KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







More and more ransomware victims are resisting the extortionists and refuse to pay when they can recover from backups, despite hackers’ threats to leak the data stolen before encryption.
This stance resulted in Q4 of 2020 seeing a significant decline in the average ransom payments compared to the previous quarter, says ransomware remediation firm Coveware.
But a more insidious phenomenon is prefiguring, where data is destroyed in the attack leaving companies no option to recover it, even if they pay the ransom.
In the last quarter of 2020, Coveware received an increasing number of reports about entire clusters of servers and data shares being wiped out in ransomware attacks.
Typically, ransomware attacks target backup systems and encrypt high-value machines. In these cases, though, there was nothing to recover and victims had to rebuild the systems.
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
Attackers doing this on purpose makes little sense since they rely on the files being available in an encrypted state; otherwise, victims would have no reason to pay for the decryption tool.
“The uptick in haphazard data destruction has led some victims to suffer significant data loss and extended business interruption as they struggle to rebuild systems from scratch” – Coveware
These incidents could be a consequence of less-skilled attackers flooding the ransomware business scene and botching things up. Coveware does not exclude the possibility of this being a trend that could continue this year.
If the former of the theories above is true, the mishandled attacks could be the work of affiliates of open ransomware-as-a-service (RaaS) operations that do not set an acceptance standard; or of non-affiliated hackers that run campaigns with no help outside their small group.
Threatening victims with leaking stolen data to pressure them into paying is a twist that the now shut down Maze ransomware operation introduced in late 2019.
Other gangs in the ransomware business, seeing the potential for higher profits from this double-extortion tactic, followed suit and set up so-called “leak sites“ where they publish data stolen from victims that did not pay the ransom.
With no other guarantee than the attackers’ word that the stolen data would not be published, victim companies caved in and acted on paying the ransom.
Statistics from Coveware seem to indicate that this method has lost some of its power as the average ransom demand dropped by 34% in Q4 2020. Translated into cash, it’s a plop from $233,817 to $154,108.
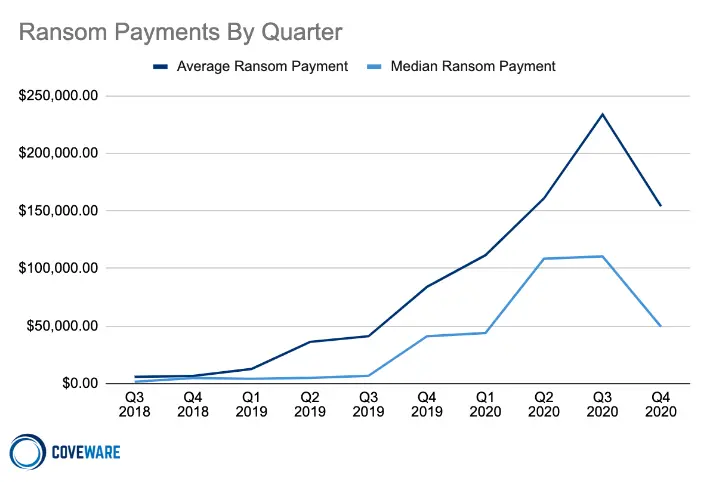
Looking at the median value, the drop is deeper, 55% from $110,532 to $49,450. Coveware says that this “dramatic reduction was attributed to more victims of data exfiltration attacks saying “ENOUGH” and choosing not to pay.”
This comes on the backdrop of more ransomware attacks in Q4 being accompanied by the threat of leaking stolen data, from 50% to 70%.
Companies are right not to trust hackers about deleting the stolen data if they got paid as Coveware continues to see signs that this is not happening in all cases.
Even more, some gangs lie about exfiltrating data and fabricate “evidence“ just to add the pressure of a data breach on the victim and force a payment.
Coveware advises ransomware victims not to pay the hackers. If they do, there is no guarantee that their data is safe, and here is what they should expect:
Although the average and median ransom sizes took a nosedive over the past four months, high-profile ransomware operators continue to collect big money from carefully selected victims.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
According to Coveware statistics, closed RaaS operations like Sodinokibi, Egregor, and Ryuk dominate the market share, breaching companies mostly via phishing and compromised RDP connections.
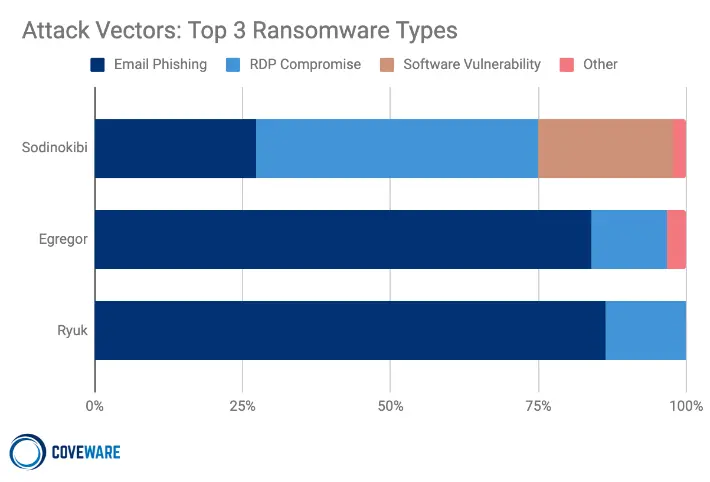
Netwalker, with one affiliate indicted in the U.S. and its dark web sites seized by law enforcement, is next on the list, followed by Maze, which is losing its spot because it shut down recently.
New ransomware strains have made it to Coveware’s top ten list at the end of last year, such as Conti, Suncrypt, Zeppelin, MedusaLocker. Some of them are very likely to increase activity soon.