KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





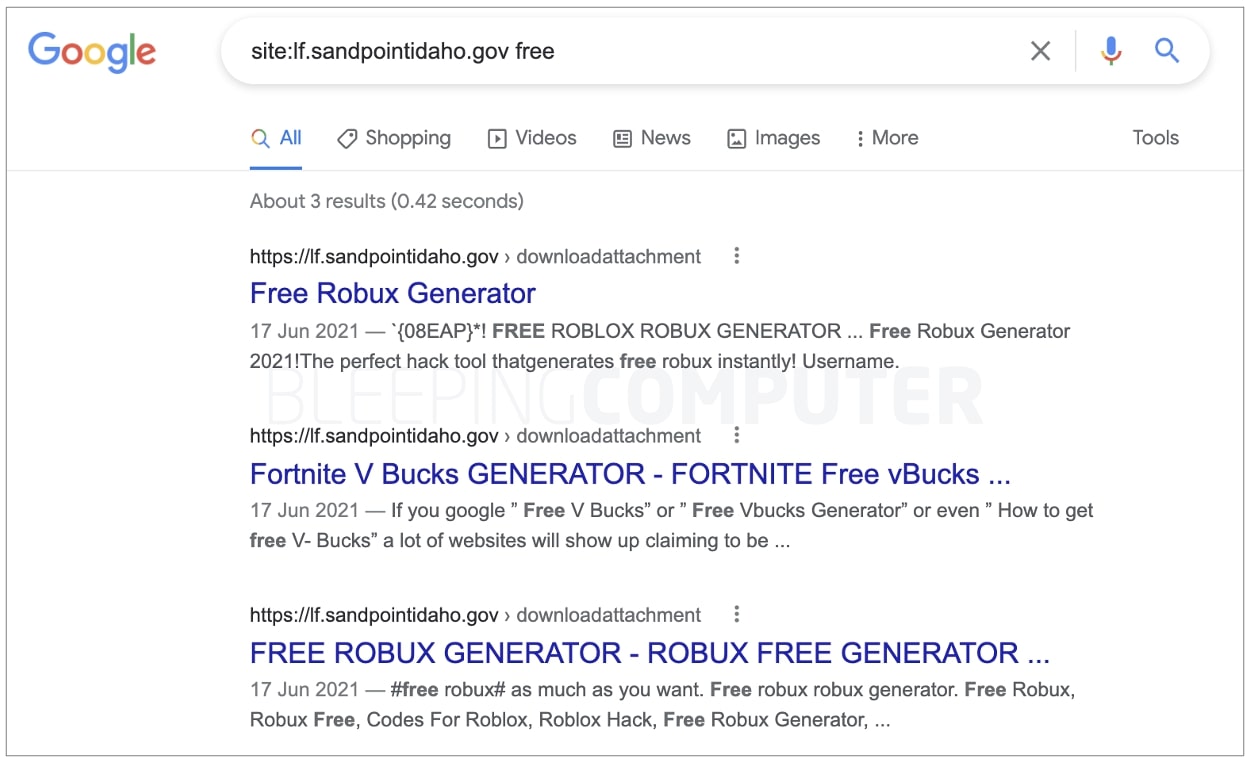
Multiple U.S. government sites using .gov and .mil domains have been seen hosting porn and spam content, such as Viagra ads, in the last year.
A security researcher noticed all of these sites share a common software vendor.
Security researcher Zach Edwards has traced the issue down to these .gov and .mil domains using a common software product provided by Laserfiche, a government contractor.
Laserfiche provides services to the FBI, CIA, U.S. Treasury, the military, and many more government bodies.
The software product called Laserfiche Forms contains a vulnerability that has allowed threat actors to push malicious and spam content on reputable government sites.
“This vulnerability created phishing lures on .gov and .mil domains that would push visitors into malicious redirects, and potentially target these victims with other exploits,” Edwards told Motherboard who first reported on the researcher’s findings.
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
Edwards, who has been tracking the flaw down for over a year has caught websites of U.S. Senator Jon Tester and the Minnesota National Guard [1, 2] sending users to Viagra product pages, for example.
