KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






A new distributed denial-of-service (DDoS) botnet that kept growing over the summer has been hammering Russian internet giant Yandex for the past month, the attack peaking at the unprecedented rate of 21.8 million requests per second.
The botnet received the name Mēris, and it gets its power from tens of thousands of compromised devices that researchers believe to be primarily powerful networking equipment.
News about a massive DDoS attack hitting Yandex broke this week in the Russian media, which described it as being the largest in the history of the Russian internet, the so-called RuNet.
Details have emerged today in joint research from Yandex and its partner in providing DDoS protection services, Qrator Labs.
Also Read: Top 10 Exceptional And Creative Website Design Guidelines
Information collected separately from several attacks deployed by the new Mēris (Latvian for ‘plague’) botnet, showed a striking force of more than 30,000 devices.
From the data that Yandex observed, assaults on its servers relied on about 56,000 attacking hosts. However, the researchers have seen indications that the number of compromised devices may be closer to 250,000.
“Yandex’ security team members managed to establish a clear view of the botnet’s internal structure. L2TP tunnels are used for internetwork communications. The number of infected devices, according to the botnet internals we’ve seen, reaches 250 000” – Qrator Labs
The difference between the attacking force and the total number of infected hosts forming Mēris is explained by the fact that the administrators do not want to parade the full power of their botnet, Qrator Labs says in a blog post today.
The researchers note that the compromised hosts in Mēris are “not your typical IoT blinker connected to WiFi” but highly capable devices that require an Ethernet connection.
Mēris is the same botnet responsible for generating the largest volume of attack traffic that Cloudflare recorded and mitigated to date, as it peaked at 17.2 million requests per second (RPS).
However, Mēris botnet broke that record when hitting Yandex, as its flux on September 5 reached a force of 21.8 million RPS.
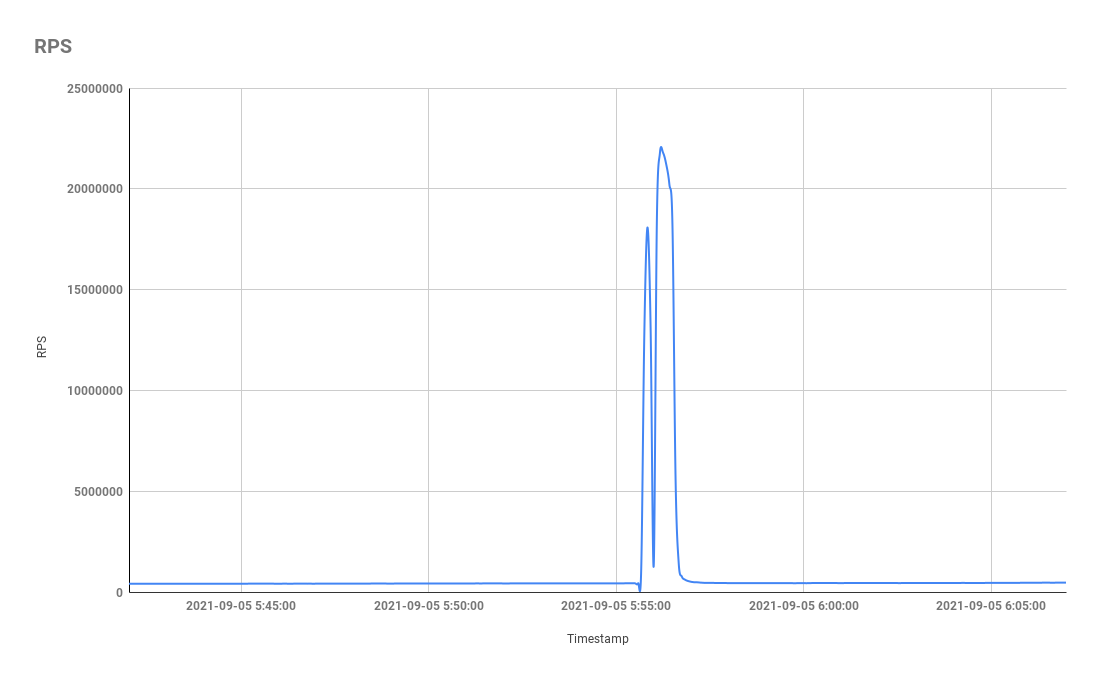
The botnet’s history of attacks on Yandex begins in early August with a strike of 5.2 million RPS and kept increasing in strength:
To deploy an attack, the researchers say that Mēris relies on the SOCKS4 proxy at the compromised device, uses the HTTP pipelining DDoS technique, and port 5678.
As for the compromised devices used, the researchers say that they are related to MikroTik, the Latvian maker of networking equipment for businesses of all sizes.
Most of the attacking devices had open ports 2000 and 5678. The latter points to MikroTik equipment, which uses it for the neighbor discovery feature (MikroTik Neighbor Discovery Protocol).
Qrator Labs found that while MikroTik provides its standard service through the User Datagram Protocol (UDP), compromised devices also have an open Transmission Control Protocol (TCP).
