KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Threat actors are trying to capitalize on the ongoing Kaseya ransomware attack crisis by targeting potential victims in a spam campaign pushing Cobalt Strike payloads disguised as Kaseya VSA security updates.
Cobalt Strike is a legitimate penetration testing tool and threat emulation software that’s also used by attackers for post-exploitation tasks and to deploy so-called beacons that allow them to gain remote access to compromised systems.
The end goal of such attacks is either that of harvesting and exfiltrating sensitive data or delivering second-stage malware payloads.
“Interestingly, 66 percent of all ransomware attacks this quarter involved red-teaming framework Cobalt Strike, suggesting that ransomware actors are increasingly relying on the tool as they abandon commodity trojans,” the Cisco Talos Incident Response (CTIR) team said in a September quarterly report.
The malspam campaign spotted by Malwarebytes Threat Intelligence researchers uses two different tactics to deploy the Cobalt Strike payloads.
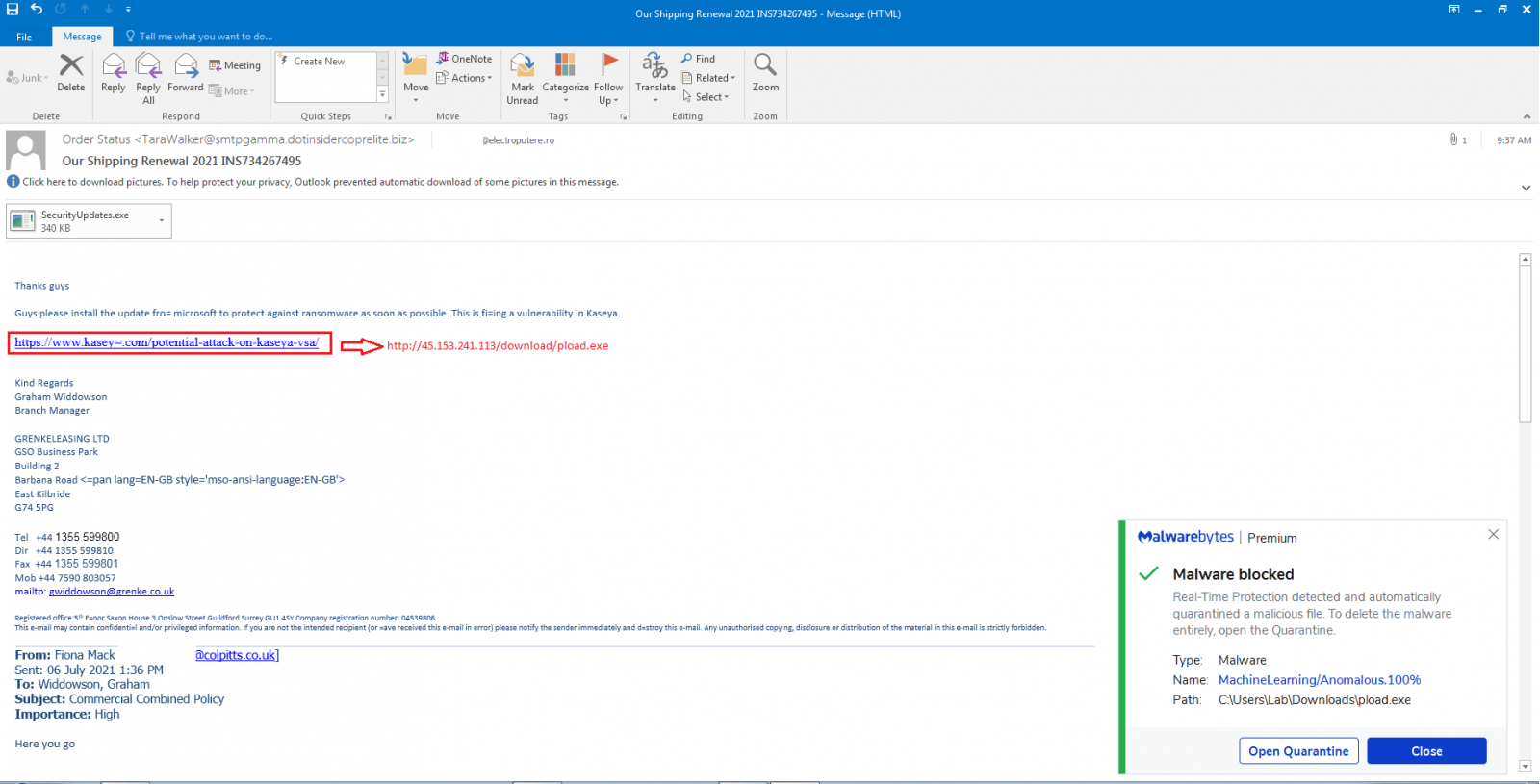
Malicious emails sent as part of this malspam campaign come with a malicious attachment and an embedded link designed to look like a Microsoft patch for the Kaseya VSA zero-day exploited in the REvil ransomware attack.
“A malspam campaign is taking advantage of Kaseya VSA ransomware attack to drop CobaltStrike,” the Malwarebytes Threat Intelligence team said.
Also Read: The 5 Phases of Penetration Testing You Should Know
“It contains an attachment named ‘SecurityUpdates.exe’ as well as a link pretending to be security update from Microsoft to patch Kaseya vulnerability!”
The attackers gain persistent remote access to the targets systems once they run the malicious attachment or download and launch the fake Microsoft update on their devices.
Last month, threat actors also used fake systems updates claiming to help detect and block ransomware infections following the Colonial Pipeline attack.
Just as with this month’s malspam campaign, the June phishing campaign was also pushing malicious payloads designed to deploy the Cobalt Strike penetration testing tool, which would have allowed the attackers to compromise the recipients’ systems.
As INKY researchers who spotted the attacks said, the phishing emails came with a deadline for installing the fake updates to add a sense of urgency.
The payload download pages were also customized using the target company’s graphics to make them appear trustworthy.
These two campaigns highlight that threat actors in the phishing business keep track of the latest news for pushing lures relevant to recent events to boost their campaigns rates of success.
The highly-publicized REvil ransomware attack that hit the Kaseya MSP software provider and approximately 60 out of 35,000 of their direct customers and 1,500 out of 1,000,000 downstream businesses makes for a perfect lure theme.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
Since Kaseya says that it failed to deploy a fix for the VSA zero-day exploited by REvil, many of its customers might fall for this pishing campaign’s tricks in their effort to protect their networks from attacks.