KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says BulletProofLink, a large-scale phishing-as-a-service (PhaaS) operation it spotted while investigating recent phishing attacks, is the driving force behind many phishing campaigns that have targeted many corporate organizations lately.
The threat actor behind BulletProofLink (also known as BulletProftLink and Anthrax) provides cybercriminals with various services, ranging from selling phish kits and email templates to providing hosting and automated services under a single payment or monthly subscription-based business model.
“In researching phishing attacks, we came across a campaign that used a rather high volume of newly created and unique subdomains—over 300,000 in a single run,” the Microsoft 365 Defender Threat Intelligence Team said.
“With over 100 available phishing templates that mimic known brands and services, the BulletProofLink operation is responsible for many of the phishing campaigns that impact enterprises today.”
Also Read: 5 Common Sections in an Agreement Form Example
The BulletProofLink threat actor was first spotted in October 2020 by OSINT Fans, who published a three-part series [1, 2, 3] exposing some of the inner workings of this PhaaS operation.
As they revealed, the Bulletproftlink ICQ group chat had 1,618 members last year, “all potential buyers of the stolen passwords and the Bulletproftlink phishing services.”
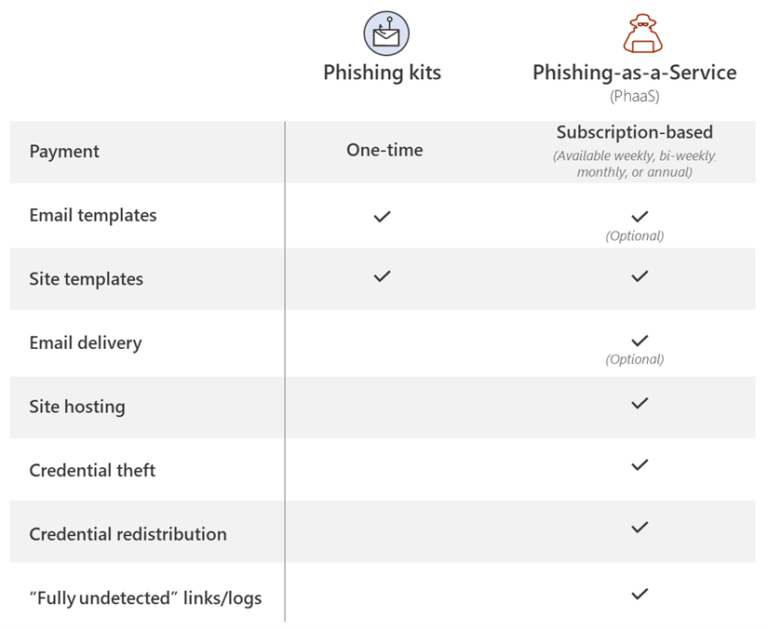
Of note, the large-scale phishing campaigns enabled by BulletProofLink also use a “double theft,” a method meant to boost the threat actor’s profits much like the double extortion one used by ransomware gangs.
The double theft Microsoft refers to is a tactic where credentials stolen in phishing attacks are also sent to a secondary server controlled by PhaaS operators if the phish kits used in the campaign use their default configuration.
This way, the credentials harvested by BulletProofLink customers are also sent to the phishing-as-a-service operator if the cybercriminals using their services will not customize the phish kits to exfiltrate stolen data only to their own servers.
“In both ransomware and phishing, the operators supplying resources to facilitate attacks maximize monetization by assuring stolen data, access, and credentials are put to use in as many ways as possible,” Microsoft added.
Also Read: Limiting Location Data Exposure: 8 Best Practices
“This is true for the BulletProofLink phishing kit, and in cases where the attackers using the service received credentials and logs at the end of a week instead of conducting campaigns themselves, the PhaaS operator maintained control of all credentials they resell.”