KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Technical documentation and proof-of-concept exploit (PoC) code is available for a high-severity vulnerability in Microsoft Exchange Server that could let remote attackers execute code on unpatched machines.
The flaw is for one of the four that the National Security Agency (NSA) reported to Microsoft and received a fix in April.
Despite being the least severe of the bunch and requiring authentication, the risk that CVE-2021-28482 poses to companies is not to be neglected.
A technical write-up is available since April 26 from security researcher Nguyen Jang, who released in the past a short-lived PoC exploit for ProxyLogon vulnerabilities.
Jang’s blog post, while in Vietnamese, should pose no challenge in understanding the technical details to achieve remote code execution in an authenticated Exchange Server environment.
Yesterday, the researcher also published on GitHub demo exploit for CVE-2021-28482 written in Python. The validity of the code has been confirmed by Will Dormann, a vulnerability analyst for CERT/CC.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
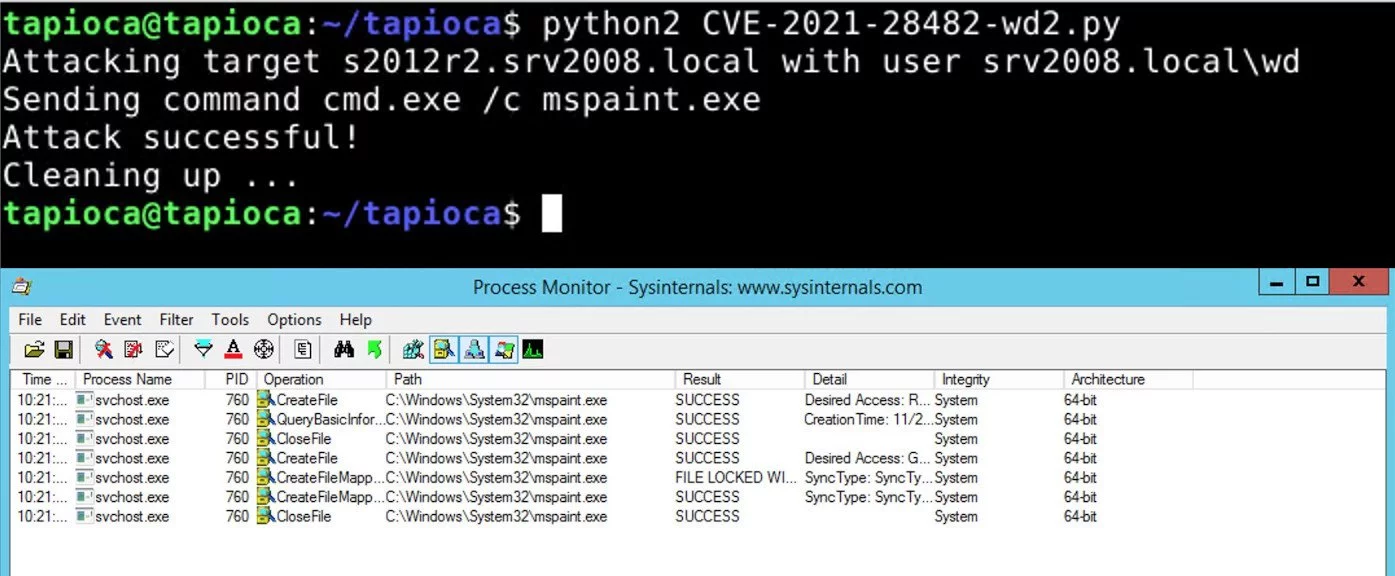
Dormann notes that attackers can exploit this deserialization vulnerability if they are authenticated on an on-premise Exchange Server instance that does not run Microsoft’s April updates.
Between the ProxyLogon vulnerabilities exploited since the beginning of the year, months before Microsoft released a patch, and the set reported by the NSA, companies rushed to update their Exchange servers at an impressively quick rate.
The high patch rate and the need for authentication lower the risk of compromise but do not eliminate it, though.
“But if anybody STILL doesn’t have April’s Exchange patches installed, if you can imagine an AUTHENTICATED attacker is a possibility, then assume CVE-2021-28482 was used” – Will Dormann
The vulnerability analyst told BleepingComputer that even if this bug is not as serious as ProxyLogon, since it does not allow en-masse scanning or exploitation, a real-life scenario for leveraging it exists:
But, any Exchange instance where a single user has a password that has been leaked, or any organization that has a single malicious or even just compromised insider is at risk if they have not installed April’s Exchange update.
Mass exploitation of an unauthenticated vulnerability leading to remote code execution should be the most powerful motivation for a company to install the latest patches for Exchange Server.
Also Read: The DNC Singapore: Looking At 2 Sides Better
Dormann said that anyone running on-premise machines without Microsoft’s April updates “is in trouble,” more so if the server is exposed to the public internet.

Established in 2018, Privacy Ninja is a Singapore-based IT security company specialising in data protection and cybersecurity solutions for businesses. We offer services like vulnerability assessments, penetration testing, and outsourced Data Protection Officer support, helping organisations comply with regulations and safeguard their data.
Singapore
7 Temasek Boulevard,
#12-07, Suntec Tower One,
Singapore 038987
Latest resources sent to your inbox weekly
© 2025 Privacy Ninja. All rights reserved
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!

Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!
