KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Vietnam-backed hacking group APT32 has coordinated several spyware attacks targeting Vietnamese human rights defenders (HRDs) between February 2018 and November 2020.
The state hackers also pointed their attacks at a nonprofit (NPO) human rights organization from Vietnam, as Amnesty International’s Security Lab revealed (full report here).
The spyware used by the APT32 hackers allowed them to read and write documents on compromised systems, launch malicious tools and programs, and monitor their victims’ activities.
“These latest attacks by Ocean Lotus highlight the repression Vietnamese activists at home and abroad face for standing up for human rights,” Amnesty Tech researcher Likhita Banerji said. “This unlawful surveillance violates the right to privacy and stifles freedom of expression.”
“The Vietnamese government must carry out an independent investigation. Any refusal to do so will only increase suspicions that the government is complicit in the Ocean Lotus attacks.”
Also Read: 10 Practical Benefits of Managed IT Services
As Amnesty International said, these attacks are part of an ongoing campaign focused on tracking and spying on Vietnamese HRDs, bloggers, and nonprofit organizations (from within and outside Vietnam’s borders) spanning over the last 15 years.
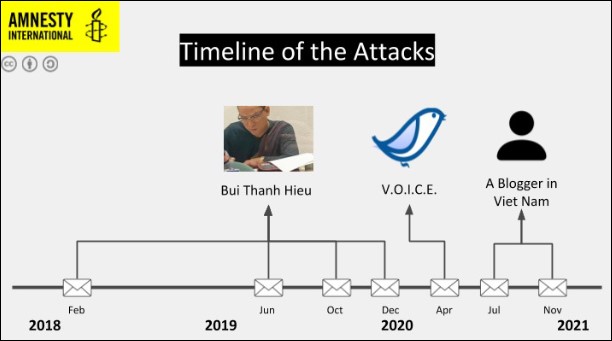
APT32’s “coordinated spyware campaign” targeted pro-democracy activist Bui Thanh Hieu, the Vietnamese Overseas Initiative for Conscience Empowerment (VOICE) NPO, and an undisclosed Vietnamese blogger.
“VOICE and the two bloggers all received emails containing spyware between February 2018 and November 2020,” Amnesty International added, with the final payload being installed on the victims’ Windows computers using APT32’s Kerrdown downloader.
The attackers downloaded and deployed Cobalt Strike beacons to gain persistent remote access to the compromised systems.
In the case of victims who used Macs, the APT32 operators used a macOS backdoor spotted by TrendMicro in previous attacks on Vietnamese targets, a malware strain designed to provide the attackers with the ability to download, upload, and execute arbitrary files and commands.
APT32 (aka OceanLotus, SeaLotus) is a Vietnamese-backed advanced persistent threat group known for targeting foreign companies investing in multiple Vietnam industry sectors, Vietnamese human rights organizations and activists, and worldwide research institutes and media organizations.
They also breached the networks of Toyota and Lexus sales subsidiaries, the networks of BMW and Hyundai, and they were linked by Crowdstrike to attacks against automotive targets.
More recently, APT32 attempted to harvest intelligence on the ongoing COVID-19 crisis through spear-phishing attacks targeting China’s Ministry of Emergency Management and the Wuhan province government.
FireEye also describes the group as “aligned with Vietnamese state interests,” with their targeted operations against journalists and Vietnam diaspora members threatening free speech and political activism.
The real identity of APT32 was exposed by the Facebook security team in December 2020 when they were publicly linked to the Vietnamese IT firm CyberOne Group.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
“Although Amnesty International was unable to independently verify any direct connection between Ocean Lotus and CyberOne or with the Vietnamese authorities, the attacks described in this investigation confirm a pattern of targeting Vietnamese individuals and organizations,” Amnesty International said.