KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Attackers are promoting sites impersonating the Microsoft Store, Spotify, and an online document converter that distribute malware to steal credit cards and passwords saved in web browsers.
The attack was discovered by cybersecurity firm ESET who issued a warning yesterday on Twitter to be on the lookout for the malicious campaign.
In a conversation with Jiri Kropac, ESET’s Head of Threat Detection Labs, BleepingComputer learned that the attack is conducted through malicious advertising that promotes what appears to be legitimate applications.
For example, one of the advertisements used in this attack promotes an online Chess application, as shown below.

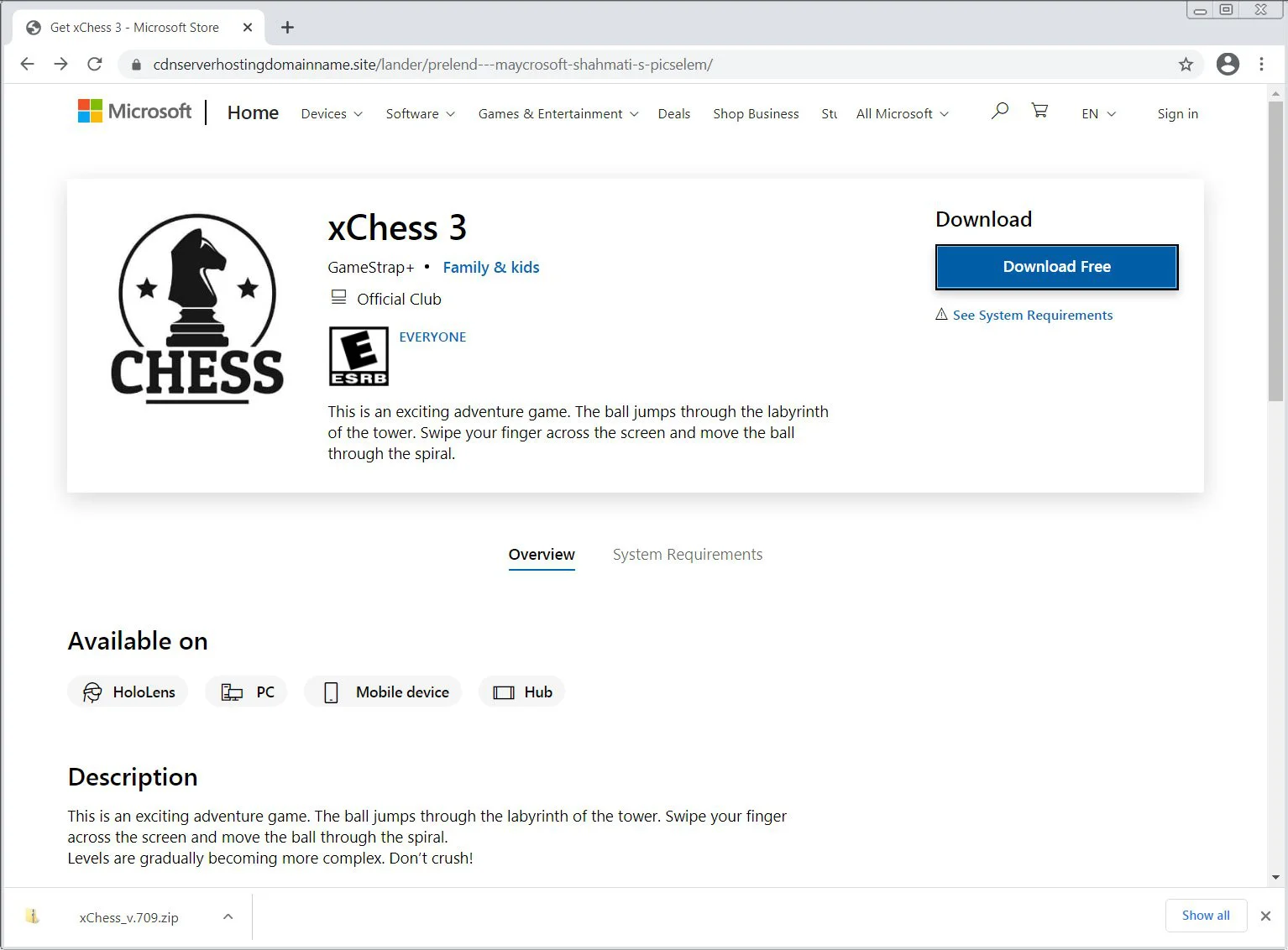
However, when users click on the ad, they are brought to a fake Microsoft Store page for a fake ‘xChess 3’ online chess application, which is automatically downloaded from an Amazon AWS server.
