KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







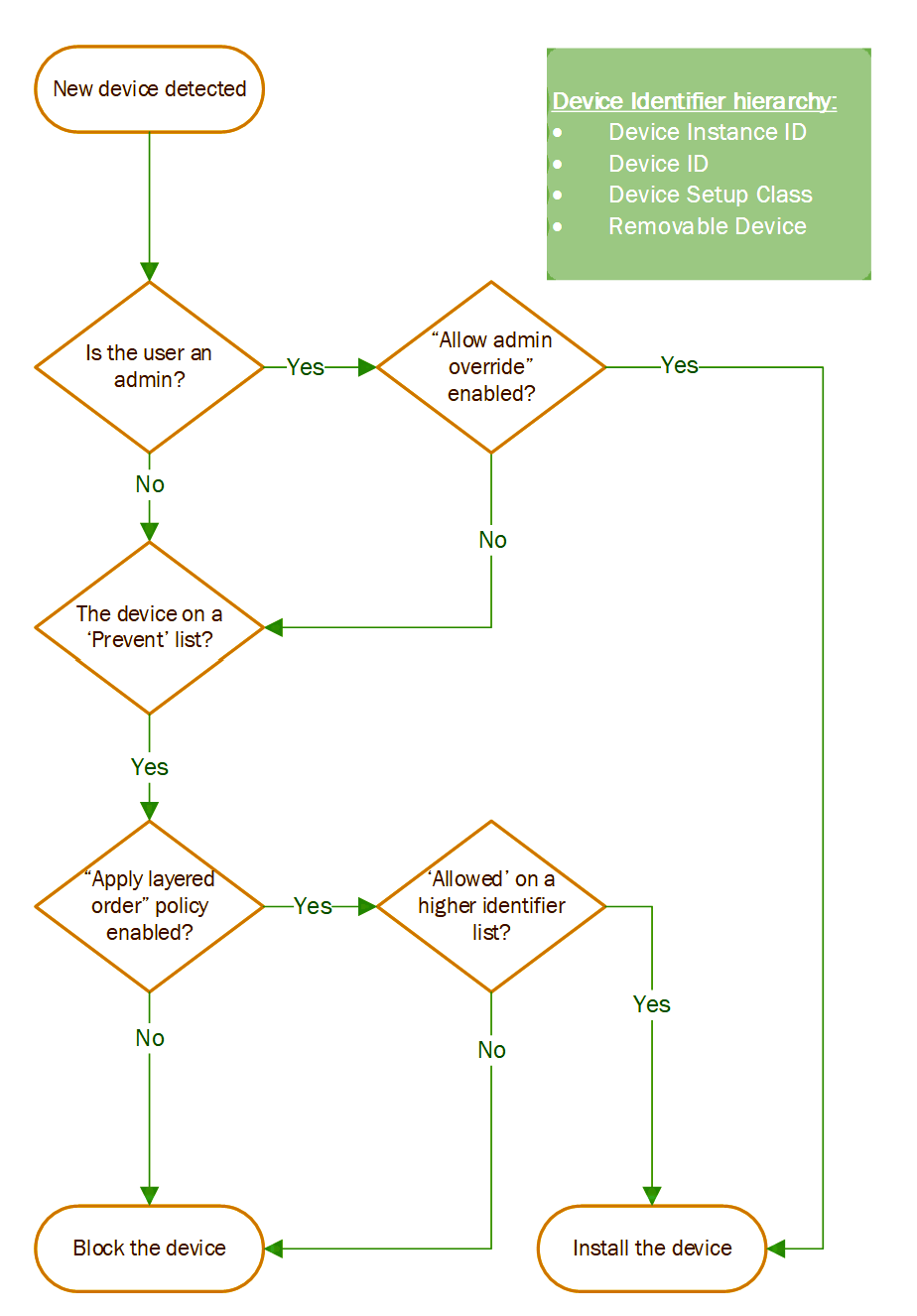
Microsoft has added support for layered Group Policies, which allow IT admins to control what internal or external devices users can be installed on corporate endpoints across their organization’s network.
