KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







E-commerce platform Mercari has disclosed a major data breach incident that occurred due to exposure from the Codecov supply-chain attack.
Mercari is a publicly traded Japanese company and an online marketplace that has recently expanded its operations to the United States and the United Kingdom.
The Mercari app has scored over 100 million downloads worldwide as of 2017, and the company is the first in Japan to reach unicorn status.
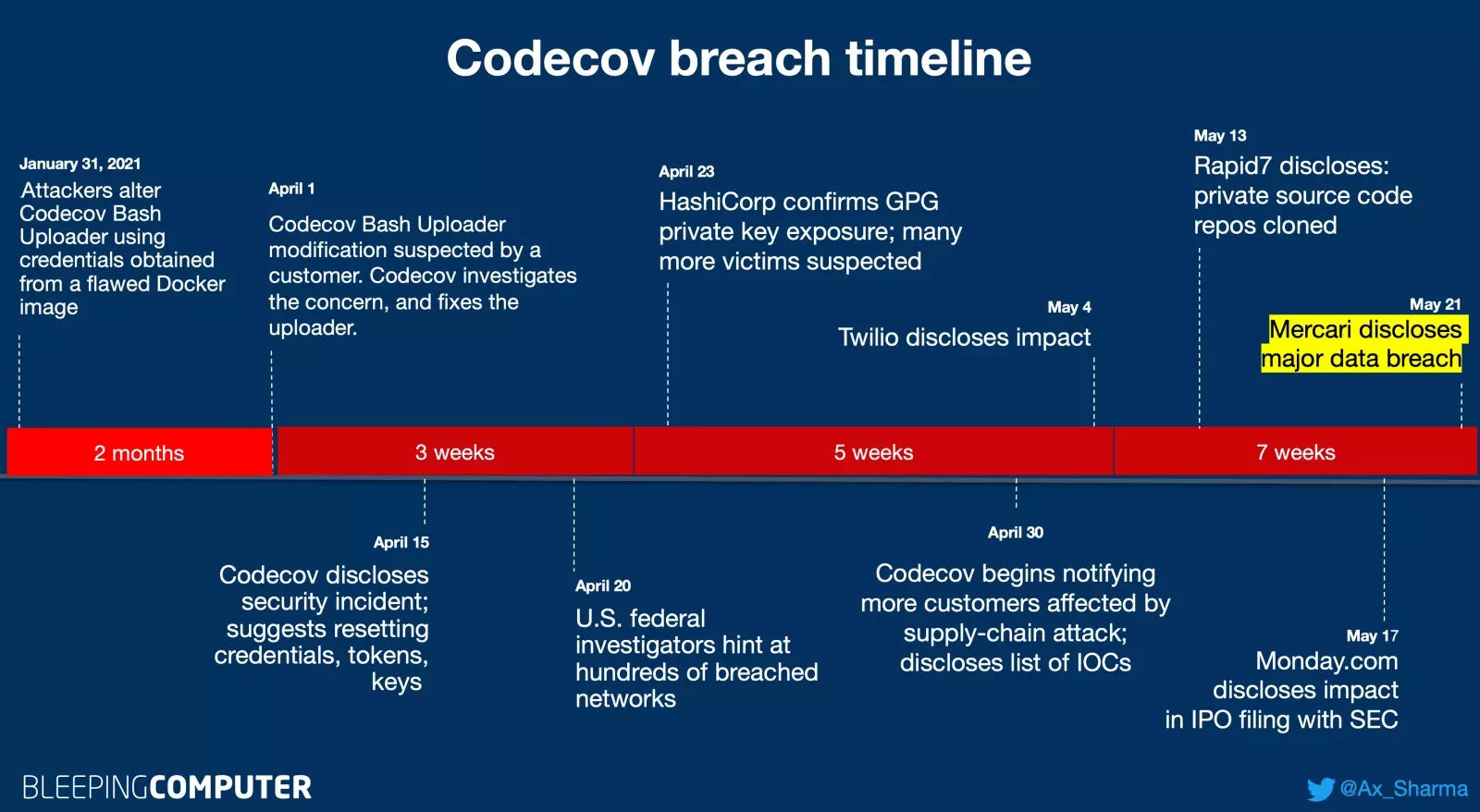
As earlier reported by BleepingComputer, popular code coverage tool Codecov had been a victim of a supply-chain attack that lasted for two months.https://www.ad-sandbox.com/static/html/sandbox.html
During this two-month period, threat actors had modified the legitimate Codecov Bash Uploader tool to exfiltrate environment variables (containing sensitive information such as keys, tokens, and credentials) from Codecov customers’ CI/CD environments.
Using the credentials harvested from the tampered Bash Uploader, Codecov attackers reportedly breached hundreds of customer networks.
Also Read: Considering Enterprise Risk Management Certification Singapore? Here Are 7 Best Outcomes
Today, e-commerce giant Mercari has disclosed major impact from the Codecov supply-chain attack on its customer data.
The company has confirmed that tens of thousands of customer records, including financial information, were exposed to external actors due to the Codecov breach.
