KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Even with the security updates prompted by the recent SolarWinds Orion supply-chain attack, researchers still found some glaring vulnerabilities affecting the platform, one of them allowing code execution with top privileges.
Three issues have been found, two of them exploitable by a local attacker. A third one, the most severe of all, allows a remote, unprivileged actor to take control of the Orion platform.
The vulnerabilities have been discovered and reported to SolarWinds by Martin Rakhmanov, Security Research Manager, SpiderLabs at Trustwave, and have proof-of-concept (PoC) exploit code available.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
The researcher did not publish the demo code with the report today to give users longer time to install the official patches from SolarWinds. However, the grace period expires on February 9, when the PoCs for all three vulnerabilities will be publicly available.
Analyzing a demo copy of the SolarWinds Orion software, Rakhmanov noticed that it uses the Microsoft Message Queue (MSMQ) technology and started to poke around.
He noticed that the SolarWinds Orion Collector service relies heavily on MSMQ, with a large list of private queues available, all of them unauthenticated.
This means that unauthenticated users can send messages to the queues over TCP port 1801, the researcher explains. Due to an insecure deserialization, an unprivileged user can execute arbitrary code remotely.
“Given that the message processing code runs as a Windows service configured to use LocalSystem account, we have complete control of the underlying operating system” – Martin Rakhmanov
SolarWinds addressed this issue (CVE-2021-25274) by adding a digital signature validation step when new messages arrive. Without a valid signature, messages are no longer processed. MSMQ, though, remains unauthenticated and can receive messages from anyone.
A second vulnerability (CVE-2021-25275) that Rakhmanov discovered was that the credentials for the Orion backend database were insufficiently protected and local users had unrestricted access to them.
The researcher found the sensitive data in the SOLARWINDS_ORION configuration file that could be read by locally authenticated users.
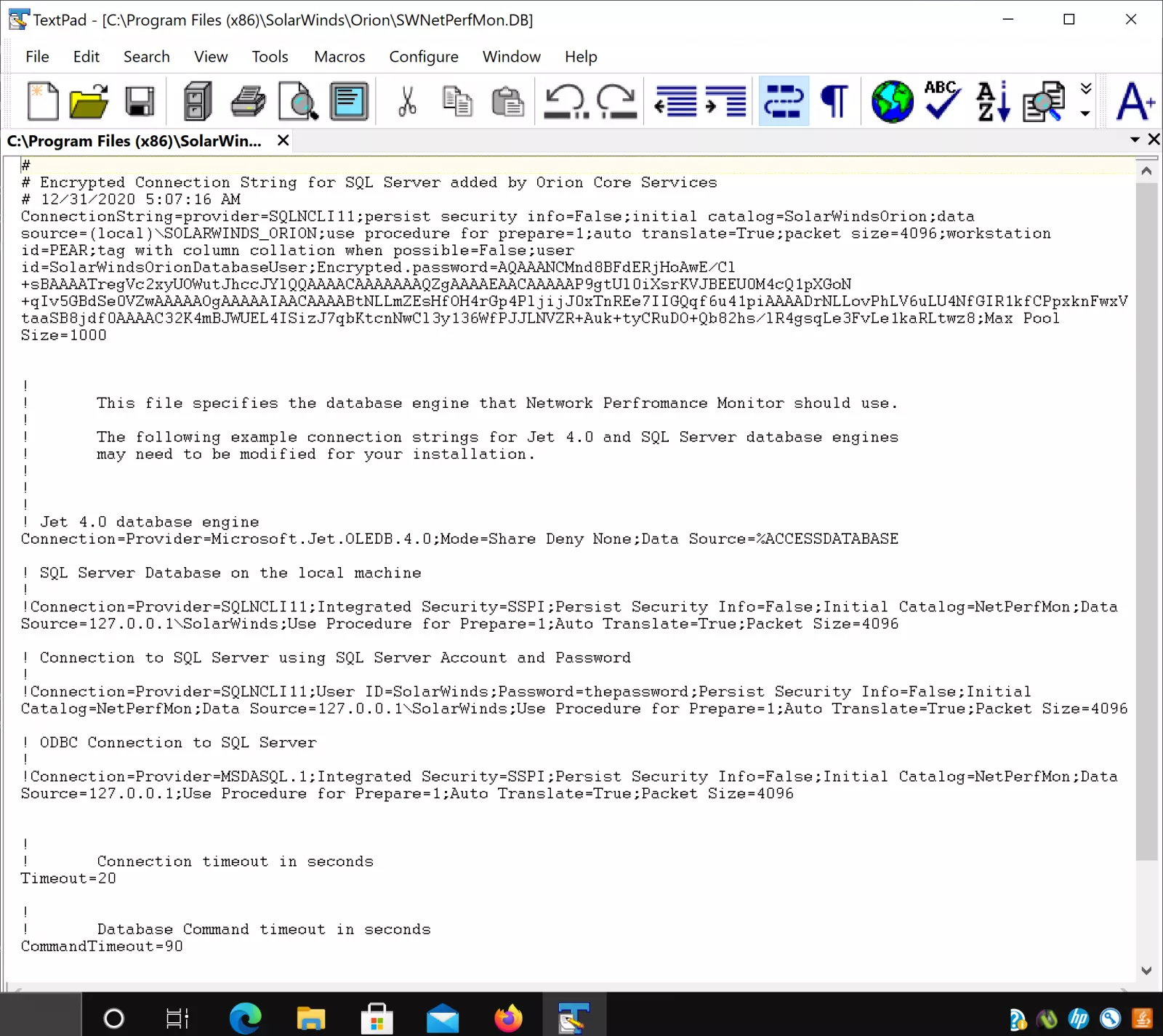
The credentials are not in plain text and the researcher had to find the code that decrypted them. According to Rakhmanov, this was not a difficult task and could be achieved with only one line of code.
“In the end, unprivileged users who can log in to the box locally or via RDP will be able to run decrypting code and get a cleartext password for the SolarWindsOrionDatabaseUser” – Martin Rakhmanov
After authenticating to the Microsoft SQL Server with the recovered credentials, a threat actor would have complete control over the SolarWinds Orion database and could steal information or add admin-level users.
The third vulnerability (CVE-2021-25276) is in the SolarWinds Serv-U FTP Server. The researcher discovered that the accounts are stored in separate files on the disk and that an authenticated user has access to them.
“Directory access control lists allow complete compromise by any authenticated Windows user. Specifically, anyone who can log in locally or via Remote Desktop can just drop a file that defines a new user, and the Serv-U FTP will automatically pick it up” – Martin Rakhmanov
The FTP server runs with LocalSystem permissions, so by creating an admin account, an attacker could set the home directory to the root of the system drive and thus open the door to read or replace any file there.
Also Read: Letter of Consent MOM: Getting the Details Right
Trustwave’s SpiderLabs started to disclose the vulnerabilities to SolarWinds on December 30, 2020, and by January 25, 2021, the software maker had rolled out patches for all of them.
Administrators can get the fixes by installing Orion Platform 2020.2.4 and by applying Hotfix 1 for ServU-FTP 15.2.2.