees in the energy industry have risen by 161% compared to last year’s (H2 2020) data, and the trend is showing no signs of slowing down.
Although the perils of outdated and vulnerable devices plague all sectors, a new report by cybersecurity firm Lookout indicates that energy is the most targeted, followed by finance, pharma, government, and manufacturing.
In terms of geographic targeting, Asia-Pacific tops the list, followed by Europe and then North America. However, there is a rising trend in phishing attacks targeting the global energy industry across the world.
Also Read: Top 11 Ultimate Cold Calling Guidelines To Boost Your Sales
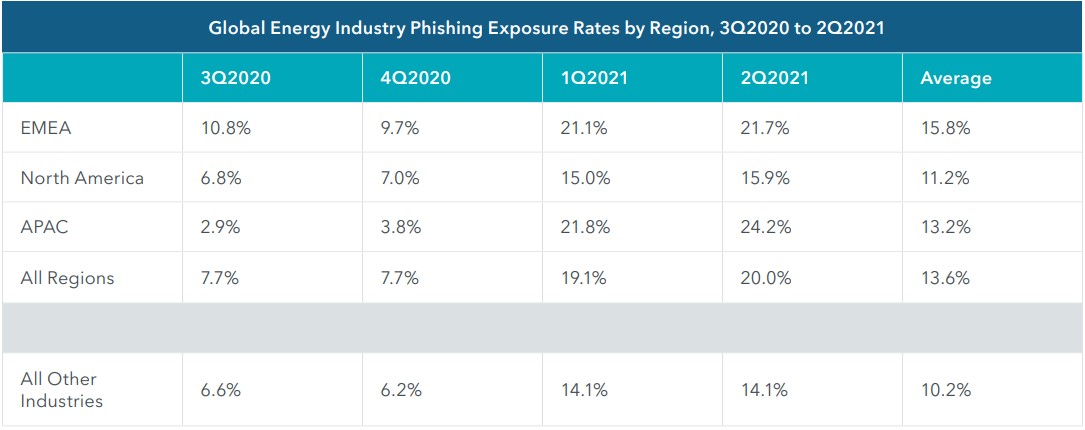
Mobile phishing also surged in the first half of 2021, with nearly 20% of all employees in the energy sector being targeted in mobile phishing attacks, leading to an increase of 161% over the previous six months.
With so many people working from home due to the COVID-19 pandemic, many employees use VPNs to access corporate networks. Unfortunately, this remote access to a corporate network makes for an attractive target for threat actors, who use phishing to steal VPN credentials or domain credentials.
In 67% of all analyzed phishing cases by Lookout researchers, threat actors are performing credential theft. To conduct these campaigns, the attackers employ email, SMS, phishing apps, and login pages at fake corporate sites.
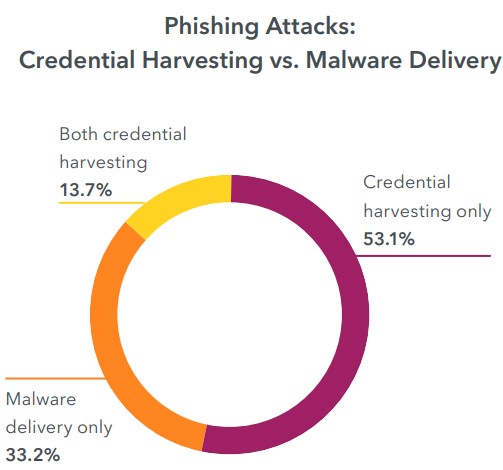
These credentials enable them to gain access to internal networks, which can then be used for further lateral movement and finding additional pivoting points.
From there, they can locate vulnerable systems and launch attacks against industrial control systems which typically carry unidentified flaws for years.
Also Read: IT Equipment Disposal Singapore and Recycle Services
According to the report from Lookout, the most significant attack surface stems from 56% of Android users running out-of-date and vulnerable versions of the OS.
“Outdated versions of Google and Apple operating systems are still in use across the energy industry. Old versions expose organizations to hundreds of vulnerabilities that can be exploited by bad actors seeking access to an organization’s environment,” explains the report from Lookout.
A full year after Android 11 was released, Lookout’s telemetry showed that only 44.1% of active Android devices were using it.
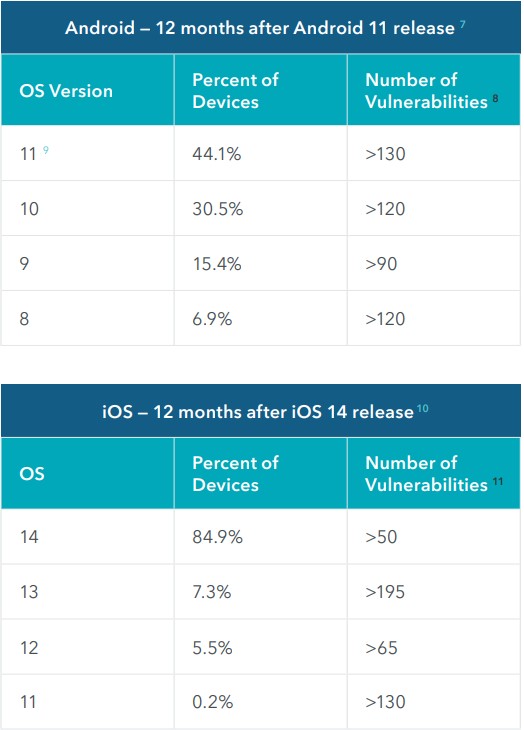
In contrast, iPhones are far less vulnerable to exploitation, as most iOS users are running the latest version.
Some of the flaws in older Android versions are easily exploitable and pretty across the entire user base.
For example, CVE-2020-16010 in Chrome can be trivially exploited through a specially crafted HTML page, and considering the browser’s popularity, would be exposed on all outdated Android phones.
Apps that request risky permissions and access sensitive data on the device are now a bigger problem than “pure” malware, as they are far easier to pass through app store vetting.
Many of these apps connect to obscure servers and send various types of data that are irrelevant to their core functionality but which still constitute a great risk to the user and their employing organization.
Spyware, keyloggers, trojans, and even ransomware droppers remain a problem, but it’s more likely to see these deployed in highly targeted attacks, so their distribution volumes are significantly smaller.
As such, employee training is critical in minimizing security lapses, as the human factor remains the greatest risk for installing riskware and the clicking/tapping of suspicious links.
Lookout reports that a single session of anti-phishing training results in 50% fewer clicks onto phishing links for the next 12 months.