KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says it found new variants of macOS malware known as WizardUpdate (also tracked as UpdateAgent or Vigram), updated to use new evasion and persistence tactics.
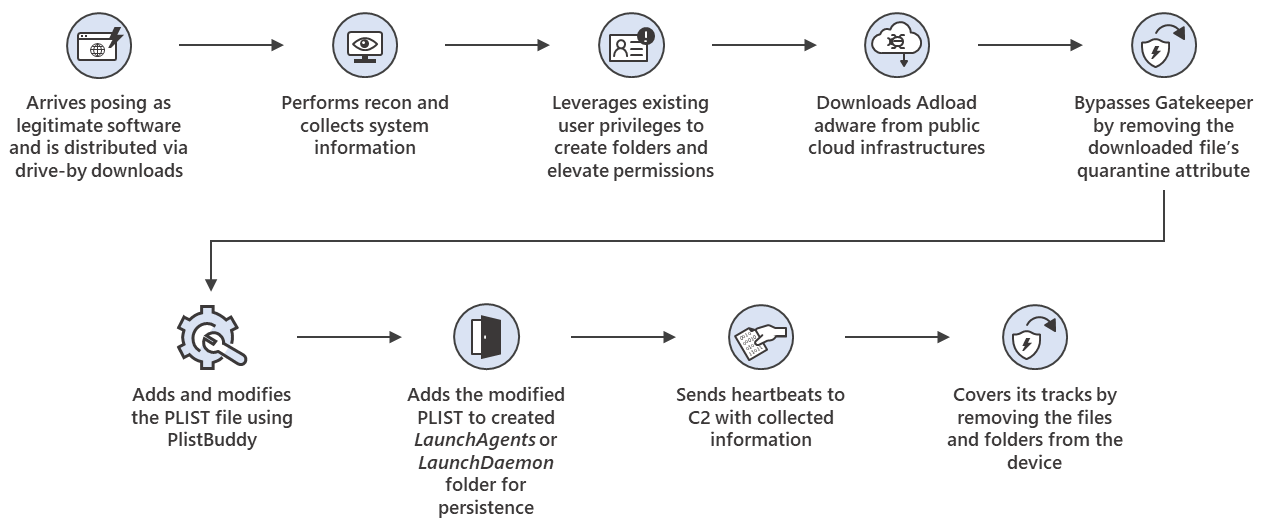
As Microsoft security experts found, the latest variant — spotted earlier this month — is likely being distributed via drive-by downloads and it impersonates legitimate software, just as it was when threat intelligence firm Confiant discovered it camouflaged as Flash installers in January.
Since the first variants were observed in November 2020, when it was only capable of collecting and exfiltrating system info, WizardUpdate was updated multiple times by its developers.
Also Read: How PII Data Works In Businesses And Its Advantages
The sample collected by Microsoft researchers in October comes with several upgrades, including the ability to:
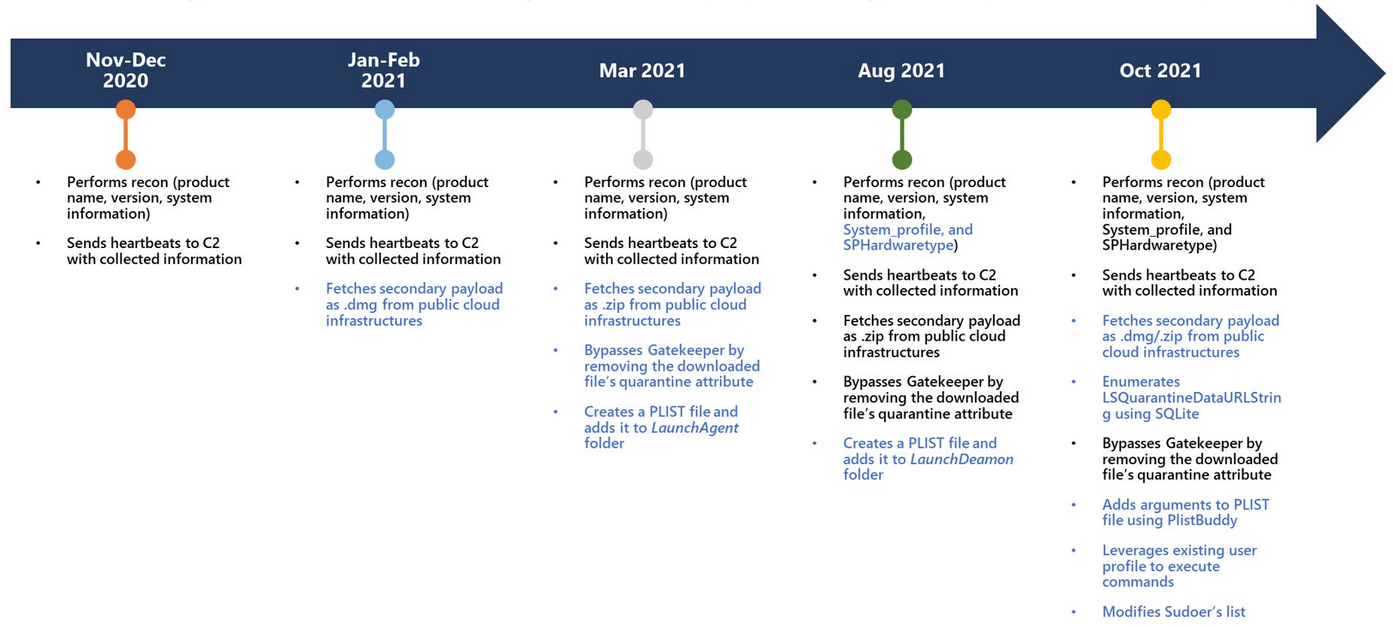
After it infects a target’s Mac, the malware starts scanning for and collecting system information that gets sent to its command-and-control (C2) server.
The trojan will deploy second-stage malware payloads, including a malware variant tracked as Adload, active since late 2017 and known for being able to slip through Apple’s YARA signature-based XProtect built-in antivirus to infect Macs.
“UpdateAgent abuses public cloud infrastructure to host additional payloads and attempts to bypass Gatekeeper, which is designed to ensure that only trusted apps run on Mac devices, by removing the downloaded file’s quarantine attribute,” Microsoft said.