After concluding their investigation today, May 21st, Mercari states that the compromised records include:
Mercari has illustrated the attack and how this data was exposed to third-party actors in the following infographic:
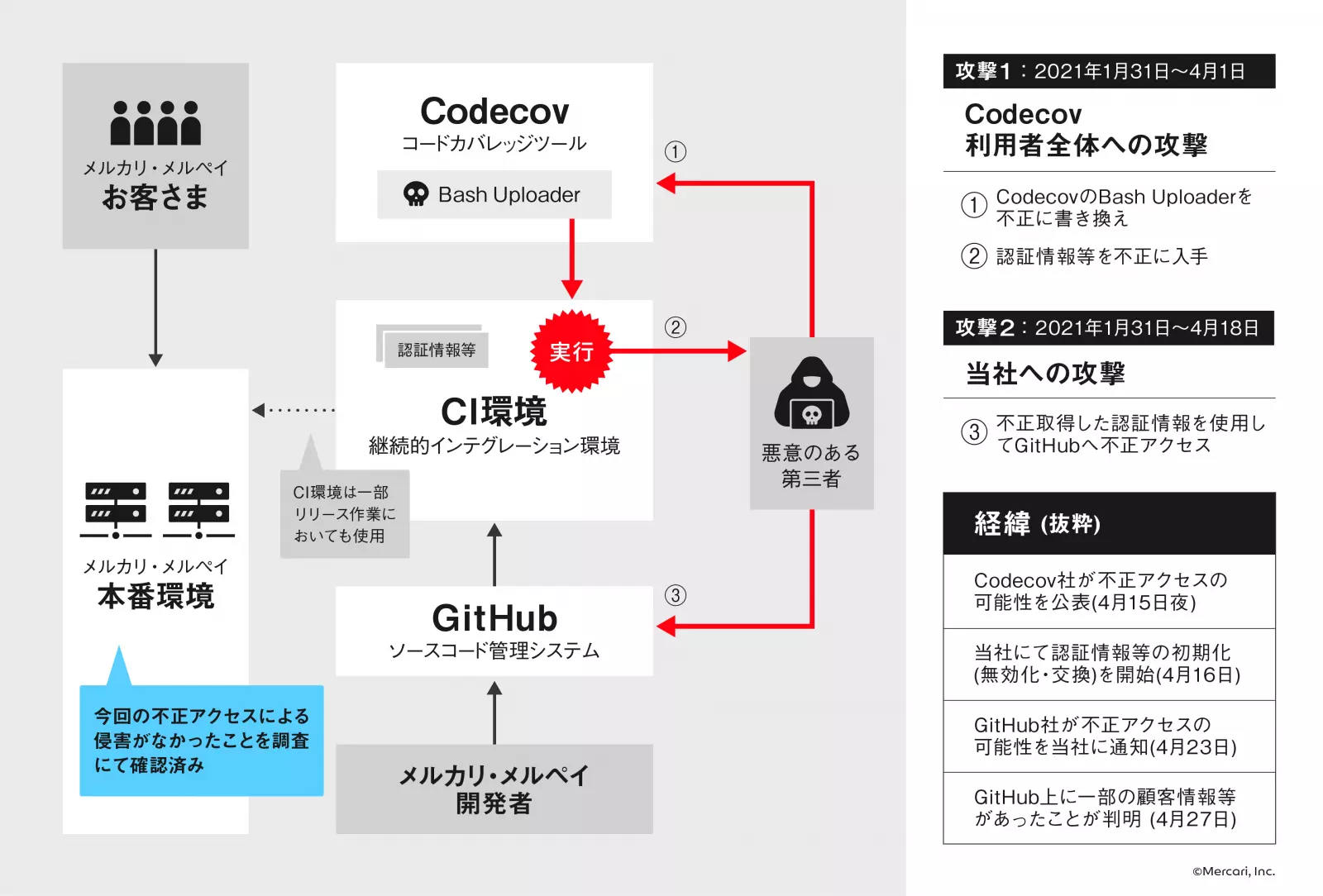
Mercari became aware of the impact from the Codecov breach shortly after Codecov’s initial disclosure made mid-April.
On April 23rd, GitHub also notified Mercari of suspicious activity related to the incident seen on Mercari’s repositories.
The same day, Mercari began digging deeper and requested GitHub for detailed access logs.
Eventually, Mercari staff determined that a malicious third party had acquired and misused their authentication credentials, accessed Mercari’s private repositories (including source code), and obtained further unauthorized access to its systems between April 13th and April 18th.
On discovery of this attack, Mercari immediately deactivated the compromised credentials and secrets and continued investigating the full impact of the breach.
On April 27, Mercari discovered that some of its customer information and source code had been illicitly accessed by unauthorized external parties.
The company says it had to wait on disclosing the data breach until today because its investigation activities had been ongoing. And until any security weaknesses could be completely identified and remediated, the company risked suffering further attacks and damage.