This kind of disguise might be one of the reasons devices got hacked unnoticed by their owners,” Qrator Labs researchers believe.
Also Read: Data Protection Officer Duties And Responsibilities
When searching the public internet for open TCP port 5678, more than 328,000 hosts responded. The number is not all MikroTik devices, though, as LinkSys equipment also uses TCP on the same port.
Port 2000 is for “Bandwidth test server,” the researchers say. When open, it replies to the incoming connection with a signature that belongs to MikroTik’s RouterOS protocol.
MikroTik has been informed of these findings. The vendor told Russian publication Vedomosti that it is not aware of a new vulnerability to compromise its products.
The network equipment maker also said that many of its devices continue to run old firmware, vulnerable to a massively exploited security issue tracked as CVE-2018-14847 and patched in April 2018.
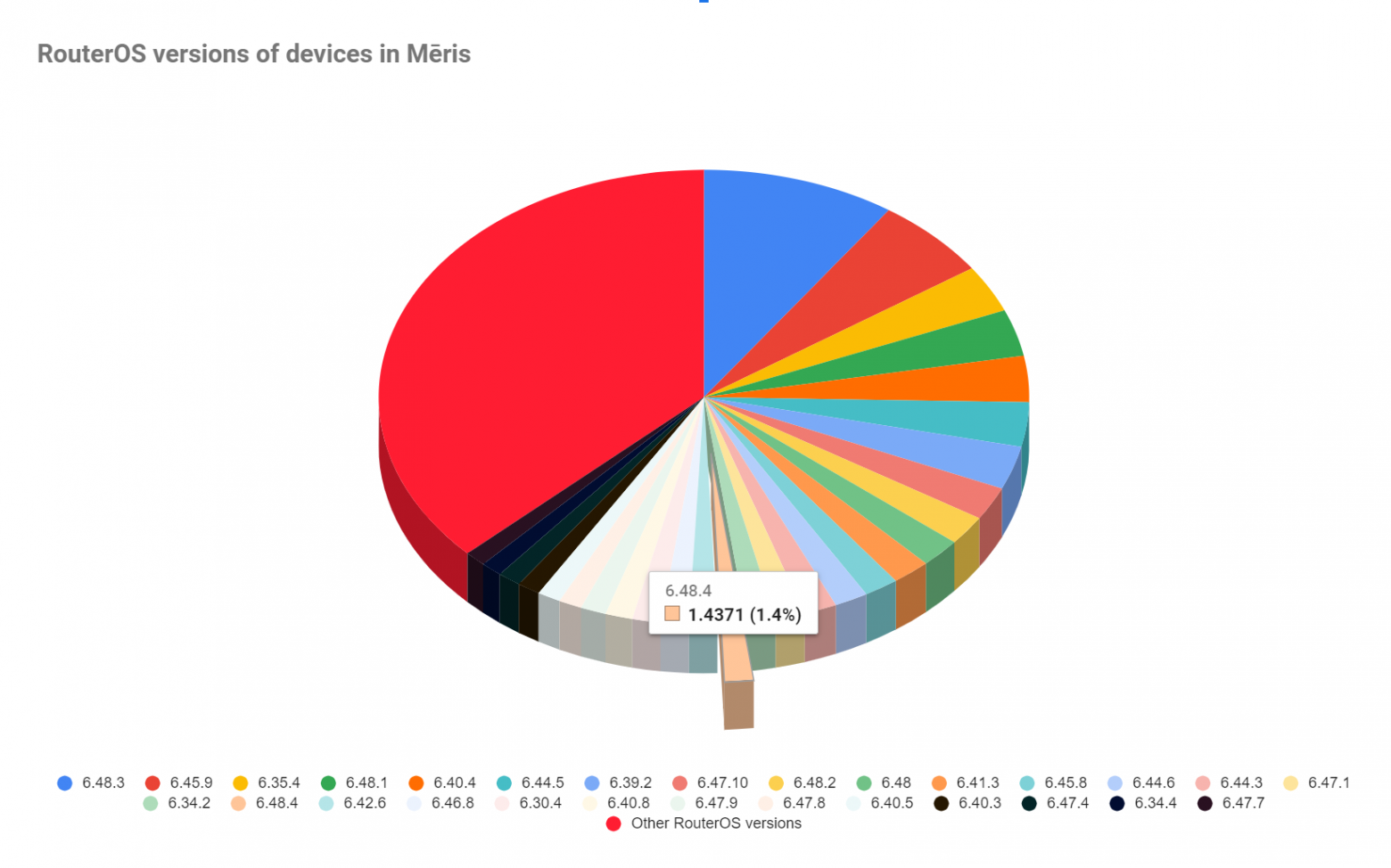
However, the range of RouterOS versions that Yandex and Qrator Labs observed in attacks from Mēris botnet varies greatly and includes devices running newer firmware versions, such as the current stable one (6.48.4) and its predecessor, 6.48.3.