“It also leverages existing user permissions to create folders on the affected device. It uses PlistBuddy to create and modify Plists in LaunchAgent/ LaunchDeamon for persistence.”
WizardUpdate’s developers have also included evasion features in the latest variant, which can cover its tracks by deleting created folders, files, and other artifacts created on the infected Macs
Also Read: How To Check Data Breach And How Can We Prevent It
AdLoad, one of the second-stage payloads delivered by WizardUpdate on compromised Macs, also hijacks search engine results and injects advertisements into web pages for monetary gain using a Man-in-The-Middle (MiTM) web proxy
It also gains persistence by adding LaunchAgents and LaunchDaemons and, in some cases, user cronjobs scheduled to run every two and a half hours.
While monitoring AdLoad campaigns active since November 2020, when WizardUpdate was also first spotted, SentinelOne threat researcher Phil Stokes found hundreds of samples, roughly 150 of them unique and undetected by Apple’s built-in antivirus.
Many of the samples detected by Stokes were also signed with valid Apple-issued Developer ID certificates, while others were notarized to run under default Gatekeeper settings.
Although both WizardUpdate and AdLoad now only deploy adware and bundleware as secondary payloads, they can switch at any time to more dangerous malware such as wipers or ransomware.
“Today, we have a level of malware on the Mac that we don’t find acceptable and that is much worse than iOS,” said Craig Federighi, Apple’s head of software, in May 2021 under oath while testifying in the Epic Games vs. Apple trial.