KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







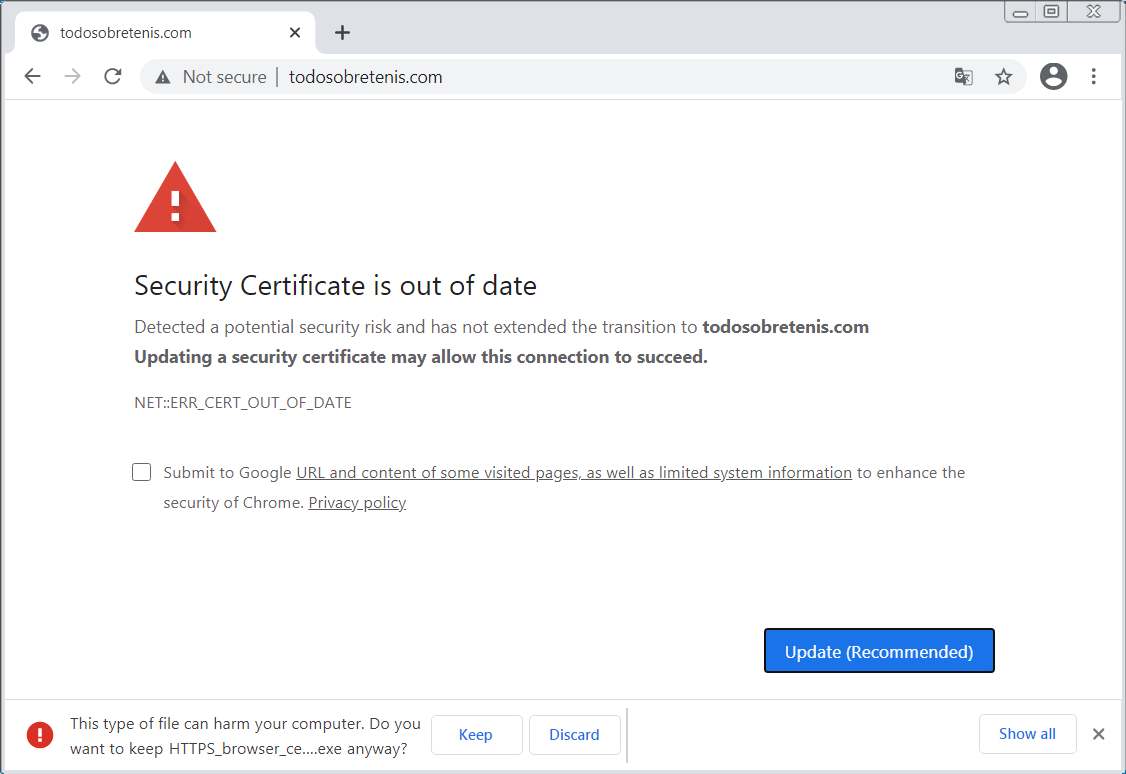
Threat actors are compromising Windows IIS servers to add expired certificate notification pages that prompt visitors to download a malicious fake installer.
Internet Information Services (IIS) is Microsoft Windows web server software included with all Windows versions since Windows 2000, XP, and Server 2003.
The message shown on the malicious certificate expiration error pages reads: “Detected a potential security risk and has not extended the transition to [sitename]. Updating a security certificate may allow this connection to succeed. NET::ERR_CERT_OUT_OF_DATE.”
Also Read: Lessons from PDPC Incident and Undertaking: August 2021 Cases
As Malwarebytes Threat Intelligence security researchers observed, the malware installed via a fake update installer [VirusTotal] signed with a Digicert certificate.
