KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers found that an attacker could leave OpenSea account owners with an empty cryptocurrency balance by luring them to click on malicious NFT art.
With a transaction volume of $3.4 billion, OpenSea is the world’s largest marketplace for buying, selling, and auctioning non-fungible tokens (NFTs) and other digital assets and collectibles.
Details emerged today about an issue on the OpenSea platform that let hackers hijack user accounts and steal the associated cryptocurrency wallets.
Also Read: 5 Brief Concepts Between Data Protection Directive vs GDPR
The attack method is as simple as creating an NFT with a malicious payload and waiting for a victim to take the bait and view it.
Multiple users reported empty cryptocurrency wallets after receiving gifts on the OpenSea marketplace, a marketing tactic known as “airdropping” and used to promote new virtual assets.
Enticed by these accounts, researchers at cybersecurity company Check Point decided to take a closer look at how the platform works and check for vulnerabilities.
An OpenSea account requires a third-party cryptocurrency wallet from a list that the platform supports. One of the most popular is MetaMask, which is also what the researchers also chose.
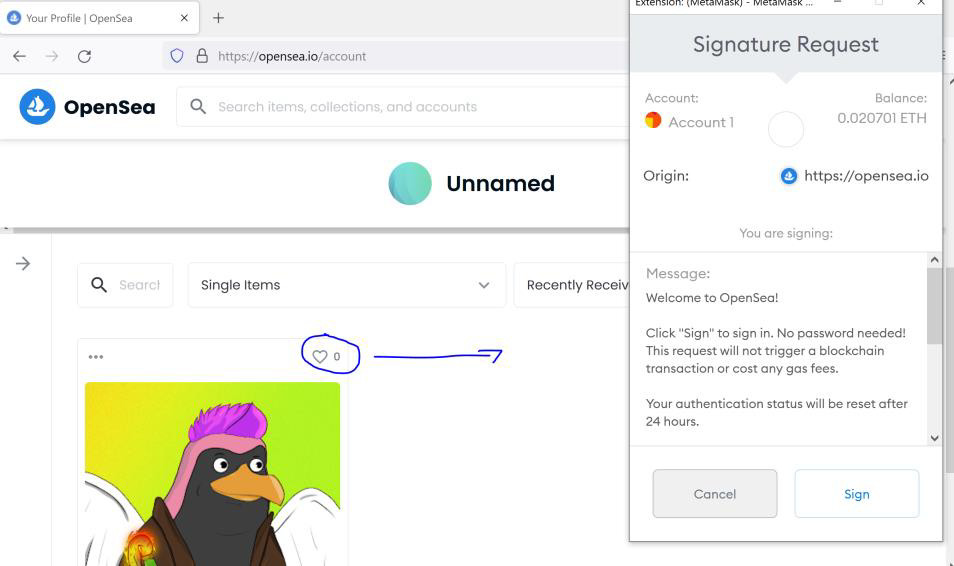
Communication with the wallet occurs for any action in the account, including liking art in the system, which triggers a wallet sign-in request.
The OpenSea platform lets anyone sell digital art, which can be files as large as 40MB with any of the following extensions: JPG, PNG, GIF, SVG, MP4, WEBM, MP3, WAV, OGG, GLB, GLTF.
Knowing this, Check Point uploaded to the OpenSea system an SVG image that carried malicious JavaScript code. When clicking on it to open in a new tab, they noticed that the file executed under the ‘storage.opensea.io’ subdomain.
They also added an iFrame to the SVG image to load HTML code that would inject the “window.ethereum” required to open communication with the victim’s Ethereum wallet.
