KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Today, Microsoft disclosed that they have also been monitoring the targeted attacks against vulnerability researchers for months and have attributed the attacks to a DPRK group named ‘Zinc.’
Earlier this week, Google disclosed that a North Korean government-backed hacking group has been using social networks to target security researchers.
As part of the attacks, the threat actors would ask researchers to collaborate on vulnerability research and then attempt to infect their computers with a custom backdoor malware.
In a new report, Microsoft states that they too have been tracking this threat actor, who they track as ‘ZINC,’ for the past couple of months as the hackers target pen testers, security researchers, and employees at tech and security companies. Other researchers track this hacking group under the well-known name ‘Lazarus.’
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
“In recent months, Microsoft has detected cyberattacks targeting security researchers by an actor we track as ZINC. The campaign originally came to our attention after Microsoft Defender for Endpoint detected an attack in progress. Observed targeting includes pen testers, private offensive security researchers, and employees at security and tech companies.”
“Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to ZINC, a DPRK-affiliated and state-sponsored group, based on observed tradecraft, infrastructure, malware patterns, and account affiliations,” the Microsoft Threat Intelligence Center team disclosed in a new report.
Based on Microsoft’s research, the ZINC actors began operating in mid-2020 by building online Twitter security researcher personas by retweeting security content and posting about vulnerability research.
The threat actors’ would then amplify these tweets using other sock-puppet Twitter accounts under their control. This tactic allowed the group to build a reputation in the security vulnerability research space and build a following that included “prominent security researchers.”
As part of their attack, the ZINC actors would contact researchers to collaborate on vulnerability and exploit research. As previously reported by Google, for those researchers who agreed, ZINC would send a Visual Studio project containing a malicious DLL that would be executed when researchers compiled the project.
This DLL would lead to installing a backdoor malware that would allow the attackers to retrieve information and execute commands on the computer.
“Over this C2 channel, the threat actors can execute remote commands to enumerate files/directories and running processes, and to collect/upload information about the target device, including IP address, Computer Name, and NetBIOS. Furthermore, we observed some hands-on-keyboard action to enumerate all files/directories on the target disk, create screenshots, and deploy additional modules,” explains Microsoft’s report.
In addition to the malicious Visual Studio project, Microsoft saw ZINC attacking security professionals using other methods.
Also Read: How a Smart Contract Audit Works and Why it is Important
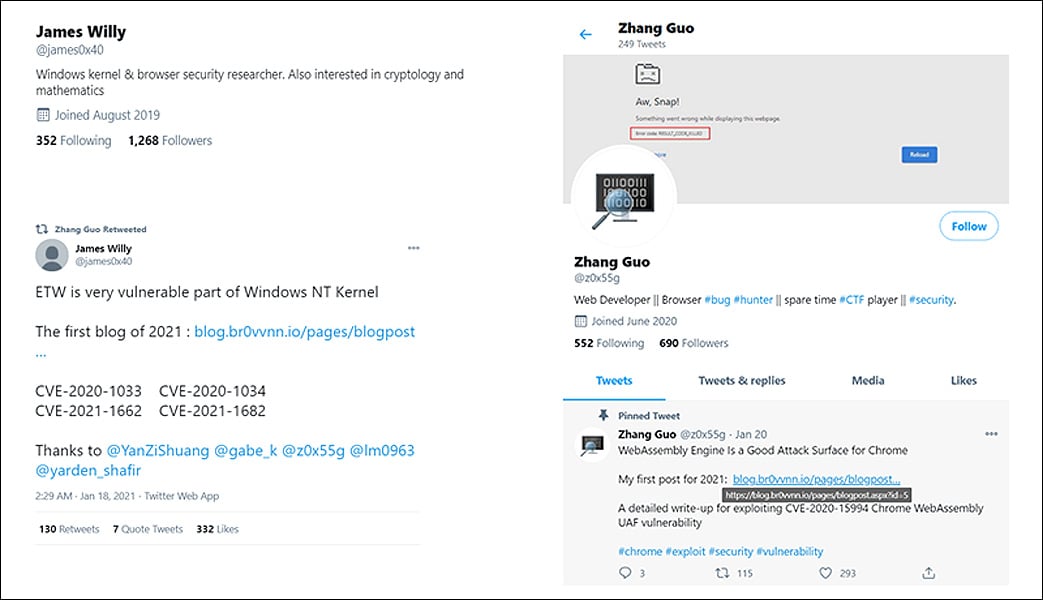
As already explained in Google’s reports, some people were infected simply by visiting the threat actors’ web site on fully patched systems and the latest Google Chrome. Google was unsure how the visitors were compromised but suspected the use of zero-day vulnerabilities.
Microsoft states that the threat actors shared a link to a blog post on their web site that contained an exploit kit using “0-day or patch gap exploits.”
“A blog post titled DOS2RCE: A New Technique To Exploit V8 NULL Pointer Dereference Bug, was shared by the actor on October 14, 2020 from Twitter. From October 19-21, 2020, some researchers, who hadn’t been contacted or sent any files by ZINC profiles, clicked the links while using the Chrome browser, resulting in known ZINC malware on their machines soon after.
“This suggests that a Chrome browser exploit chain was likely hosted on the blog, although we haven’t been able to prove this. Since some of the victim’s browsers were fully patched, it’s also suspected, but unproven, that the exploit chain used 0-day or patch gap exploits”, Microsoft explained.
Other attacks methods used by ZINC included:
Microsoft warns that you had visited the ZINC-owned blog (br0vvnn[.]io), you should immediately run a full antivirus scan or use the IOCs in their report to check for infections.
If these IOCs are found on your machine, you should assume that the device has been fully compromised.