Devices that can be blocked or allowed to install on endpoints include printers, USB storage drives, and other USB peripherals added to a given organization’s prohibited or approved list of devices.
Benefits of controlling device installation with the help of group policies include reducing support costs and decreasing the risk of corporate data theft.
All devices come with their own set of “device identifiers” understood by the system (e.g., class, device ID, and instance ID).
Using these identifiers, an admin can create an ‘allow list’ of allowed devices that will block all other devices from being installed.
The new apply layered Group Policy feature provides more granular control over what devices are blocked from installation using a set of device identifiers such as instance IDs, hardware IDs, setup class, and removable device property.
Also Read: Don’t Be Baited! 5 Signs of Phishing in Email
Per Microsoft, using the apply layered Group Policy with already existing device installation policies improves flexibility and intuitive usage:
If you want to apply right now in your environment, the path to the new Group Policy is Computer Configuration > Administrative Templates > System > Device Installation > Device Installation Restrictions > ‘Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria’.
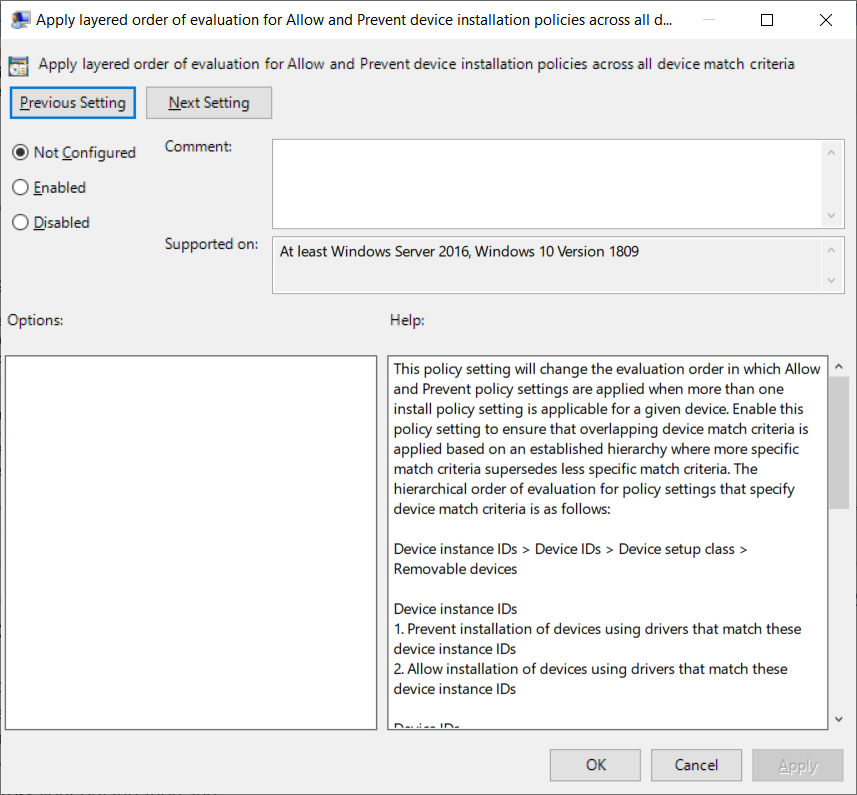
“Applying layered Group Policy is available on all Windows 10 systems where as part of the July 2021 optional ‘C’ client release, and will be made more broadly available beginning in the August 2021 Update Tuesday release,” Microsoft said.
Also Read: 4 Reasons to Outsource Penetration Testing Services
“The Windows Server release will follow thereafter. This feature will also be supported in Windows 11.”
Additional information on the “Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria” policy setting is available on the Microsoft 365 docs website.