KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A threat actor uses an unusual attachment to bypass security software that is a double-edged sword that may work against them.
As secure email gateways and security software become more advanced and adapt to ever-changing phishing campaigns, threat actors resort to more unusual file formats to bypass detection.
In the past, phishing scams switched to unusual attachments such as ISO files or TAR files which are not commonly found as email attachments.
However, as threat actors adopt new and unusual attachments, cybersecurity companies add further detections to block them.
In a new report by Trustwave, researchers explain how a threat actor has begun to utilize WIM (Windows Imaging Format) attachments to distribute the Agent Tesla remote access trojan.
Also Read: The 5 Phases of Penetration Testing You Should Know
“All the WIM files we gathered from our samples contain Agent Tesla malware. This threat is a Remote Access Trojan (RAT) written in .Net which can take full control over a compromised system and can exfiltrate data via HTTP, SMTP, FTP, and Telegram,” explains Trustwave security researcher Diana Lopera in the report.
These campaigns start with phishing emails that pretend to be shipping information from DHL or Alpha Trans, as shown below.
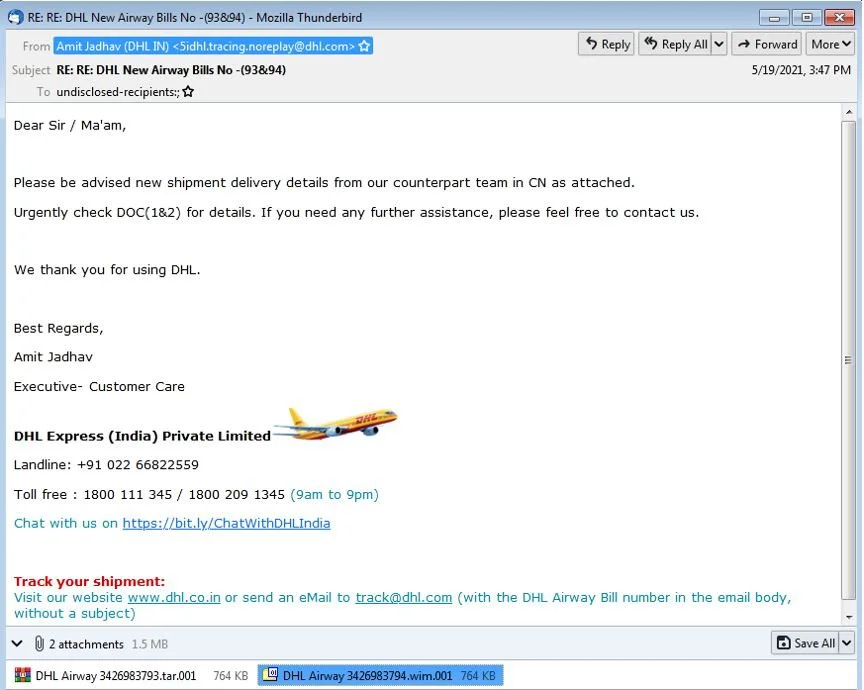
Included in the emails are .wim attachments (sometimes ending with .wim or .wim.001) designed to bypass security software.
Windows Imaging Format (WIM) files are a file-based disk image format that Microsoft developed to aid in deploying Windows Vista and later operating systems.
WIM files are used to pack an entire drive, with all of its files and folders, into a single file for easy distribution.
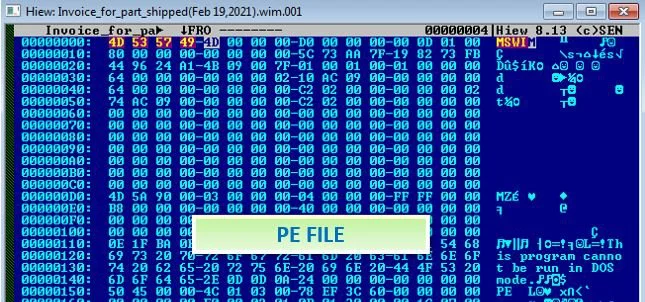
As you can see below, when opening one of these WIM attachments in a hex editor, it clearly shows that an executable is enclosed within it.
However, while WIM files may be less likely to be detected, phishing campaigns that use them have a bigger problem as Windows has no built-in mechanism to open a WIM file.
Therefore, when a user attempts to open the attachment in Windows, they will just be greeted with a message asking them to select the program to open the file, as shown below.