Mercari has now concluded its investigation and hence come forward with the detailed disclosure today.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
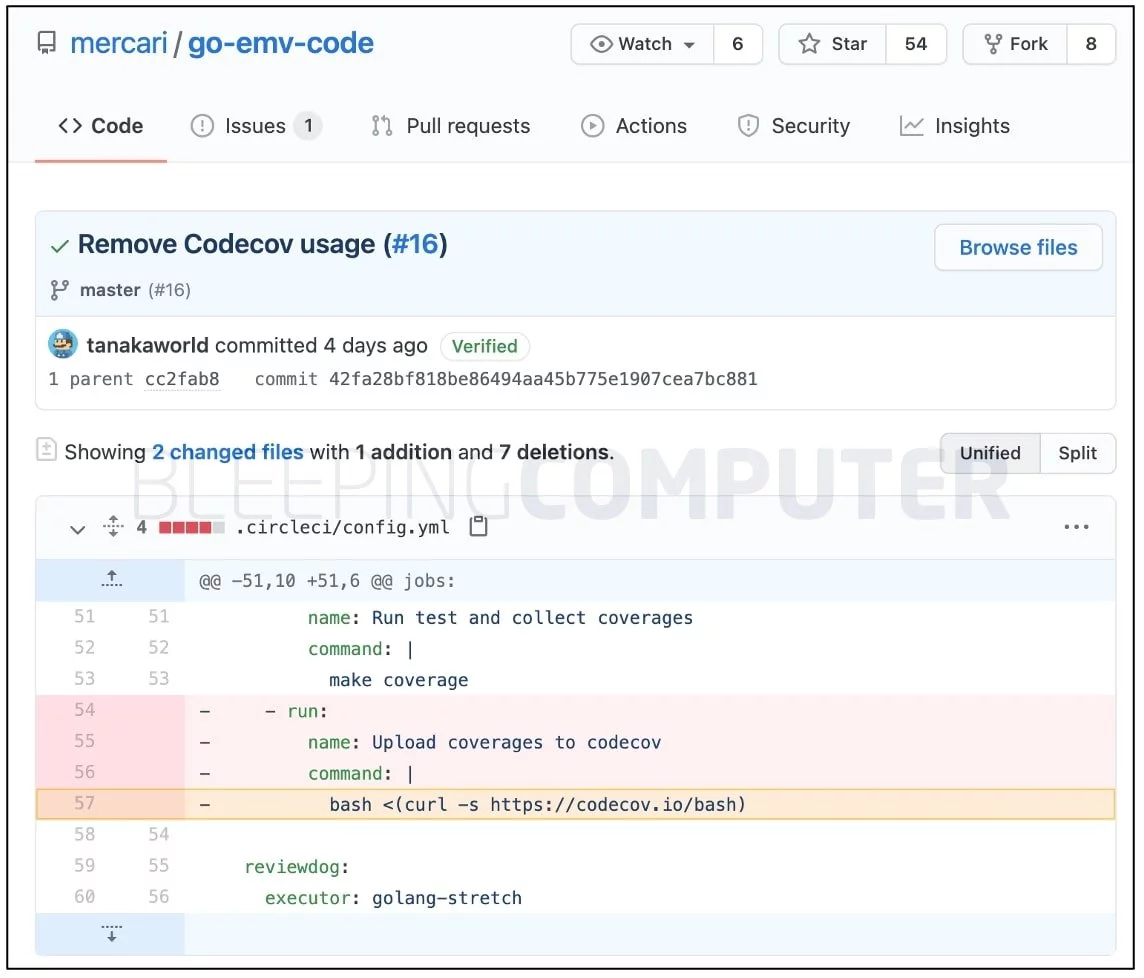
As observed by BleepingComputer, this week, the e-commerce giant also began purging its GitHub repositories from using Codecov anywhere:

Prior to this, multiple Mercari repositories used the Codecov Bash Uploader that had been compromised, as confirmed by BleepingComputer:
Mercari has individually contacted the people whose information has been compromised, and also notified relevant authorities, including the Personal Information Protection Commission, Japan, of this data breach:
“At the same time as this announcement, we will promptly provide individual information to those who are subject to the information leaked due to this matter, and we have also set up a dedicated contact point for inquiries regarding this matter.”
“In the future, we will continue to implement further security enhancement measures and investigate this matter while utilizing the knowledge of external security experts, and will promptly report any new information that should be announced.”
“We sincerely apologize for any inconvenience and concern caused by this matter,” says Mercari in a rough translation of its original press release.
Today’s disclosure comes after multiple companies have recently come forward with the impact of the Codecov supply-chain attack on their private repositories. These include software manufacturer HashiCorp, cloud communications platform Twilio, cloud services provider Confluent, insurance company Coalition, U.S. cybersecurity firm Rapid7, and workflow management platform Monday.com.
Last month, Codecov also began sending additional notifications to the impacted customers and disclosed a thorough list of Indicators of Compromise (IOCs), i.e. attacker IP addresses associated with this supply-chain attack.
Codecov users should scan their CI/CD environments and networks for any signs of compromise, and as a safeguard, rotate any and all secrets that may have been exposed.