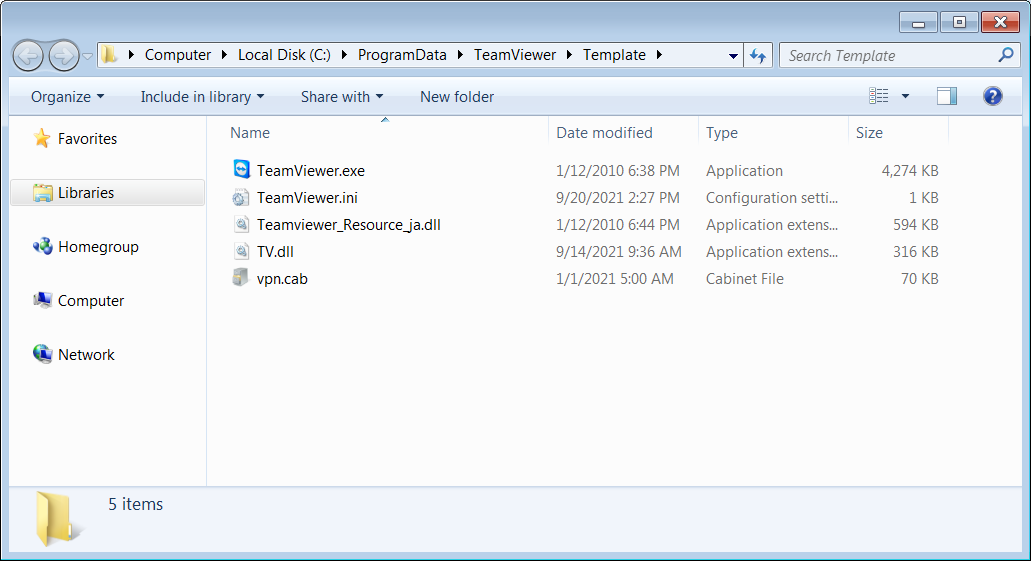
The payload dropped on infected systems is TVRAT (aka TVSPY, TeamSpy, TeamViewerENT, or Team Viewer RAT), a malware designed to provides its operators with full remote access to infected hosts.
Once deployed on infected device, the malware will silently install and launch an instance of the TeamViewer remote control software.
After being launched, the TeamViewer server will reach out to a command-and-control (C2) server to let the attackers know they can remotely take complete control of the newly compromised computer.
TVRAT first surfaced in 2013 when it was delivered via spam campaigns as malicious attachments that tricked targets into enabling Office macros.
While the method used by the attackers to compromise IIS servers is not yet known, attackers can use various ways to breach a Windows IIS serverr.
For instance, exploit code targeting a critical wormable vulnerability found in the HTTP Protocol Stack (HTTP.sys) used by the Windows IIS web server has been publicly available since May.
Microsoft patched the security flaw (tracked as CVE-2021-31166) during the May Patch Tuesday and said it only impacts Windows 10 versions 2004/20H2 and Windows Server versions 2004/20H2.
Also Read: Vulnerability Management For Cybersecurity Dummies
There hasn’t been any malicious activity abusing this flaw in the wild since then and, as we reported at the time, most potential targets were likely safe from attacks given that home users with the latest Windows 10 versions would’ve updated and companies don’t commonly use the latest Window Server versions.
However, state-sponsored level threat actors have also leveraged various other exploits to compromise internet-facing IIS servers in the past.
The most recent example is an advanced persistent threat (APT) group tracked as Praying Mantis or TG1021, which targeted Microsoft IIS web servers according to an August report from Israeli security firm Sygnia.
In their attacks, Praying Mantis used a Checkbox Survey RCE Exploit (CVE-2021-27852), a VIEWSTATE Deserialization and Altserialization Insecure Deserialization exploits, and a Telerik-UI Exploit (CVE-2019-18935, CVE-2017-11317).
“The operators behind the activity targeted Windows internet-facing servers, using mostly deserialization attacks, to load a completely volatile, custom malware platform tailored for the Windows IIS environment,” the researchers said.
Praying Mantis actors then used the access the hacked IIS servers provided to conduct additional malicious tasks, including credential harvesting, reconnaissance, and lateral movement on their targets’ networks.