KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






The Groove ransomware gang is calling on other extortion groups to attack US interests after law enforcement took down REvil’s infrastructure last week.
Over the weekend, BleepingComputer reported that the REvil ransomware operation shut down again after an unknown third party hijacked their dark web domains.
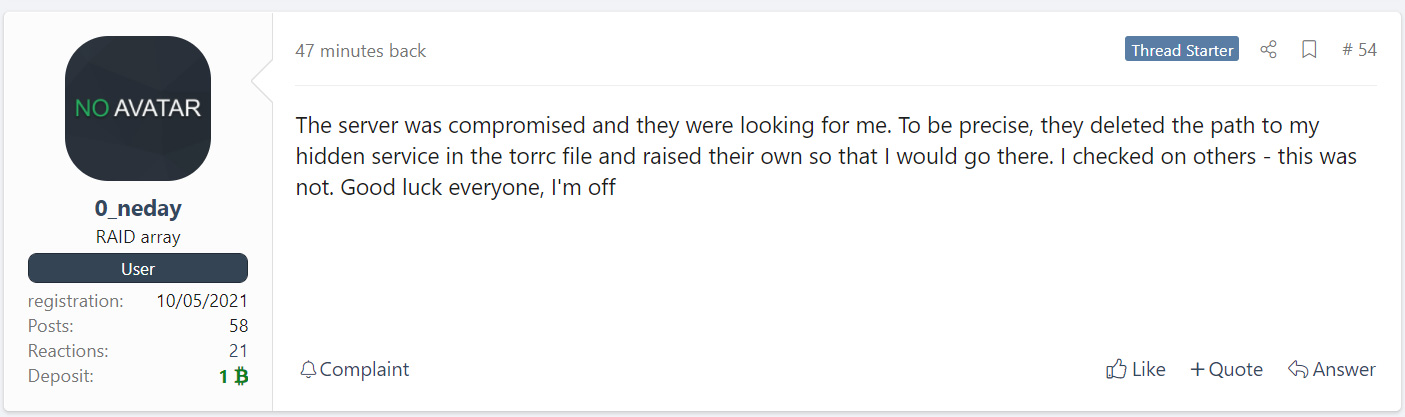
As part of this shutdown, a known REvil operator claimed that the unknown party was “looking” for them by modifying configuration files, so that the threat actor would be tricked into going to a site operated by the unknown entity.
Yesterday, Reuters reported that REvil’s takedown resulted from an international law enforcement operation that included support from the FBI.
Also Read: Top 8 Main PDPA Obligations To Boost And Secure Your Business
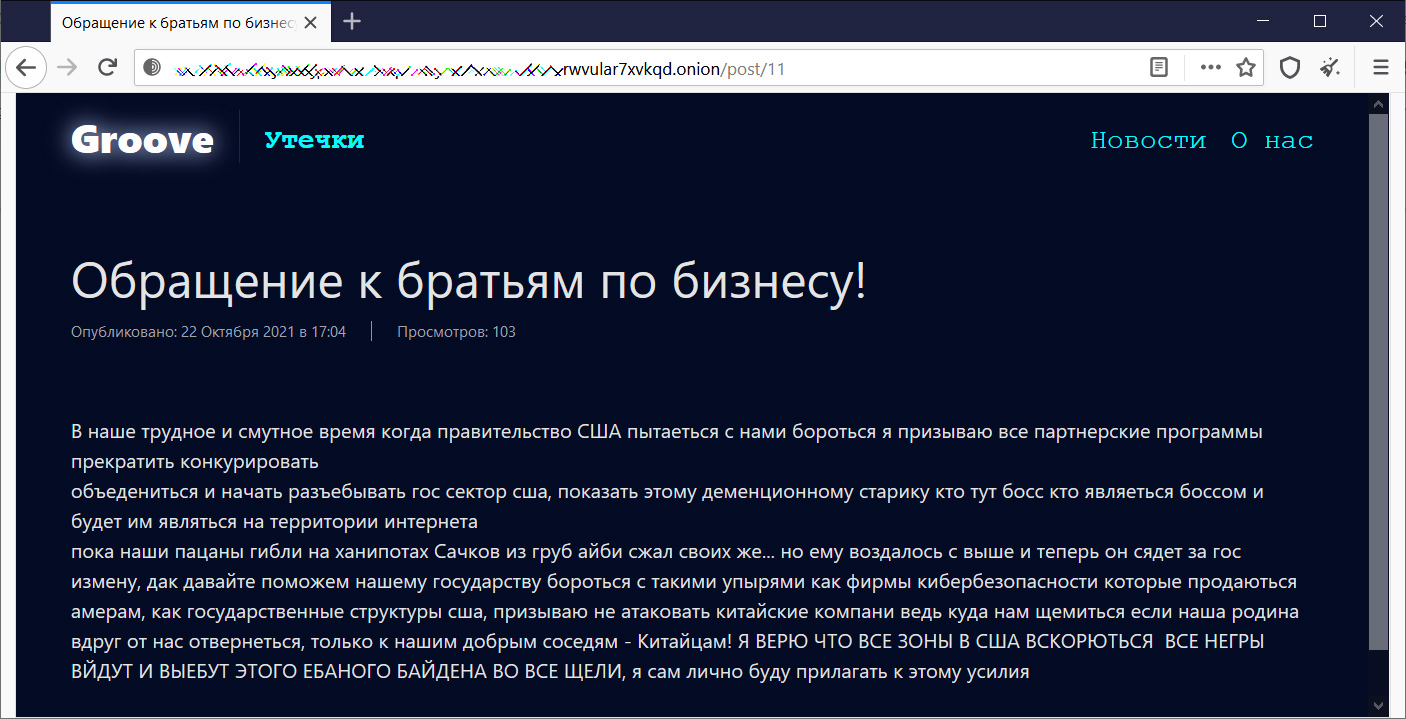
Today, the Groove ransomware gang published a Russian blog post calling on all other ransomware operations to target US interests.
The blog post also warns ransomware operations not to target Chinese companies, as the gangs would need to use the country as a safe haven if Russia takes a stronger stance on cybercrime operating inside its country.
The whole translated message, with some censoring of inappropriate words, can be read below.
