KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






A new report analyzes the recently released Avaddon ransomware decryption keys to shed light on the types of victims targeted by the threat actors and potential revenue they generated throughout their operation.
On June 11th, the Avaddon ransomware gang decided to shut down their operation. As part of the shutdown, the ransomware gang anonymously shared their victims’ decryption keys with BleepingComputer.
Using these keys, Emsisoft created a decryptor that allows victims to recover their files for free.
These decryption keys were released as two text files where each victim contained a numeric ID and two base64 encoded cryptographic keys that could decrypt a victim’s files.
For many of these keys, the ransomware gang also included an identifier of some sort that could be a Windows domain, the logged-in user’s name, or some other identifier.
While some of these IDs reveal significant cyberattacks against previously unknown corporate targets, BleepingComputer does not intend to report on these victims.
After analyzing the unique identifiers attached to the Avaddon decryption keys, cybersecurity firm Advanced Intel has released anonymous details about the victims targeted by the ransomware group.
“Today we shed light on this lost and hidden criminal empire using unique datasets – the full list of Avaddon victims ever targeted by the group over the year of its existence,” says Advanced Intel’s report.
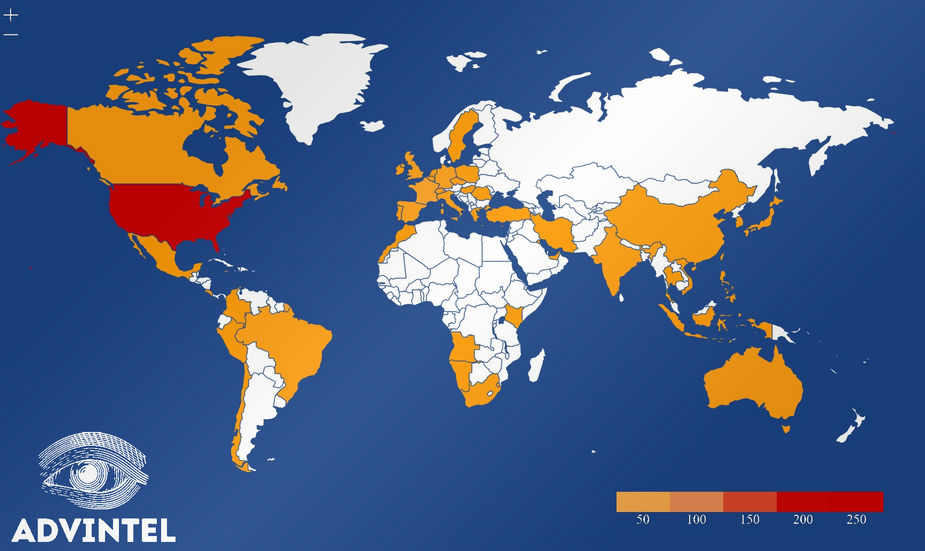
Of the victims targeted by Avaddon, most organizations resided in the USA, followed by Canada, and then the rest of the world. As noted by the map, there were no known victims in Russia or other CIS countries, as is typical for ransomware gangs.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
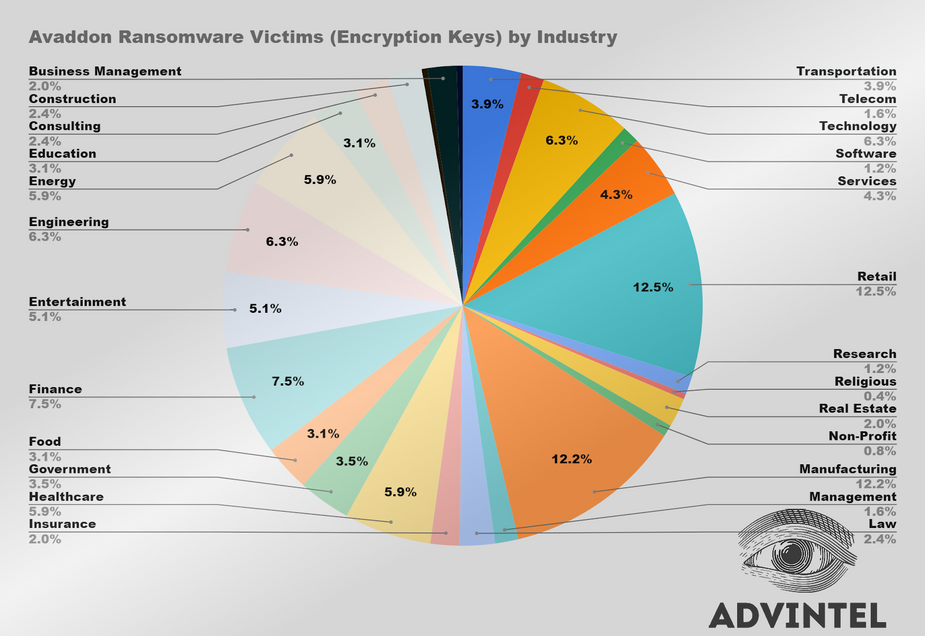
The top three industries targeted by Avaddon were Retail (12.5%), Manufacturing (12.2%), and (6.3%), and Finance (7.5%). However, Avaddon targetted a wide range of companies, and while the threat actors targeted some industries more than others, these were likely still opportunistic attacks.
