KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers have devised a way to block the recently disclosed PetitPotam attack vector that allows hackers to take control of a Windows domain controller easily.
Last month, security researcher GILLES Lionel disclosed a new method called PetitPotam that forces a Windows machine, including a Windows domain controller, to authenticate against a threat actor’s malicious NTLM relay server using the Microsoft Encrypting File System Remote Protocol (EFSRPC).
Threat actors would then relay this authentication request to a targeted domain’s Active Directory Certificate Services via HTTP., where the attacker would be given a Kerberos ticket-granting ticket (TGT), allowing them to assume the domain controller’s identity.
Also Read: 4 Reasons Why You Need an Actively Scanning Antivirus Software
After the vector was disclosed, researchers quickly began testing the method and illustrated how easy it was to dump credentials and take over a Windows domain.https://player.vimeo.com/video/578617278
Using this attack, a threat actor can take complete control over a Windows domain, including pushing out new group policies, scripts, and deploying malware on all devices, such as ransomware.
Last week, Microsoft released an advisory titled ‘Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS)‘ that explains how to mitigate NTLM relay attacks.
“To prevent NTLM Relay Attacks on networks with NTLM enabled, domain administrators must ensure that services that permit NTLM authentication make use of protections such as Extended Protection for Authentication (EPA) or signing features such as SMB signing,” explained Microsoft’s advisory.
“PetitPotam takes advantage of servers where Active Directory Certificate Services (AD CS) is not configured with protections for NTLM Relay Attacks. The mitigations outlined in KB5005413* instruct customers on how to protect their AD CS servers from such attacks.”
While Microsoft’s suggestions may prevent NTLM relay attacks, they do not provide any guidance on blocking PetitPotam, which can be used as a vector for other attacks.
“It can be used for different attacks too like NTLMv1 downgrade and relaying machine account on computers where this machine account is local admin,” Lionel told BleepingComputer when he first disclosed the attack vector.
Microsoft’s response to recent vulnerabilities, such as PetitPotam, SeriousSAM, and PrintNightmare have been very concerning for security researchers who feel that Microsoft is not doing enough to protect its customers.https://platform.twitter.com/embed/Tweet.html?creatorScreenName=BleepinComputer&dnt=false&embedId=twitter-widget-0&features=eyJ0ZndfZXhwZXJpbWVudHNfY29va2llX2V4cGlyYXRpb24iOnsiYnVja2V0IjoxMjA5NjAwLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X2hvcml6b25fdHdlZXRfZW1iZWRfOTU1NSI6eyJidWNrZXQiOiJodGUiLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X3NwYWNlX2NhcmQiOnsiYnVja2V0Ijoib2ZmIiwidmVyc2lvbiI6bnVsbH19&frame=false&hideCard=false&hideThread=false&id=1421846897262796800&lang=en&origin=https%3A%2F%2Fwww.bleepingcomputer.com%2Fnews%2Fmicrosoft%2Fwindows-petitpotam-attacks-can-be-blocked-using-new-method%2F&sessionId=ce3b0c7843740251630ce721bba6e7e66c44e28c&siteScreenName=BleepinComputer&theme=light&widgetsVersion=1890d59c%3A1627936082797&width=550px
The good news is that researchers have figured out a way to block the remote unauthenticated PetitPotam attack vector using NETSH filters without affecting local EFS functionality.
NETSH is a Windows command-line utility that allows administrators to configure network interfaces, add filters, and modify the Windows firewall configuration.
This weekend, Craig Kirby shared a NETSH RPC filter that blocks remote access to the MS-EFSRPC API, effectively blocking the unauthenticated PetitPotam attack vector.
According to security researcher Benjamin Delpy, you can use this filter by copying the following contents into a file called ‘block_efsr.txt’ and saving it on your desktop.
rpc
filter
add rule layer=um actiontype=block
add condition field=if_uuid matchtype=equal data=c681d488-d850-11d0-8c52-00c04fd90f7e
add filter
add rule layer=um actiontype=block
add condition field=if_uuid matchtype=equal data=df1941c5-fe89-4e79-bf10-463657acf44d
add filter
quitNow open an elevated command prompt and type the following command to import the filter using NETSH.
netsh -f %userprofile%\desktop\block_efsr.txtYou can verify that the filters have been added by running the following command:
netsh rpc filter show filterAfter running the command, netsh should display two filters, one for c681d488-d850-11d0-8c52-00c04fd90f7e and another for df1941c5-fe89-4e79-bf10-463657acf44d, as shown below.
