KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has pushed out a new update for their Microsoft Safety Scanner (MSERT) tool to detect web shells deployed in the recent Exchange Server attacks.
On March 2nd, Microsoft disclosed that four Exchange Server zero-day vulnerabilities were being used in attacks against exposed Outlook on the web (OWA) servers. These vulnerabilities are tracked as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065.
Known as ‘ProxyLogon,’ these vulnerabilities are being used by Chinese state-sponsored threat actors to steal mailboxes, harvest credentials, and deploy web shells to access the internal network.
When Microsoft disclosed these attacks, they had released updated signatures for Microsoft Defender that will detect the web shells installed using the zero-day vulnerabilities.
These web shells are detected using the following names by Microsoft Defender:
For organizations not using Microsoft Defender, Microsoft has added the updated signatures to their Microsoft Safety Scanner standalone tool to help organizations find and remove web shells used in these attacks.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
Microsoft Safety Scanner, also known as the Microsoft Support Emergency Response Tool (MSERT), is a standalone portable antimalware tool that includes Microsoft Defender signatures to scan for and remove detected malware.
MSERT is an on-demand scanner and will not provide any real-time protection. Therefore, it should only be used for spot scans and not relied upon as a full-fledged antivirus program.
Furthermore, MSERT will automatically delete any detected files and not quarantine them if you do not start the program with the /N argument, as in msert.exe /N. To scan for web shellsand not delete them, you can also use use the PowerShell script described at the end of the article.
The Microsoft Safety Scanner can be downloaded as either a 32-bit or 64-bit executable and used to perform spot scans of a machine as needed.
After launching the program, agree to the license agreements, and you will be shown a screen asking what type of scan you would like to perform.
Microsoft recommends that you select the ‘Full scan’ option to scan the entire server.
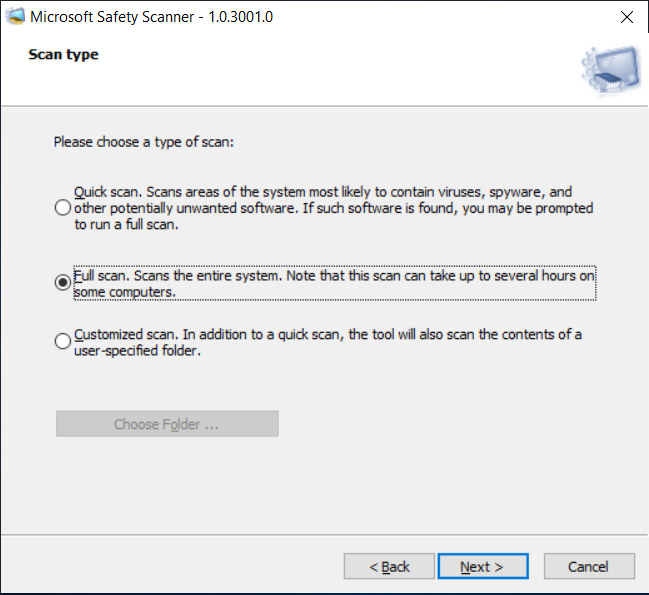
As the full scan can take a long time depending on the size of your install, Microsoft also states you can perform a ‘Customized scan’ against each of the following folders:
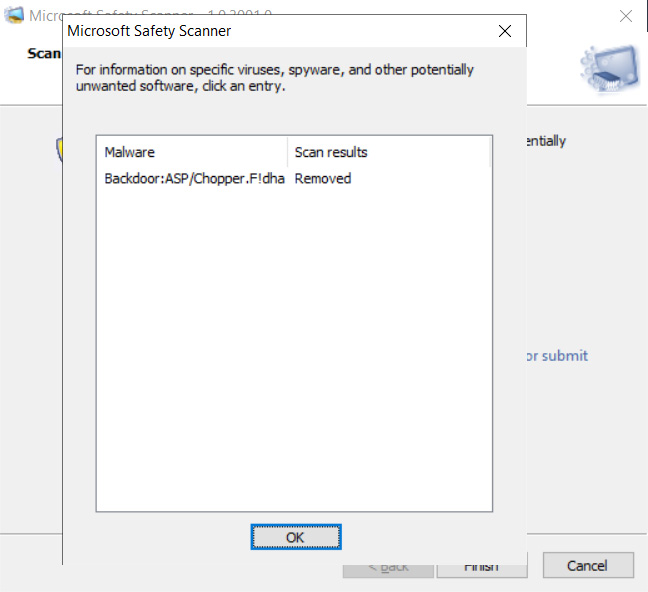
After the scan is finished, MSERT will report what files have been removed and their definition name.
