KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new malware sold on dark web forums is being used by threat actors to steal accounts for multiple gaming platforms, including Steam, Epic Games Store, and EA Origin.
Kaspersky security researchers who spotted the new trojan in March dubbed it BloodyStealer and found that it’s capable of collecting and stealing a wide range of sensitive information, including cookies, passwords, bank cards, as well as sessions from various applications.
This malware explicitly targets gaming platforms, like Steam, Epic Games, EA Origin, GOG Galaxy, and more, as it can harvest accounts for its operators, which later sell them in underground markets.
“While BloodyStealer is not made exclusively for stealing game-related information, the platforms it can target clearly point to the demand for this type of data among cybercriminals,” Kaspersky said.
“Logs, accounts and in-game goods are some of the game-related products sold on the darknet in bulk or individually for an attractive price.”
Also Read: Battling Cyber Threats in 4 Simple Ways
The information stealer is sold through private channels to VIP members of underground forums under a subscription model for roughly $10 per month or $40 for a lifetime “license.”
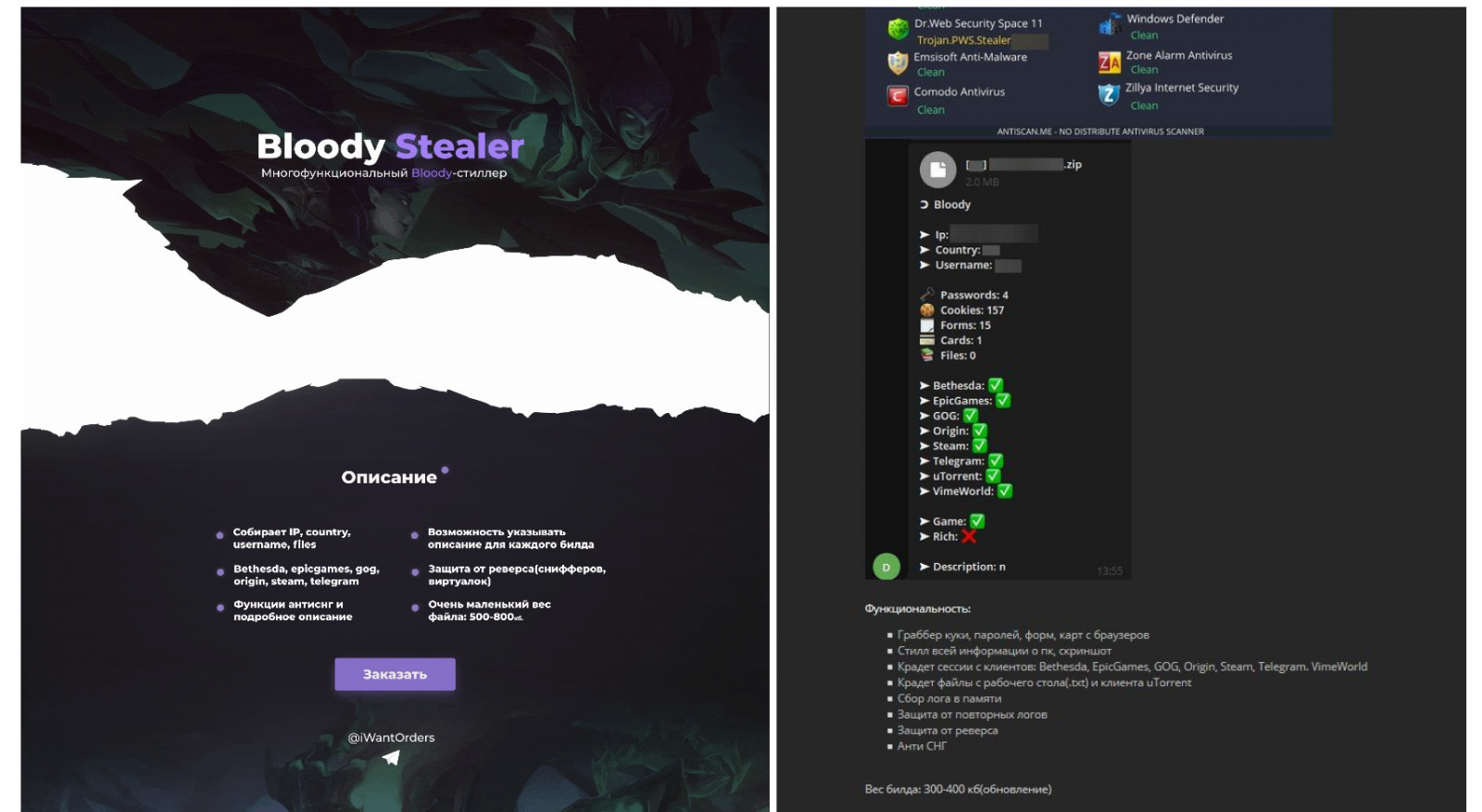
BloodyStealer is also marketed as coming with detection evasion and with malware analysis protection capabilities.
The complete list of capabilities, as described by its developers, includes:
Since its discovery, Kaspersky has detected BloodyStealer being used in attacks targeting victims from Europe, Latin America, and the Asia-Pacific region.
“BloodyStealer is a prime example of an advanced tool used by cybercriminals to penetrate the gaming market. With its efficient anti-detection techniques and attractive pricing, it is sure to be seen in combination with other malware families soon,” Kaspersky researchers added.
Also Read: What is Smishing? How Can We Prevent It? Explained.
“Furthermore, with its interesting capabilities, such as extraction of browser passwords, cookies, and environment information as well as grabbing information related to online gaming platforms, BloodyStealer provides value in terms of data that can be stolen from gamers and later sold on the darknet.”
You can find further info on BloodyStealer’s anti-analysis and data exfiltration capabilities in Kaspersky’s report.
While Kaspersky did not share info on the attack vectors used to deliver this malware, gamers are usually targeted by threat actors with malware-laced modding-related and game cheat tools if they are willing to cheat their way to victory or want to further mod their games.
Game cheats are a well-documented source of malware infections and have been used to infect unethical gamers with cryptocurrency miners, remote access trojans, and other malware strains for years.