Finally, using the list of known victims, Advanced Intel grouped them by their yearly revenue, showing that over 50% earned income below $10 million.
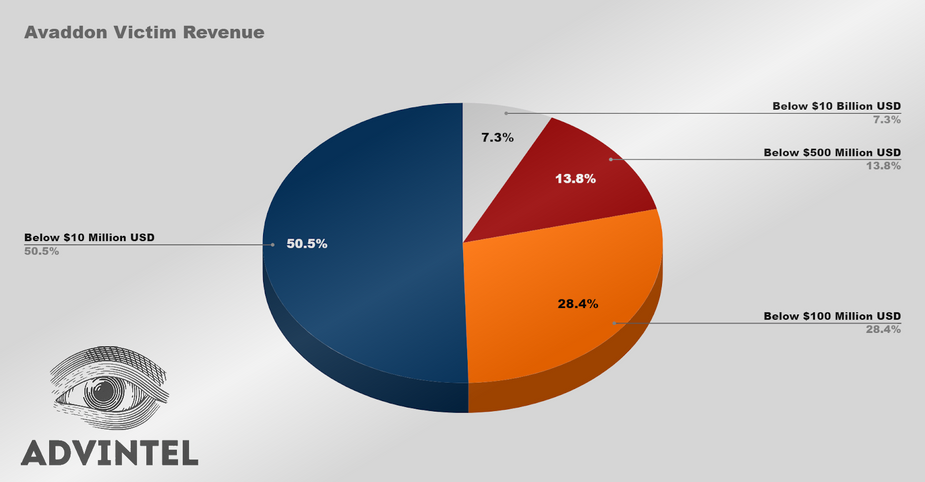
On average, Avaddon’s victims’ revenue are:
An Advanced Intel source states that Avaddon uses a “5×5” rule when determining ransom demands.
“The most common calculation which according to our sensitive and credible source intelligence as used by Avaddon was a so-called “5×5” rule when 5% of the annual revenue is used to start the negotiations, with annual revenue estimated as one-fifth of the total revenue,” explained the report.
Also Read: How to Comply with PDPA: A Checklist for Businesses
“In other words, for a victim which has a total revenue of $7 Million USD, the starting ransom price will be $70,000 USD. Typically, Avaddon dropped the price during the bargaining, and the end ransom was around $50,000 USD for a successful operation.”
Using this information and internal intelligence based on known victims, Advanced Intel believes that Avaddon’s total earnings are of approximately $87 million.
“Feedback from the top-tier underground community members who reportedly worked with Avaddon, as well as other collections from the DarkWeb though which we were able to build an approximate patter for each 3d victim paying the ransom,” Advanced Intel’s Yelisey Boguslavskiy told BleepingComputer.
“This pattern correlated with our experience of engaging in mitigation of ransomware incidents.”
It is not clear why Avaddon shut down its operation, but it is believed to be due to the increased pressure exerted by the US government and law enforcement.
While ransomware has been a problem since 2012, it has not been until the past two years that law enforcement has successfully disrupted these operations.
This disruption has been successful as it targets the affiliates, infrastructure, and payments rather than the ransomware operation’s core developers.