The downloaded zip file is named ‘xChess_v.709.zip’ [VirusTotal], which is actually the the ‘Ficker’, or ‘FickerStealer,’ information-stealing malware in disguise, as shown by this Any.Run report created by BleepingComputer.
Also Read: The DNC Singapore: Looking At 2 Sides Better
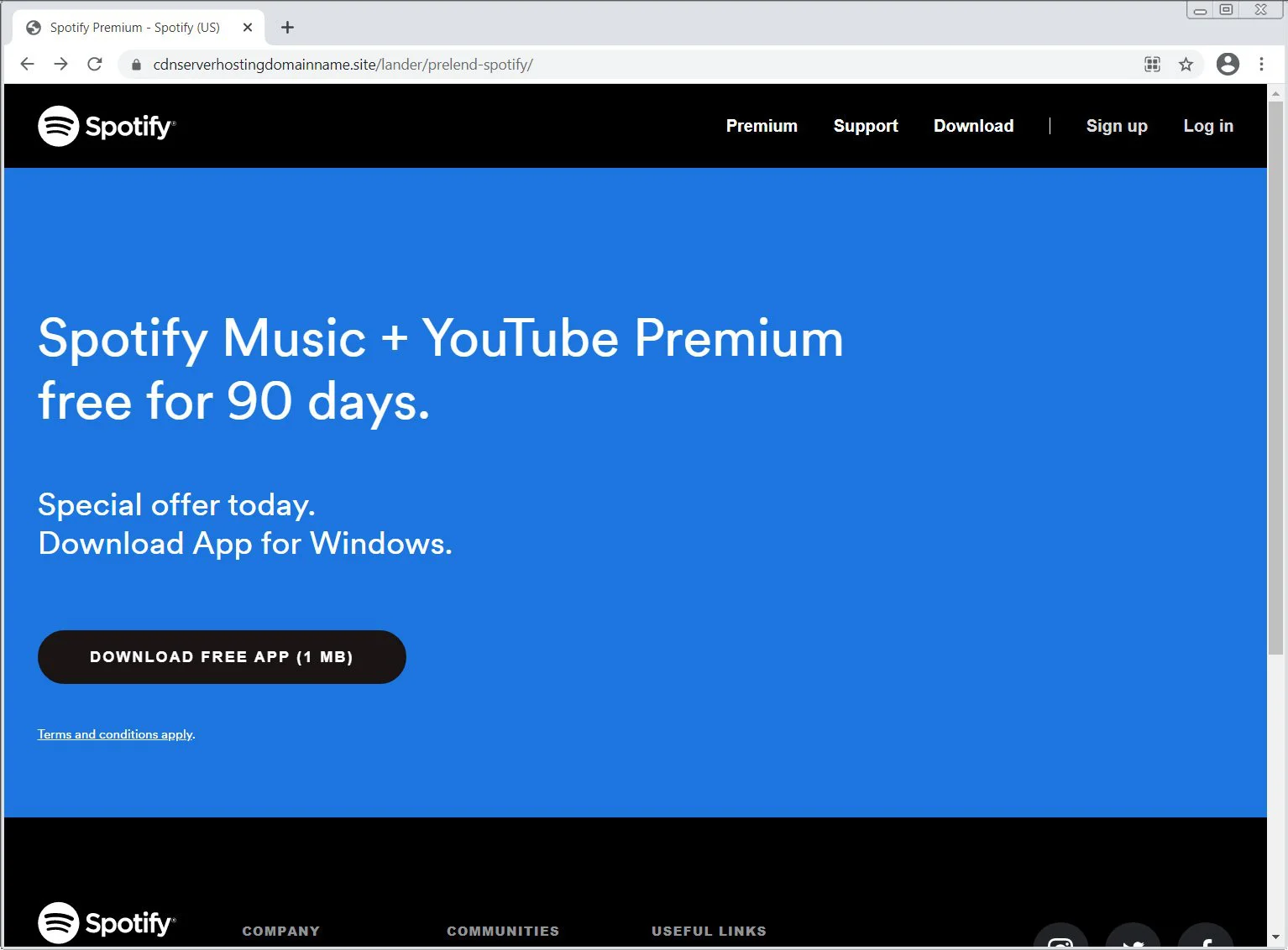
Other advertisements from this malware campaign pretend to be for Spotify (shown below) or an online document converter. When visited, their landing pages will also automatically download a zip file containing the Ficker malware.
Once a user unzips the file and launches the executable, instead of being greeted by a new online Chess application or the Spotify software, the Ficker malware will run and begin stealing the data stored on their computer.
Ficker is an information-stealing Trojan released on Russian-speaking hacker forums in January when the developer began renting out the malware to other threat actors.