Also Read: Top 10 Best Freelance Testing Websites That Will Pay You
“In our attack scenario, the user is asked to sign with their wallet after clicking an image received from a third party, which is unexpected behavior on OpenSea, since it does not correlate to services provided by the OpenSea platform, like buying an item, making an offer, or favoring an item” – Check Point
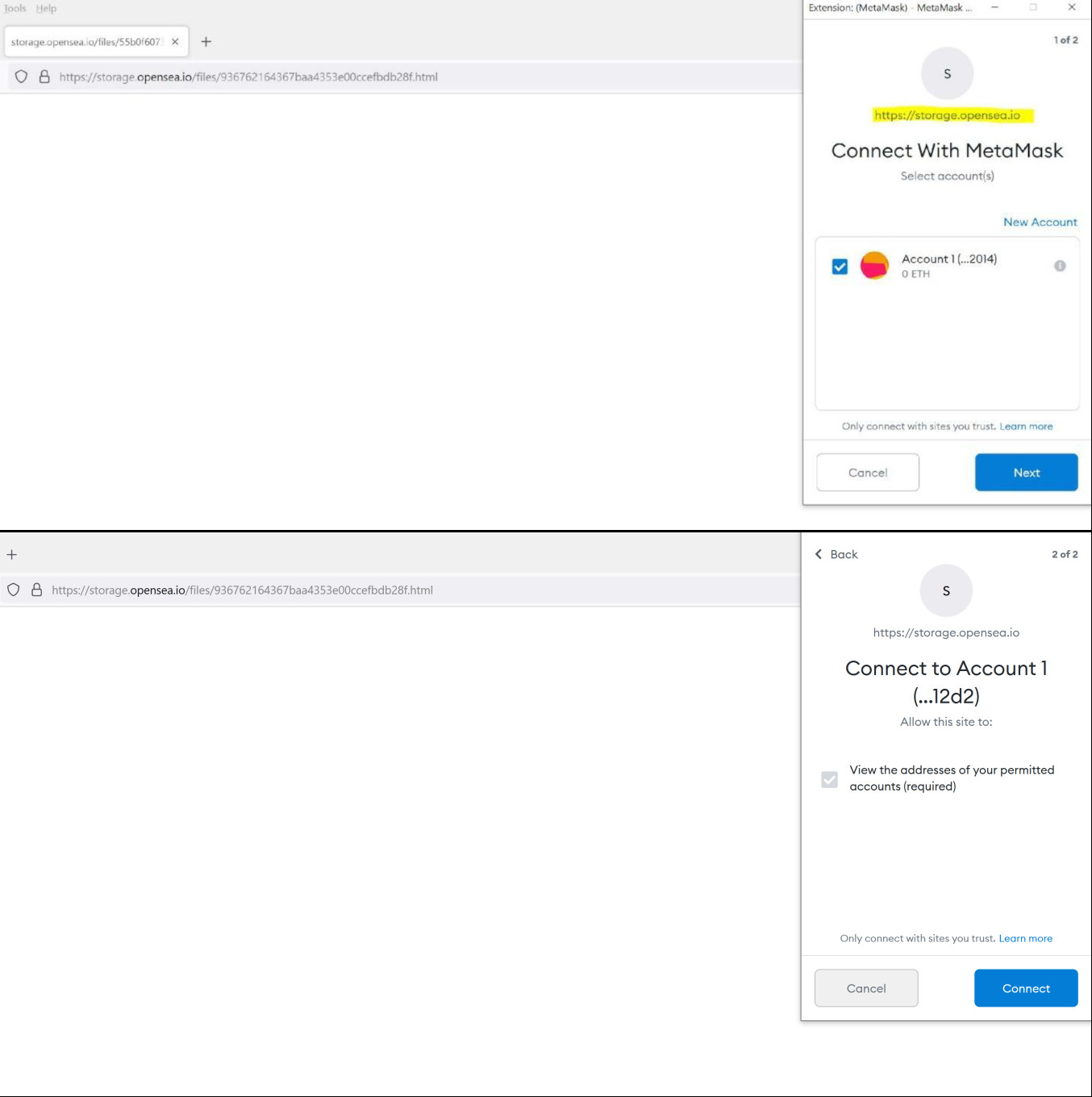
Abusing the wallet functionality is done through the Ethereum RPC-API, which starts the communication with MetaMask and opens the popup for connecting to the wallet.
An attacker then needed the victim to interact with the legitimate pop-up window so they could perform actions on behalf of the victim.
The researchers note that another signature request popup was required for the hacker to get the cryptocurrency in the wallet.
This would not have been much of a problem, though, since such requests “often appear as a system notice” and users are likely to approve the transaction without reading the message.
With a transaction domain from the OpenSea platform and action that victims typically see with other NFT operations, it is easy to see how users could have fallen victims.
In a report today, Check Point researchers summarized the attack as follows:
Check Point researchers informed OpenSea of their findings on September 26. The two parties collaborated to address the issue and OpenSea came up with a solution in less than an hour from the responsible disclosure.
OpenSea says that they could not identify any cases where attackers exploited this vulnerability but continue to raise awareness and educate the community on the best security practices and how to spot scams and phishing attempts.