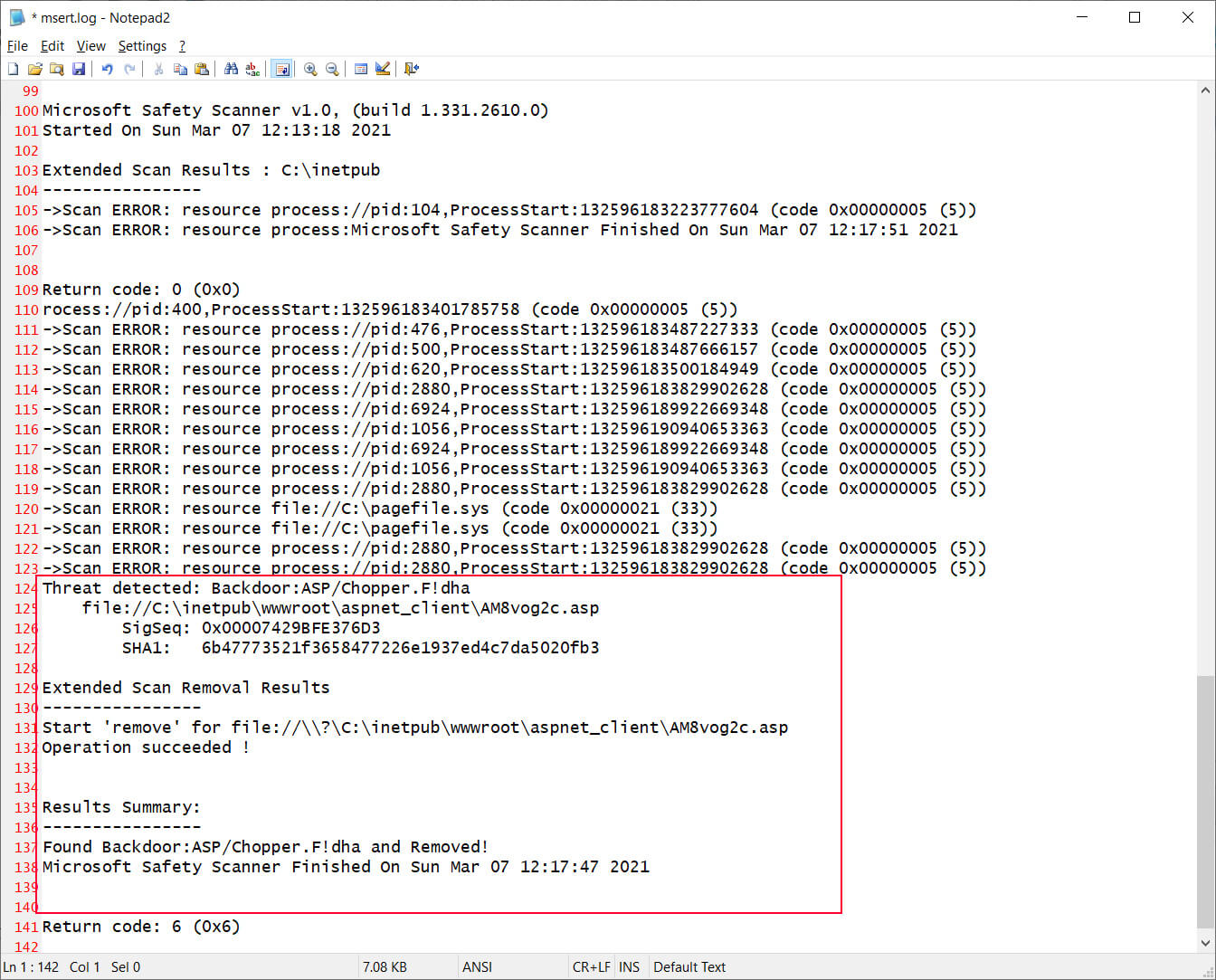
For more detailed information on what files were removed, you can consult the %SYSTEMROOT%\debug\msert.log file, as shown below.
When done using MSERT, you can uninstall the tool simply by deleting the msert.exe executable.
If you would like to scan for web shells without removing them, you can use a new PowerShell script named detect_webshells.ps1 created by CERT Latvia.
“Initial activity during January 2021 was attributed to HAFNIUM, however since then other threat actors got hold of these exploits and started using them. Prior to public disclosure & patches being published by Microsoft (since 27 February or so) publically exposed Exchange servers started being exploited indiscriminately.”
“As such, installing latest Exchange updates soon after Microsoft published them did not fully mitigate the risk of prior compromise, therefore all Exchange servers should be inspected for signs of unauthorized access,” the CERT-LV explains in their project description.
This script will display files containing specific strings used by web shells, but not Microsoft Exchange, in ProxyLogon attacks. This script’s advantage is that it will not delete the file and allow incident responders to further analyze it.
Also Read: The DNC Registry: 5 Things You Must Know
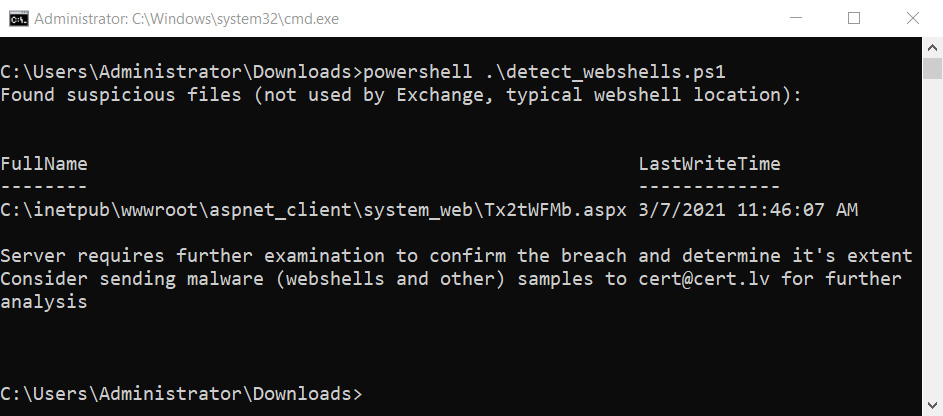
More information on how to use this script can be found in the CERT-LV project’s GitHub repository.
Microsoft also released a PowerShell script called Test-ProxyLogon.ps1 that can be used to search for indicators of compromise (IOC) related to these attacks in Exchange and OWA log files.