KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The U.S. National Security Agency (NSA) is warning of the dangers stemming from the use of broadly-scoped certificates to authenticate multiple servers in an organization.
In a document released last week, the agency provides mitigations against the risks that come with the use of wildcard certificates. These include a recently disclosed ALPACA technique that could be used for various traffic redirect attacks.
The agency is referring to the dangers posed by wildcard or multi-domain digital certificates that validate server identity to allow a trusted, secure connection via the Transport Layer Security (TLS) cryptographic protocol.
In a presentation two months ago, researchers showed that TLS servers running different protocols but with compatible certificates (e.g. wildcard, multi-domain) could be exploited via an application layer protocol content confusion attack.
They named the technique ALPACA, short for Application Layer Protocols Allowing Cross-Protocol Attack, noting that a malicious actor meeting certain conditions could at least steal cookies or perform cross-site scripting attacks.
A wildcard digital certificate can be used with multiple subdomains on the same domain, so it can cover multiple servers (e.g. email, FTP, apps), while a multi-domain certificate is used for multiple domains on a single IP address.
Also Read: How To Comply With PDPA: A Checklist For Businesses
The NSA says [PDF] that “ALPACA is a complex class of exploitation techniques that can take many forms,” and that a realistic scenario for such an attack would require the following:
A threat actor meeting these “relatively uncommon conditions” would be able to run at least phishing, watering hole, malvertising, or man-in-the-middle (MitM) attacks.
Using the ALPACA technique, an adversary could cause the victim’s web browser to trust and execute responses reflected from a malicious service that are signed with the correct certificate.
This opens the door to stealing session cookies, private user data, and executing arbitrary code in the context of a vulnerable server.
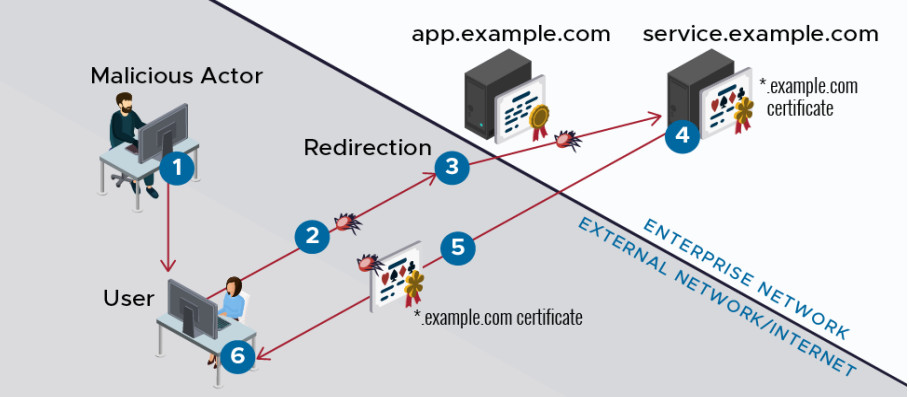
The NSA also reminds organizations of the role wildcard certificates play in a trust architecture since they “can be used to represent any system within its scope.”
For this reason, they should ensure the protection of the private key of a wildcard certificate and keep it on a well-maintained server to avoid the risk of an attacker getting it by compromising a poorly-secured machine.
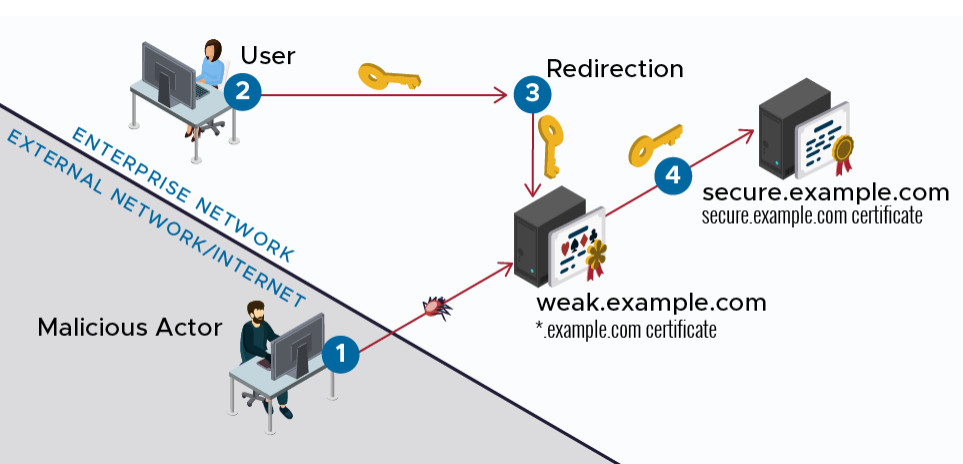
The NSA recommends organizations make sure that wildcard certificates are used responsibly and their scope within the organization is well understood.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing
Companies should identify where the private keys for these certificates are stored and use the security level required by all apps in the certificates’ scope.
Using an application gateway or a Web Application Firewall (WAF) in front of servers, non-HTTP ones included, is another recommendation from the agency.
Encrypted DNS and validating DNS Security Extensions (DNSSEC) to prevent DNS redirection that could land target users in a malicious location.
The NSA also recommends enabling the Application-Layer Protocol Negotiation (ALPN) if this is possible, and keeping browsers updated to their latest version.