KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have published comprehensive recommendations for strengthening the security of an organization’s Kubernetes system.
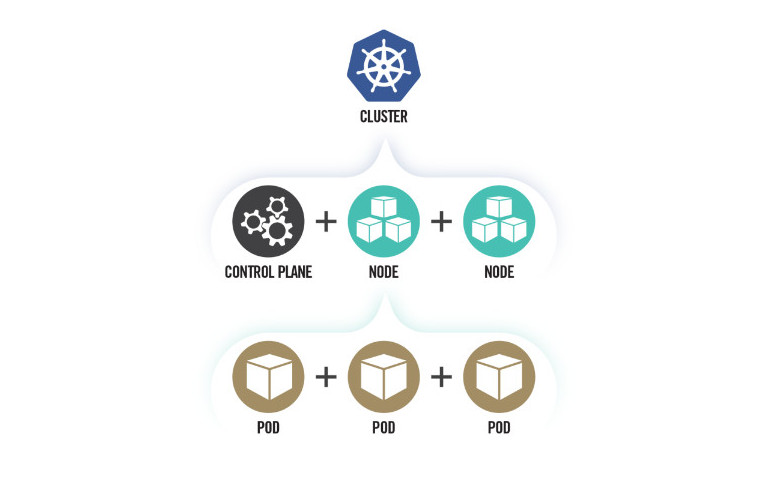
Kubernetes is a popular open-source solution for deploying, scaling, and managing containerized apps in the cloud, making it an attractive target for cyber attacks.
Also Read: Don’t Be Baited! 5 Signs of Phishing in Email
Hackers are constantly hitting Kubernetes environments, their motivation varying from stealing data, to cryptocurrency mining, to denial-of-service (DoS) that could act as a diversion for other operations.https://www.ad-sandbox.com/static/html/sandbox.html
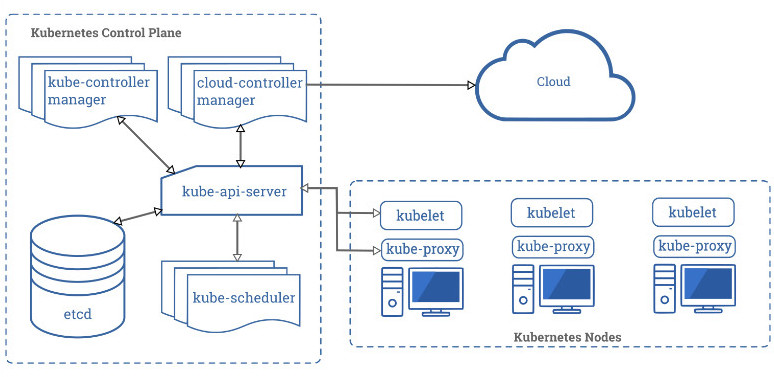
To help companies make their Kubernetes environment more difficult to compromise, the NSA and CISA released a 52-page cybersecurity technical report that offers guidance for admins to manage Kubernetes securely.
The NSA says that the main three causes for a compromised Kubernetes environment are supply-chain attacks, malicious actors, and insider threats.
While administrators can’t prevent all three risks, they can harden the security of a Kubernetes cluster by avoiding common misconfigurations and applying mitigations to minimize security risks.
The agency notes that supply-chain attacks “are often challenging to mitigate,” adding that a malicious threat actor’s way in is typically exploiting a vulnerability or leveraging misconfigurations.
“Insider threats can be administrators, users, or cloud service providers. Insiders with special access to an organization’s Kubernetes infrastructure may be able to abuse these privileges” – the National Security Agency
In broad strokes, the defensive actions against this these threats is to scan containers and Pods for bugs and misconfigurations; use the least privileges to run run Pods and containers (unless higher permissions are needed), and use network separation, strong authentication, properly configured firewalls, and audit logs.
Admins should also review all Kubernetes settings regularly and ensure that the system benefits from the latest updates, patches, and available upgrades.
Titled “Kubernetes Hardening Guidance,” the document goes through each of the following security recommendations, with examples:
Kubernetes Pod security:
Use containers built to run applications as non-root users
– Preventing privileged containers
– Denying container features frequently exploited to breakout, such as hostPID, hostIPC, hostNetwork, allowedHostPath
– Rejecting containers that execute as the root user or allow elevation to root
– Hardening applications against exploitation using security services such as SELinux, AppArmor, and seccomp
Network separation and hardening:
Authentication and authorization:
Log auditing:
Upgrading and application security practices:
Read the full Kubernetes Hardening Guidance document [PDF] from the NSA and CISA.