KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A hacker has leaked 1.9 million Pixlr user records containing information that could be used to perform targeted phishing and credential stuffing attacks.
Pixlr is a very popular and free online photo editing application with many of the same features found in a professional desktop photo editor like Photoshop. While Pixlr offers basic editing tools for free, the site also provides premium memberships that include more advanced tools, stock photos, and other features.
Over the weekend, a threat actor known as ShinyHunters shared a database for free on a hacker forum that he claims was stolen from Pixlr while he breached the 123rf stock photo site. Pixlr and 123rf are both owned by the same company, Inmagine.
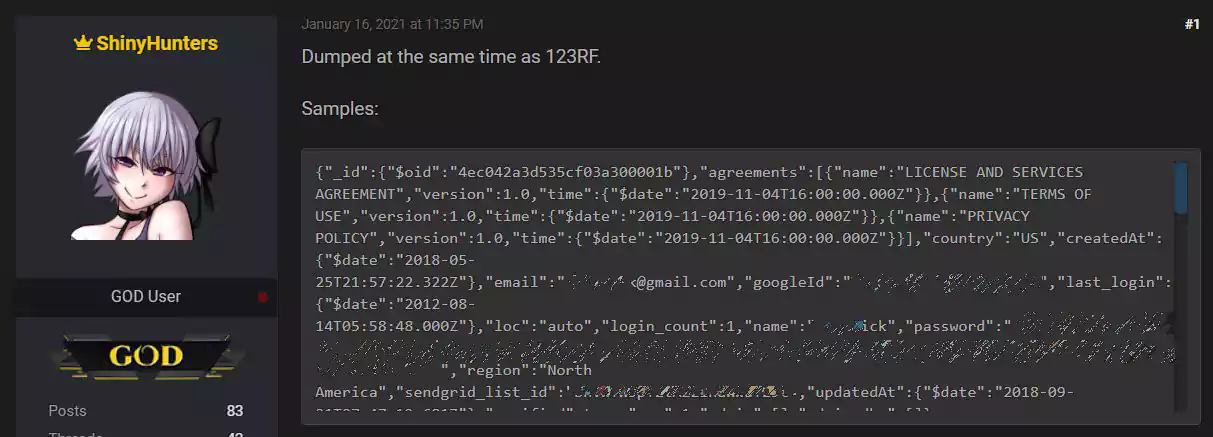
ShinyHunters is a threat actor well-known for hacking into websites and selling stolen user databases in private sales or via data breach brokers. In the past, ShinyHunters has been responsible for data breaches at Tokopedia, Homechef, Minted, Chatbooks, Dave, Promo, Mathway, Wattpad, and many more.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
The alleged Pixlr database posted by ShinyHunters contains 1,921,141 user records consisting of email addresses, login names, SHA-512 hashed passwords, a user’s country, whether they signed up for the newsletter, and other internal information.
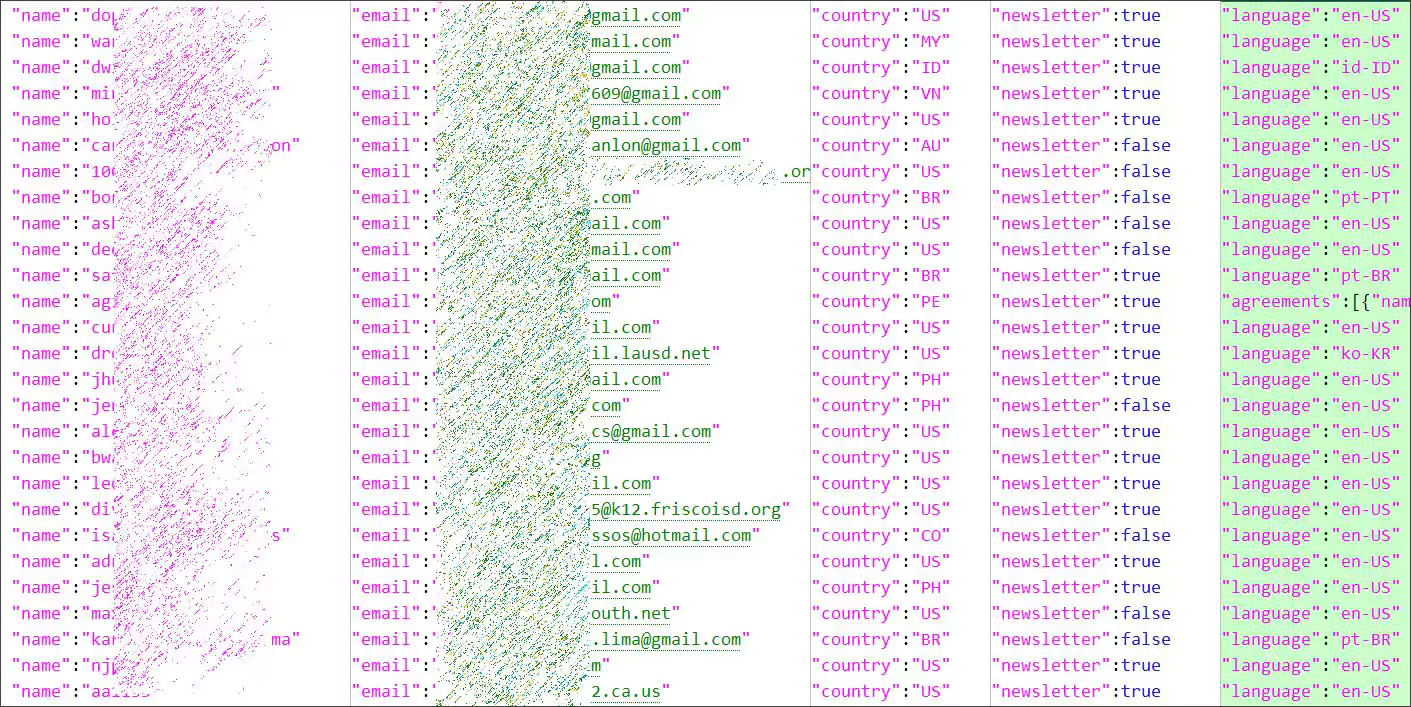
ShinyHunters stated he downloaded the database from the company’s AWS bucket at the end of 2020.
After sharing the database, many other threat actors who frequent the hacker forum shared their appreciation as attackers could use the data for their malicious activities.
While Pixlr has not responded to our email about the leaked database, BleepingComputer has confirmed that many of the email addresses in the database are registered Pixlr members.
As some of the exposed data is confirmed as accurate, it does appear to be a legitimate breach.
It is strongly suggested that all Pixlr users immediately change their passwords on the site out of an abundance of caution. Users should use a unique and strong password that is not used at any other site.
If the same password at Pixlr is used at other sites, you should change your password at these sites and one unique for the site.
A password manager is recommended to help you manage the unique passwords you use at different sites.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
Update 1/20/2021: Article was updated to include the correct number of user records. Originally, we stated 1.4 million user records, but the actual number is 1.9 million.