“In our difficult and troubled time when the US government is trying to fight us, I call on all partner programs to stop competing,
unite and start xxcking up the US public sector, show this old man who is the boss here who is the boss and will be on the Internet
while our boys were dying on honeypots, the nets from rude aibi squeezed their own… but he was rewarded with higher and now he will go to jail for treason, so let’s help our state fight against such ghouls as cybersecurity firms that are sold to amers, like US government agencies, I urge not to attack Chinese companies, because where do we pinch if our homeland suddenly turns away from us, only to our good neighbors – the Chinese! I BELIEVE THAT ALL ZONES IN THE USA WILL BE OPENED, ALL xxOES WILL COME OUT AND xxCK THIS xxCKING BIDEN IN ALL THE CRACKS, I myself will personally make efforts to do this” – Groove ransomware.
The calling of attacks on US interests correlates with other information shared with BleepingComputer this week by a threat intelligence researcher for a Dutch bank.
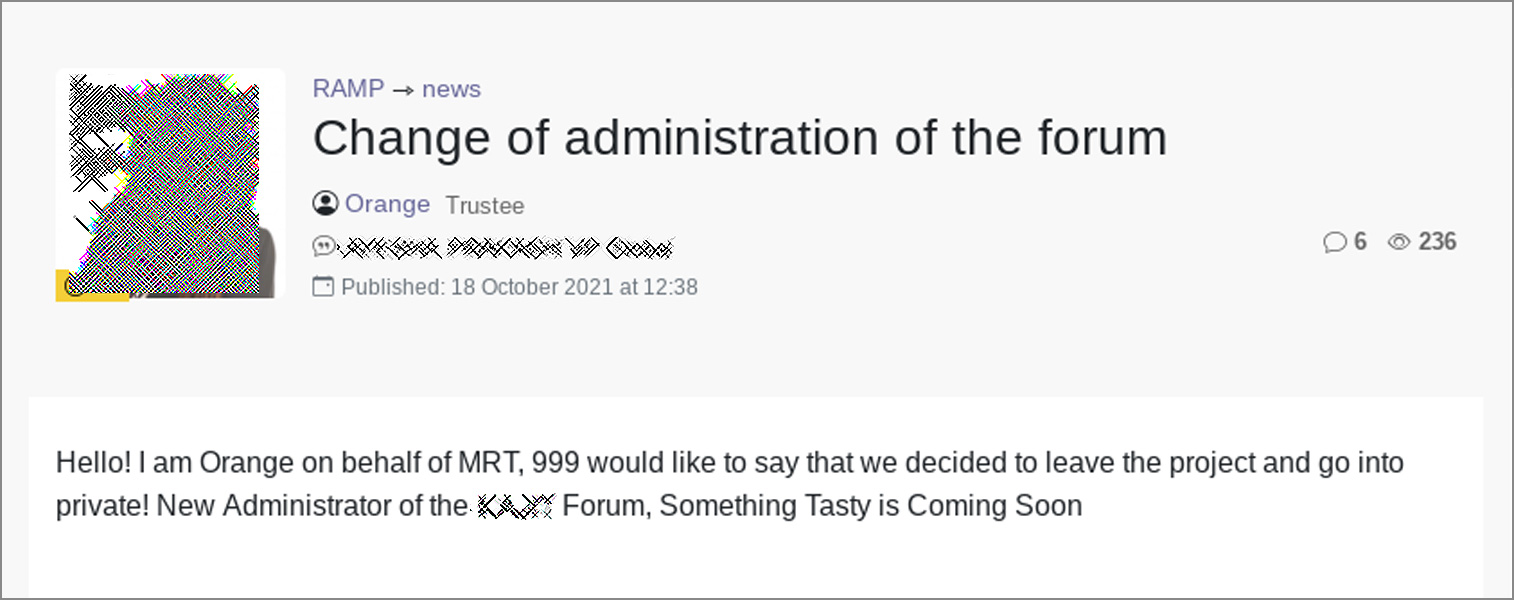
In July 2021, a threat actor known as ‘Orange’ launched the RAMP hacking forum after shutting down and splitting from the original Babuk Ransomware operation.
