KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The ScamClub malvertising group used a zero-day vulnerability in the WebKit web browser engine to push payloads that redirected to gift card scams.
During their campaigns over the past three months, the number of malicious ad impressions served in a day recorded spikes as high as 16 million.
ScamClub malvertisers are notorious for their noisy tactics that consist of flooding the ad ecosystem with malicious ads hoping that a smaller percentage goes through.
Even if most of the ads are blocked, the volume is so large that the ads that slip undetected amount to a significant number of malicious impressions during a single campaign.
Describing ScamClub’s “bombardment strategy,” ad security and quality controls company Confiant says that an improvement of just 1% in the redirect rate can translate into “tens of thousands of impacted impressions” during a single campaign.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
While observing ScamClub activity, in June 2020 Confiant noticed in the payload’s obfuscated code four lines with an event listener that piqued the researchers’ curiosity.
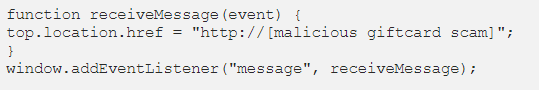
In a blog post today, Confiant security engineer and researcher Eliya Stein found that the malvertiser relied on a vulnerability in WebKit that bypassed the iframe sandboxing policy.
Investigating further, the researcher removed the unnecessary code and staged a simple HTML file with a cross-origin sandboxed frame and a button that dispatched the event, with the payload being the listener.
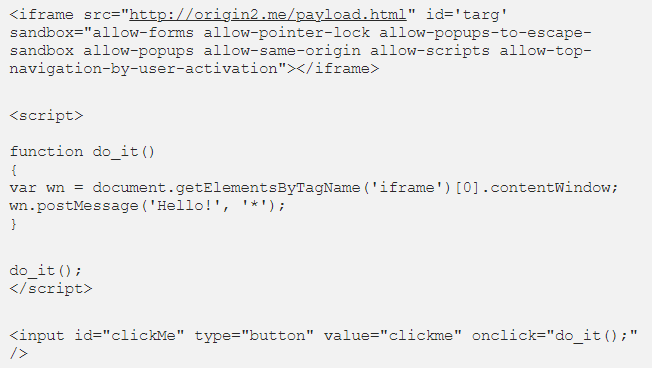
Stein notes that the ‘allow-top-navigation-by-user-activation’ sandbox attribute in the proof of concept code above should prevent any redirection. This is valid if no proper activation occurs, which, in this case, means clicking inside the frame.
“This means our proof of concept shouldn’t work under any circumstances. The clickMe button is outside of the sandboxed frame after all. However, if it does redirect, that means we have a browser security bug on our hands, which turned out to be the case when tested on WebKit based browsers, namely Safari on desktop and iOS” – Eliya Stein
While this should theoretically prevent malicious redirects, the researcher further explains that messages with wildcard destinations in modern web applications are common, and they often occur on user interaction.
Given SscamClub’s broad targeting and large volumes of malicious ads they push, some of them still slip through and have a significant impact. Below are domains used in ScamClub’s malvertising campaigns.
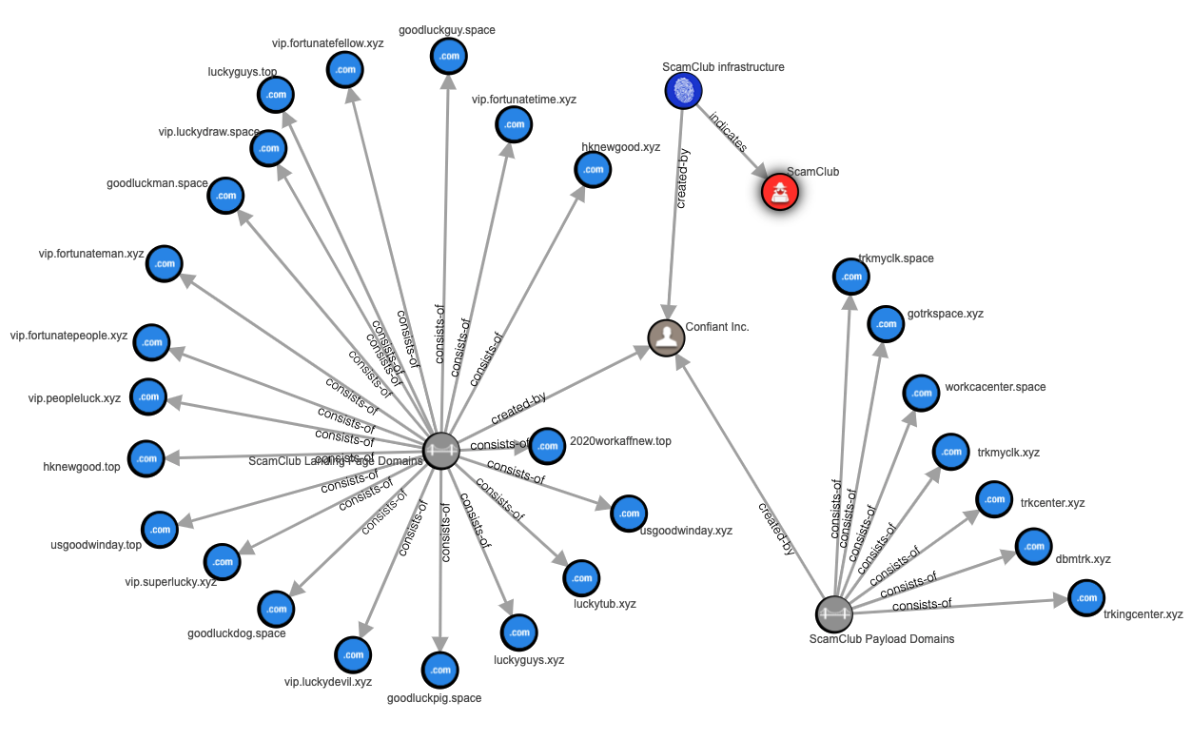
To put this into perspective, Confiant attributes to the ScamClub group more than 50 million malicious impressions over the past 90 days, with peaks in impacted ads that reached 16 million in a day.
Also Read: The 3 Main Benefits Of PDPA For Your Business
Since WebKit is used in Chrome on iOS and Safari, Stein submitted his findings to both Apple Security and the Google Chrome team. WebKit received a patch on December 2, 2020, and the identifier CVE-2021-1801 has been assigned to the vulnerability.
Confiant released indicators of compromise (IoCs) in their GitHub repository, which include hosting of the payloads in Amazon cloud and the domains used in the recent ScamClub campaigns.