In a forum post, the developer describes the malware’s capabilities and allows other threat actors to rent the software from anyone from one week up to six months.
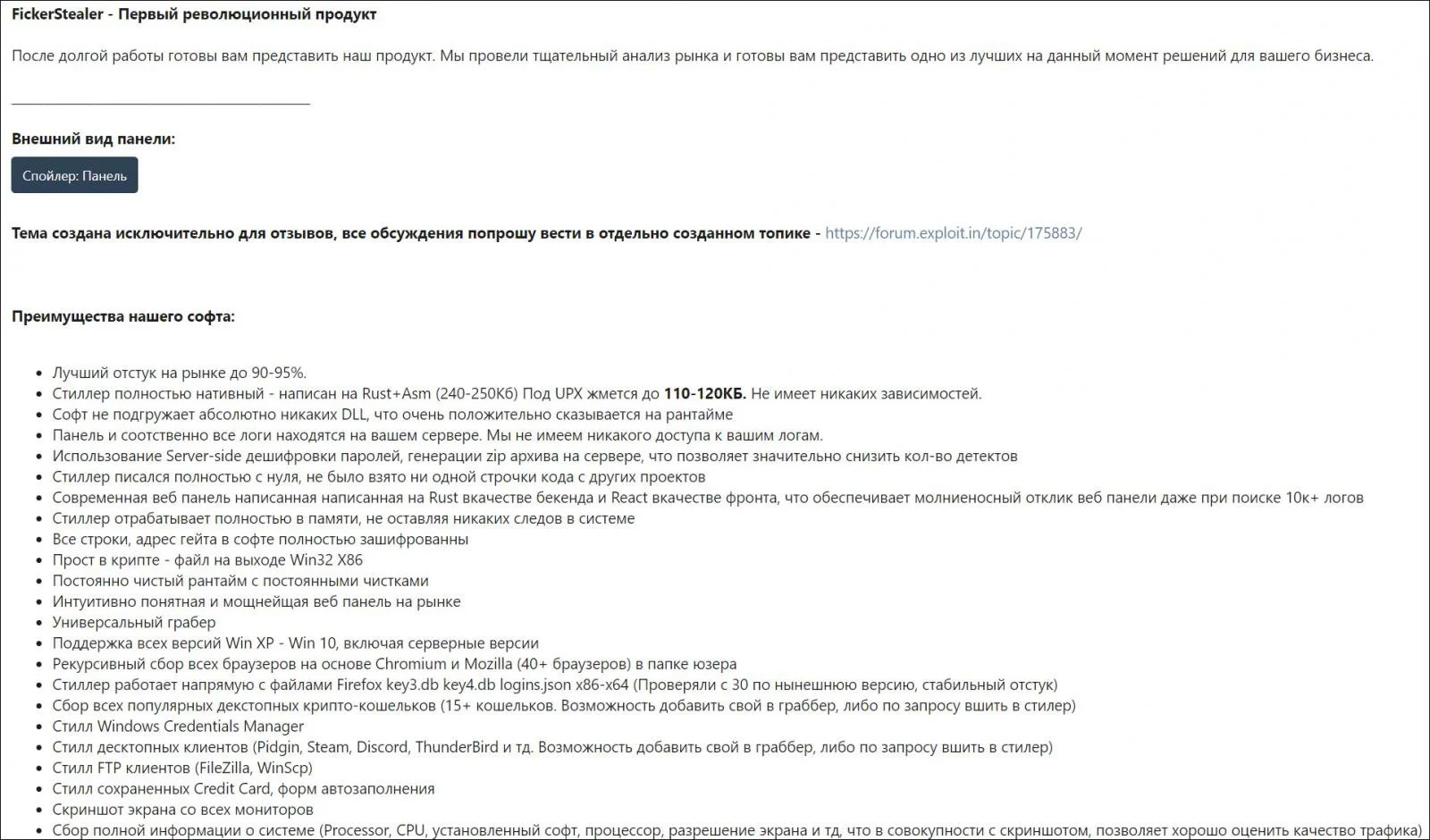
Using this malware, threat actors can steal saved credentials in web browsers, desktop messaging clients (Pidgin, Steam, Discord), and FTP clients.
In addition to stealing passwords, the developer claims the malware can steal over fifteen cryptocurrency wallets, steal documents, and take screenshots of the active applications running on victims’ computers.
This information is then compiled into a zip file and transmitted back to the attacker, where they can then extract the data and use it for other malicious activities.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
Due to the Ficker malware’s extensive functionality, victims of this campaign should immediately change their online passwords, check firewalls for suspicious port forwarding rules, and perform a thorough antivirus scan of your computer to check for additional malware.