KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







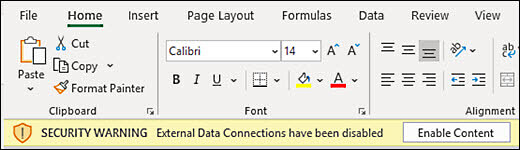
Microsoft plans to allow Office 365 admins ensure that end-users can’t ignore organization-wide policies set up to block active content on Trusted Documents.
Redmond says trusted docs are files with active content (e.g., ActiveX controls, macros, and Dynamic Data Exchange (DDE) functions that don’t require user interaction) that open without warnings after the content has been enabled.
Trusted documents will automatically open without prompts even if altered by adding new (potentially malicious) active content, bypassing Office’s Protected View, which opens files from potentially unsafe locations as read-only.
“However, the prompt appears if the file was moved since you last trusted the file. After a document is trusted, it does not open in Protected View. Therefore, you should trust documents only if you trust the source of the file,” Microsoft explains.
Also Read: PDPA Laws And Regulations; A Systematic Guidelines In Singapore
“We are changing the behavior of Office applications to enforce policies that block Active Content (ex. macros, ActiveX, DDE) on Trusted Documents,” Microsoft said on the Microsoft 365 Roadmap.
“Previously, Active Content was allowed to run in Trusted Documents even when an IT administrator had set a policy to block it.”
As part of an ongoing effort towards Office security hardening, the IT administrators’ choice to block Active Content even for trusted files will now always take precedence over the user’s choice to trust a document.
This would translate in all documents with embedded active content being opened in Protected View, despite a user’s willingness to ignore security warnings reminding them that all active content has been disabled.
Also Read: What Is PDPA And What Are The 5 Things You Should Know About
Microsoft plans to roll out this new feature by the end of October, making it generally available worldwide in all environments.
In related news, Redmond is also updating Defender for Office 365 to protect users from embedded email threats when previewing quarantined emails.
In May, Microsoft updated the security baseline for Microsoft 365 Apps for enterprise (formerly Office 365 Professional Plus) to protect from unsigned macros and JScript code execution attacks.
In March, it also added XLM macro protection for Microsoft 365 customers to block malware abusing Office VBA macros and PowerShell, JScript, VBScript, MSHTA/Jscript9, WMI, or .NET code, which are regularly used to deploy malicious payloads via Office document macros.