KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An unofficial Cobalt Strike Beacon Linux version made by unknown threat actors from scratch has been spotted by security researchers while actively used in attacks targeting organizations worldwide.
Cobalt Strike is a legitimate penetration testing tool designed as an attack framework for red teams (groups of security professionals who act as attackers on their own org’s infrastructure to discover security gaps and vulnerabilities.)
Cobalt Strike is also used by threat actors (commonly dropped in ransomware attacks) for post-exploitation tasks after deploying so-called beacons, which provide persistent remote access to compromised devices. Using beacons, attackers can later access breached servers to harvest data or deploy further malware payloads.
Over time, cracked copies of Cobalt Strike have been obtained and shared by threat actors, becoming one of the most common tools used in cyberattacks leading to data theft and ransomware. However, Cobalt Strike has always had a weakness — it only supports Windows devices and does not include Linux beacons.
In a new report by security firm Intezer, researchers explain how threat actors have taken it upon themselves to create their Linux beacons compatible with Cobalt Strike. Using these beacons, threat actors can now gain persistence and remote command execution on both Windows and Linux machines.
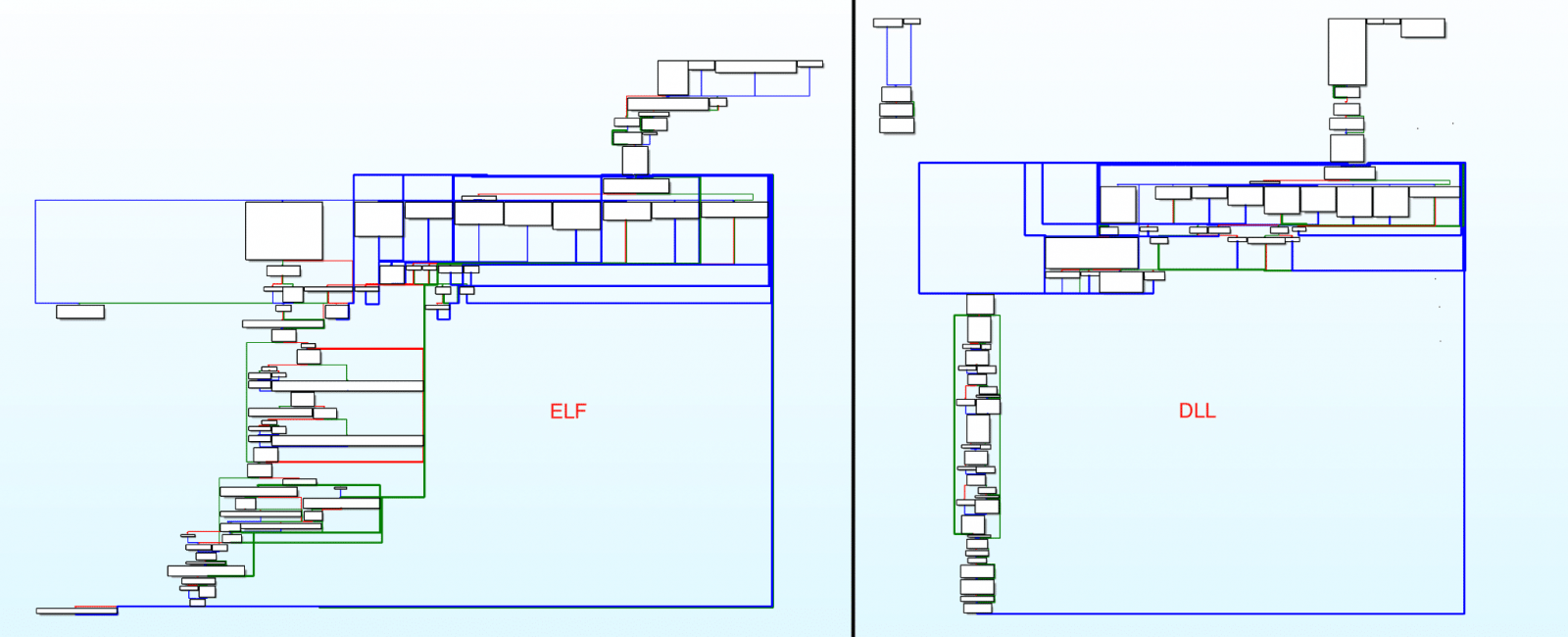
Intezer researchers, who first spotted the beacon re-implementation in August and dubbed it Vermilion Strike, said that the Cobalt Strike ELF binary [VirusTotal] they discovered is currently fully undetected by anti-malware solutions.
Vermilion Strike comes with the same configuration format as the official Windows beacon and can speak with all Cobalt Strike servers, but doesn’t use any of Cobalt Strike’s code.
This new Linux malware also features technical overlaps (the same functionality and command-and-control servers) with Windows DLL files hinting at the same developer.
Also Read: Top 11 Ultimate Cold Calling Guidelines To Boost Your Sales
“The stealthy sample uses Cobalt Strike’s Command and Control (C2) protocol when communicating to the C2 server and has Remote Access capabilities such as uploading files, running shell commands and writing to files,” Intezer said.
“The malware is fully undetected in VirusTotal at the time of this writing and was uploaded from Malaysia.”
Vermilion Strike can perform the following tasks once deployed on a compromised Linux system:
Using telemetry data provided by McAfee Enterprise ATR, Intezer also found multiple orgs targeted using Vermilion Strike since August 2021 from various industry sectors ranging from telecom companies and government agencies to IT companies, financial institutions, and advisory companies worldwide.
It’s also worth mentioning that Vermilion Strike is not the first or only port of Cobalt Strike’s Beacon to Linux, with geacon, an open-source Go-based implementation, publicly available for the last two years.
However, as Intezer told BleepingComputer, “this is the first Linux implementation that has been used for real attacks.” Unfortunately, there is no info on the initial attack vector the attackers use to target Linux systems.
Also Read: IT Equipment Disposal Singapore and Recycle Services
“The sophistication of this threat, its intent to conduct espionage, and the fact that the code hasn’t been seen before in other attacks, together with the fact that it targets specific entities in the wild, leads us to believe that this threat was developed by a skilled threat actor,” Intezer concluded.