KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





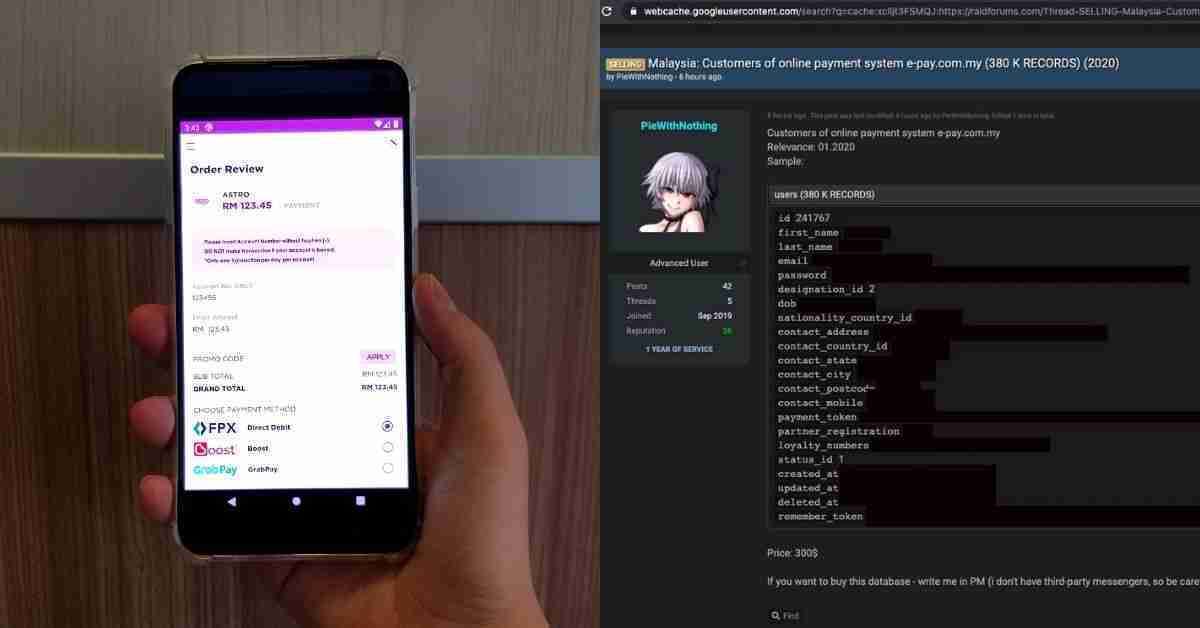
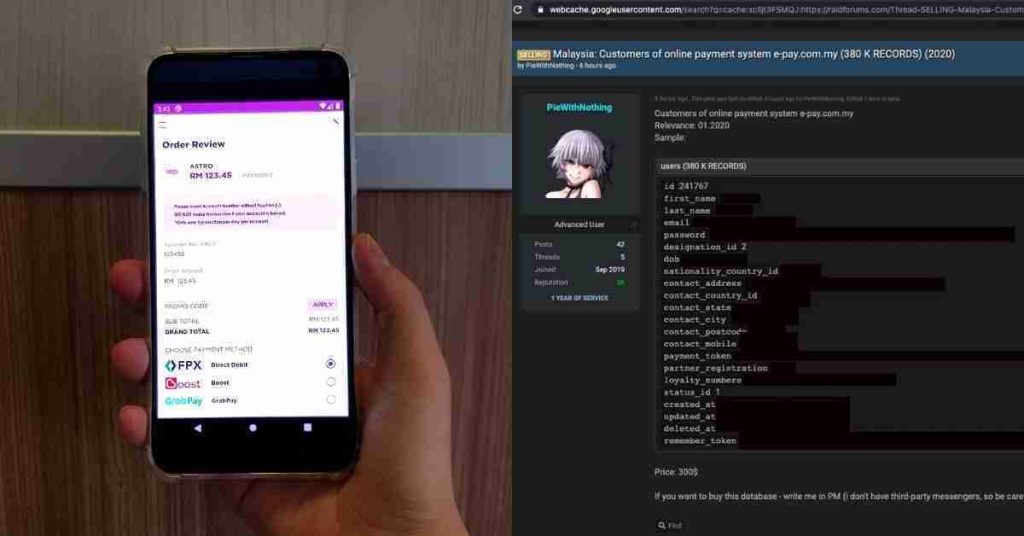
Reports have surfaced that personal details of at least 380,000 e-pay Malaysia customers are being allegedly sold on an online data-sharing forum for US$300 (roughly RM1,215).
This transaction was highlighted on Twitter and shared on Facebook at 3AM on February 4.
From what we can see of a sample record that has since been deleted on the forum, data being leaked consists of names, full addresses, passwords, mobile phone numbers, and more.
Also Read: How To Check Data Breach And How Can We Prevent It
Now, it’s unclear whether or not the payment gateway itself has been hacked. This might just be a website hack through e-pay.com.my, as the details shared in the leak line up with the website’s user info field.
Their other products like the online payment gateway and terminal might not be affected, as we haven’t seen any victims sharing on social media that their financial accounts have been affected yet.
On the Facebook post, most commenters who are also users merely voiced out their worries.
To be on the safe side though, e-pay Malaysia users should change their username and passwords immediately, even if they may not be one of the 380,000 users affected.
Additionally, users can consider deactivating or deleting their accounts until e-pay Malaysia makes an official statement on this, or at least avoid making any transactions through the site for the meantime.
Because e-pay is Malaysia’s largest prepaid top-up and bill collection network, some of its merchants include:
They also service most card and e-wallet payments such as Visa, MasterCard, GrabPay, Touch ‘n Go eWallet, etc.
Though there’s likely nothing you can do if your info has already been leaked, commentators are disappointed that it allegedly happened in the first place.
As we wait for an official report, we noticed some suggestions on Facebook from concerned users on what others could do in the meantime on top of the aforementioned immediate actions.
One option, on top of changing your online banking passwords, is to change the payment account that’s using the debit option.
If possible, concerned users could request making a new debit card with a new number from your bank (it’s still the same account, under a different number).
On e-pay Malaysia’s end, it is extremely important that they be transparent about providing the exact details of:
Also Read: Intrusion Into Privacy All About Law And Legal Definition
As of now, e-pay Malaysia has yet to address user concerns or clarify anything and we have no further way to verify this information, but we hope investigation and a report is underway nonetheless.
Even if this turns out to be untrue, the lack of clarification from e-pay Malaysia could still end up hurting their brand reputation and cause customers to lose confidence in them.
So, we’ve reached out to e-pay Malaysia to get their side of the story and more facts, and will be updating the piece with their responses.
Editor’s Update (February 4, 6:17PM): The e-pay Malaysia team has gotten back to us with a media statement to acknowledge the issue. We’ve summarised their statement below.
The GHL Group on behalf of e-pay Malaysia stated that the above allegations are isolated only to the e-pay online reload and bill payment collection system (EVE).
The EVE system operates on an independent standalone system which does not interfere with the technical operations of other e-pay and GHL merchant acquiring systems and servers, so their other businesses and operations will not be impacted.
Investigations are still being conducted, and the team shared that they’ll continue to update users on the progress and any new findings.
In the meantime, they advised EVE users to go to the official website and change their passwords as precautionary measures, and avoid clicking on unverified email links urging them to update their credentials.