KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Almost a month after a disgruntled Conti affiliate leaked the gang’s attack playbook, security researchers shared a translated variant that clarifies any misinterpretation caused by automated translation.
Apart from providing information about the gang’s attack methods and the thoroughness of the instructions, which allow for less-skilled actors to become Conti ransomware affiliates and hit valuable targets.
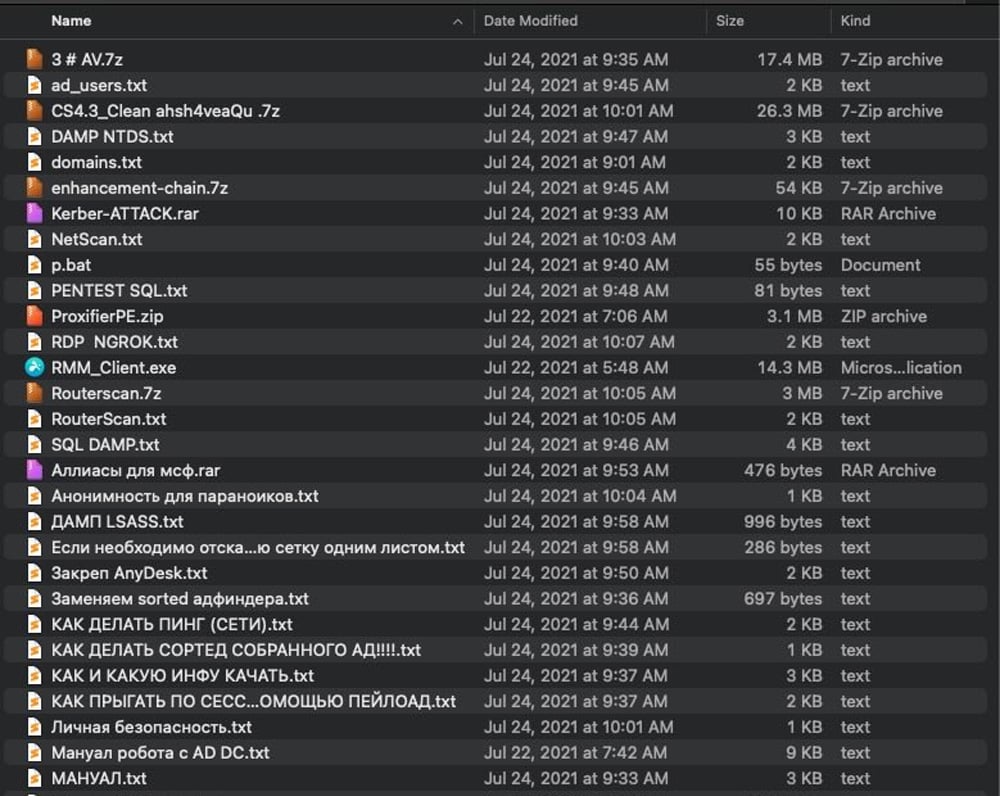
Linguists working with Cisco Talos researchers went through the leaked material to provide an intelligible English version that accurately describes the gang’s techniques and tools.
The attack scenarios described in the documents were so thorough that “even amateur adversaries [could] carry out destructive ransomware attacks,” the researchers say.
“This lower barrier to entry also may have led to the leak by a disgruntled member who was viewed as less technical (aka “a script kiddie”) and less important”
Among the “tips” provided in the manuals is how to get administrator access after breaching a victim’s network by using commands and tools to list users, particularly those with Active Directory access.
Simple reconnaissance like checking LinkedIn and other social media platforms to identify employees with privileged access is also detailed, with a note that the techniques work better for companies in the U.S. and Europe.
The top tool described in the leaked material is the Cobalt Strike red-teaming framework, accompanied by a cracked 4.3 version of the software.
Usage instructions also referred to exploiting the ZeroLogon vulnerability (CVE-2020-1472). Other critical bugs mentioned in Conti ransomware’s playbook are PrintNightmare (CVE-2021-1675, CVE-2021-34527) and EternalBlue (CVE-2017-0143/0148).
Also Read: A Look At The Risk Assessment Form Singapore Requires
Some of the tools detailed by the adversary are not what Cisco researchers typically see during incident response engagements:
Among other tools and command-line utilities described in the leaked documents include the following:
Before moving to the exploitation part, the affiliates are instructed to learn about their victim’s revenue by looking for open source info.
The leak from the angry Conti affiliate also includes video tutorials, mostly in Russian, that explain how to use PowerShell for pen-testing, attacking the Active Directory, or how to use leverage SQL Server in a Windows domain.
Much of the video tutorials (Metasploit, PowerShell, WMI attacks and defense, network pen-testing) for affiliates is from various offensive security resources readily available online.
Cisco Talos researchers believe that the translated version of the leaked Conti documentation will help other researchers better understand the tactics, techniques, and procedures of this threat actor as well as others that may be inspired by documentation.
Also Read: CCTV Law Singapore Edition: Know Your Rights and Responsibilities
“This is an opportunity for defenders to make sure they have logic in place to detect these types of behaviors or compensating controls to help mitigate the risk. This translation should be viewed as an opportunity for defenders to get a better handle on how these groups operate and the tools they tend to leverage in these attacks” – Cisco Talos
The researchers provide translated individual texts in a ZIP archive as well as a PDF file. A summary of the materials is also available from Fortinet.