As Orange still controlled Babuk’s Tor site, he used it to launch the hacking forum where he acted as an admin. Orange is also believed to be one of the representatives of the Groove ransomware operation.
Recently, Orange stepped down as the forum’s admin to pursue a new operation but did not provide any further information on what was being planned.
Also Read: 5 Tips In Using Assessment Tools To A Successful Businesses
However, a later post indicates that the threat actor is likely starting a new ransomware operation as he began actively pursuing the purchase of network access to US hospitals and government agencies, as shown in the forum post below.
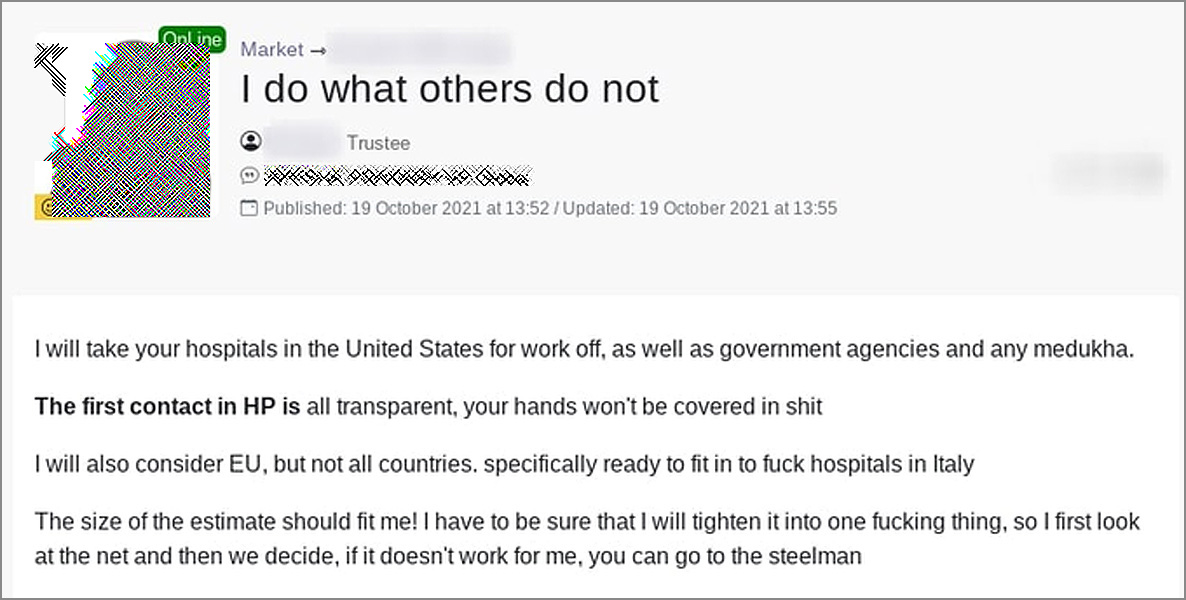
Groove’s post correlates with the above forum posts from Orange, indicating that targeting all USA interests has been planned for some time.
Today’s announcement from Groove Ransomware correlates with the Orange’s forum posts, indicating that targeting of all USA interests has been planned for some time, with the REvil law enforcement operation being the catalyst for Groove’s announcement.
It is unclear if ‘Orange’ will be performing these attacks on USA organizations under the Groove operation or launching a new ransomware operation.