KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Kaseya has warned customers that an ongoing phishing campaign attempts to breach their networks by spamming emails bundling malicious attachments and embedded links posing as legitimate VSA security updates.
“Spammers are using the news about the Kaseya Incident to send out fake email notifications that appear to be Kaseya updates. These are phishing emails that may contain malicious links and/or attachments,” the company said in an alert issued on Thursday evening.
“Do not click on any links or download any attachments claiming to be a Kaseya advisory. Moving forward, Kaseya email updates will not contain any links or attachments.”
While the company did not provide additional details regarding these attacks, the warning perfectly lines up with another series of malspam emails targeting Kaseya customers with Cobalt Strike payloads.
As BleepingComputer first reported, Malwarebytes Threat Intelligence researchers have recently discovered a series of phishing attacks trying to take advantage of the ongoing Kaseya ransomware crisis.
“A malspam campaign is taking advantage of Kaseya VSA ransomware attack to drop CobaltStrike,” Malwarebytes researchers said.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
“It contains an attachment named ‘SecurityUpdates.exe’ as well as a link pretending to be security update from Microsoft to patch Kaseya vulnerability!”
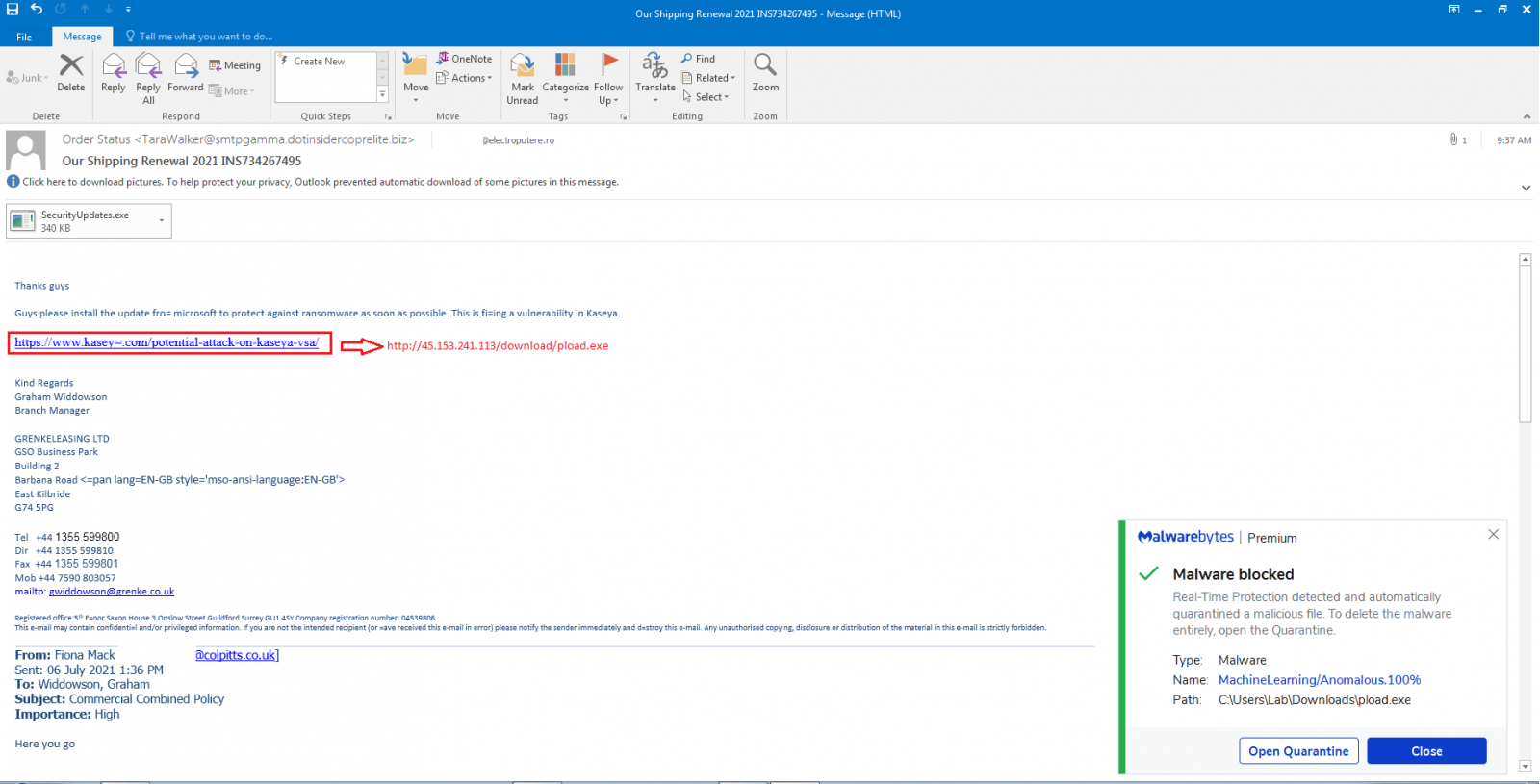
The attackers’ end goal is to deploy Cobal Strike beacons on the recipients’ devices to backdoor them and steal sensitive info or deliver more malware payloads.
Once the targets run the malicious attachment or download and execute the fake Microsoft update on their devices, the attackers gain persistent remote access to the now compromised systems.
In June, following the Colonial Pipeline attack, threat actors also used fake systems updates claiming to help block ransomware infections.
These two campaigns highlight that cybercriminals behind phishing attacks keep up with the latest news to push lures relevant to recent events to boost their campaigns’ success rates.
Given that Kaseya has so far failed to deploy a fix for the VSA zero-day exploited by REvil, some of its customers might fall for this campaign’s tricks in their effort to protect their networks from attacks.
The highly-publicized REvil ransomware attack that hit Kaseya and approximately 1,500 of their direct customers and downstream businesses makes for a perfect lure theme.
After the attack was disclosed, CISA and the FBI have shared guidance on how to deal with the attack’s aftermath, and the White House National Security Council is urging victims to follow the guidance issued by Kaseya and report incidents to the FBI.
Also Read: Compliance Course Singapore: Spotlight on the 3 Offerings
However, despite the attack’s massive reach, which has led to some calling the largest ransomware attack ever, multiple victims told BleepingComputer that their backups were not affected, and they are restoring systems rather than paying a ransom.
Victims who do ultimately pay REvil’s ransoms will likely only do so because their backups failed or they had no backups, to begin with.