He shared a video demonstrating the vulnerability in action and says he’s seen this behavior “on probably 50 different government subdomains.”
This isn’t the only attack vector leveraged by spammers. Previously, attackers have abused the open redirect functionality on government websites like that of the National Weather Service website sites to boost SEO for their content and redirect users to porn sites.
Laserfiche has now released a security advisory for the vulnerability, along with instructions on how to clean up your website from spam content.
According to the company, the root cause of the issue is an unauthenticated File Upload vulnerability.
Parts of Laserfiche Forms contain a public form that has a file upload field. This can be accessed by unauthenticated actors to upload files to your web portal and make their content temporarily accessible on the web.
“The vulnerability described here in this advisory is being exploited in a way where an unauthenticated third party can use Laserfiche Forms to temporarily host uploaded files for distribution,” states the company in the security advisory.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
“Valid customer form submission data is not impacted and is not accessible to the third party. The security updates address this vulnerability by reducing the time frame where the temporary file download link is active.”
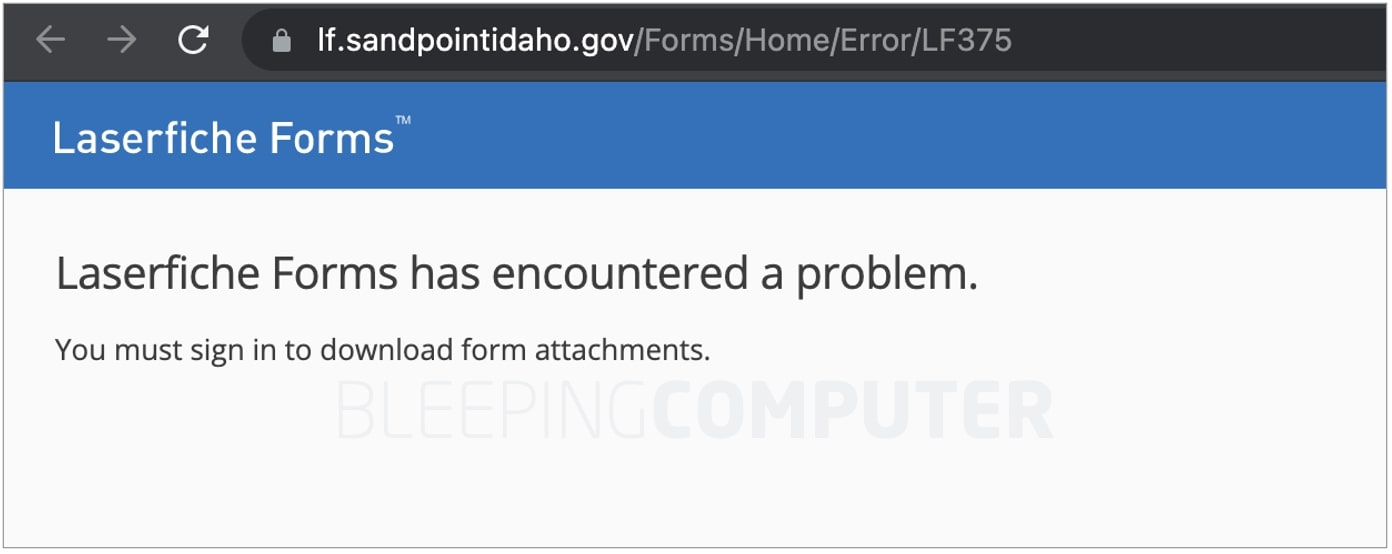
It appears some government clients have followed the remediation steps as accessing the aforementioned search results, previously showing spam content, are now throwing errors via the Laserfiche Forms instance:
However, Edwards isn’t quite satisfied as Laserfiche hasn’t fixed the vulnerability for all versions of its product that are still in widespread use, among other reasons.
“Note that not all versions of the update are available immediately,” says Laserfiche.
“We feel that it is important to notify our solution providers and customers of the vulnerability and the updates that are available now. Security updates for select prior versions of Laserfiche Forms are expected soon.”
Laserfiche has released a cleanup tool that clients can use to purge unauthorized uploads made to their web portals.