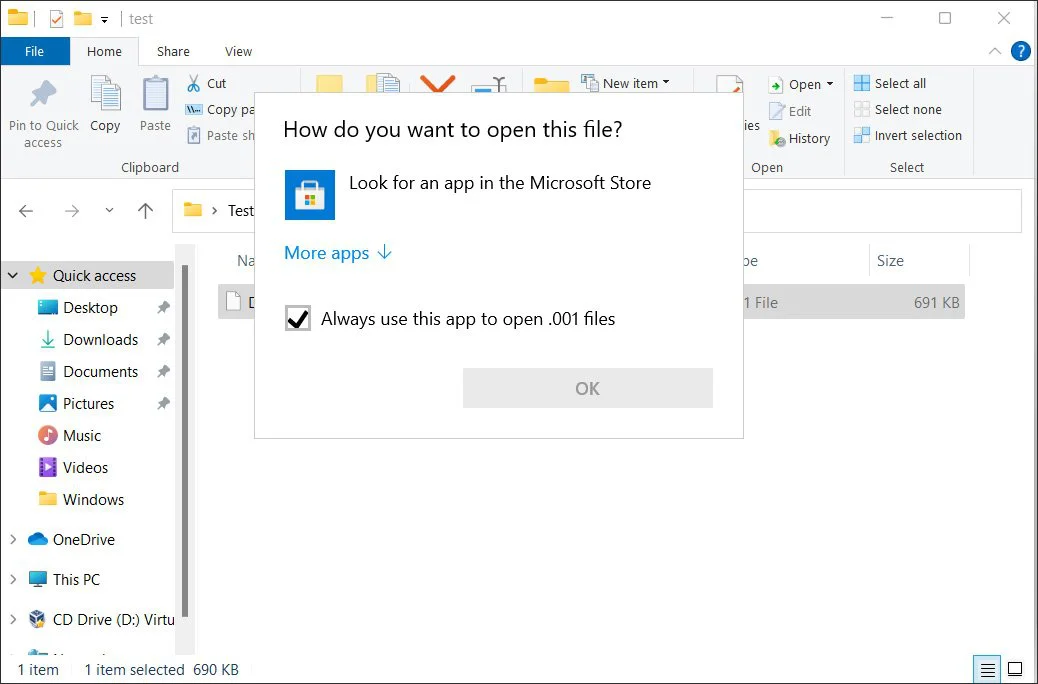
This file format would then require a recipient to go out of their way and extract the file using a program like 7-zip and then double-click on the file within it, which is highly unlikely to happen.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
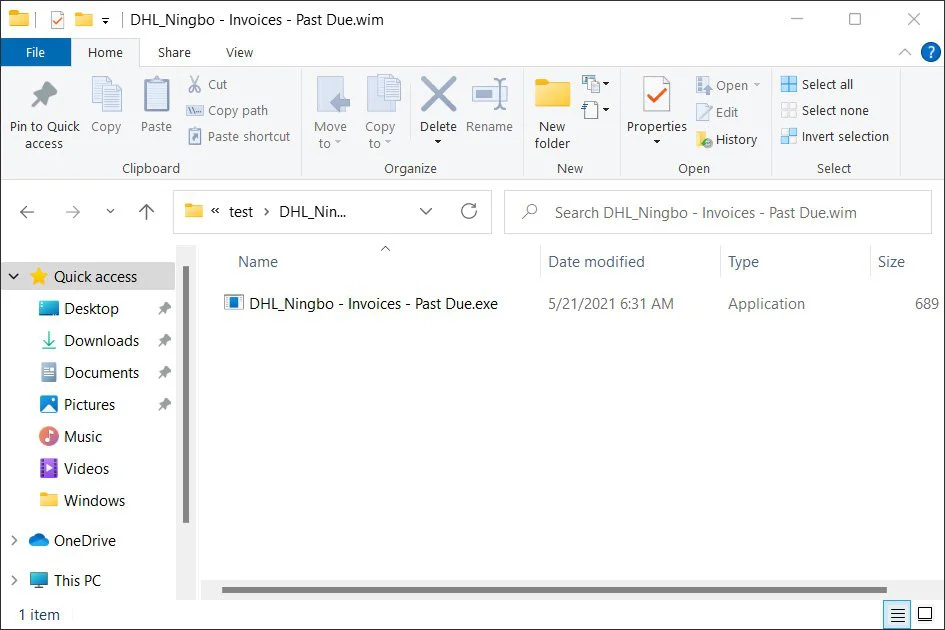
While using an uncommon attachment may bypass some security filters, they are also likely a double-edged sword for the threat actor.
This is because the files will not be opened by most devices that do not have specialized programs, such as 7-zip installed, and recipients who will make that extra effort to extract the files.
“Encapsulating malware in an unusual archive file format is one of the common ways to bypass gateways and scanners. However, this strategy also poses a hurdle – the target system must recognize the file type or at least have a tool which can unpack and process the file,” says Lopera.
“In contrast to the more popular .IMG and .ISO disk image files, WIM files are not supported by Windows built-in ability to mount disk image files. Moreover, the other popular archive utilities WinRAR and WinZip do not recognize the WIM disk image. WIM files can be processed with the widely used 7Zip.”
Secure email gateways will soon block these attachments if not already done. However, if you do run into an email with a WIM attachment, simply delete it as no legitimate email will use this file format.