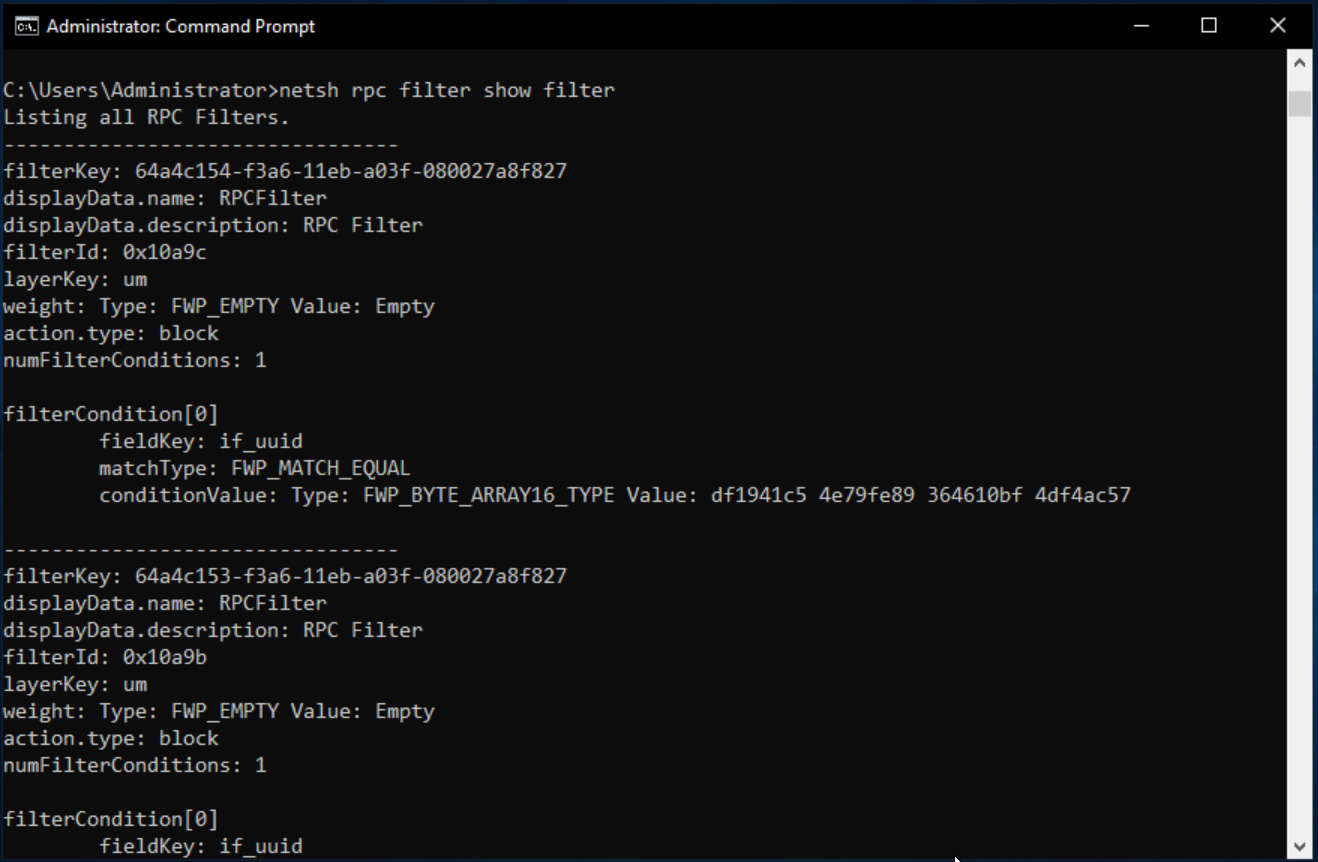
With these filters in place, the PetitPotam vector will no longer work, but EFS will continue to operate normally on the device.
If Microsoft ever fixes the API to prevent this vector, you can remove the filters using the following command:
netsh rpc filter delete filter filterkey=[key]The filterkey can be found when displaying the list of configured filters as described above.