KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An unpatched zero-day in Microsoft Windows 10 allows attackers to corrupt an NTFS-formatted hard drive with a one-line command.
In multiple tests by BleepingComputer, this one-liner can be delivered hidden inside a Windows shortcut file, a ZIP archive, batch files, or various other vectors to trigger hard drive errors that corrupt the filesystem index instantly.
In August 2020, October 2020, and finally this week, infosec researcher Jonas L drew attention to an NTFS vulnerability impacting Windows 10 that has not been fixed.
When exploited, this vulnerability can be triggered by a single-line command to instantly corrupt an NTFS-formatted hard drive, with Windows prompting the user to restart their computer to repair the corrupted disk records.
The researcher told BleepingComputer that the flaw became exploitable starting around Windows 10 build 1803, the Windows 10 April 2018 Update, and continues to work in the latest version.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
What’s worse is, the vulnerability can be triggered by standard and low privileged user accounts on Windows 10 systems.
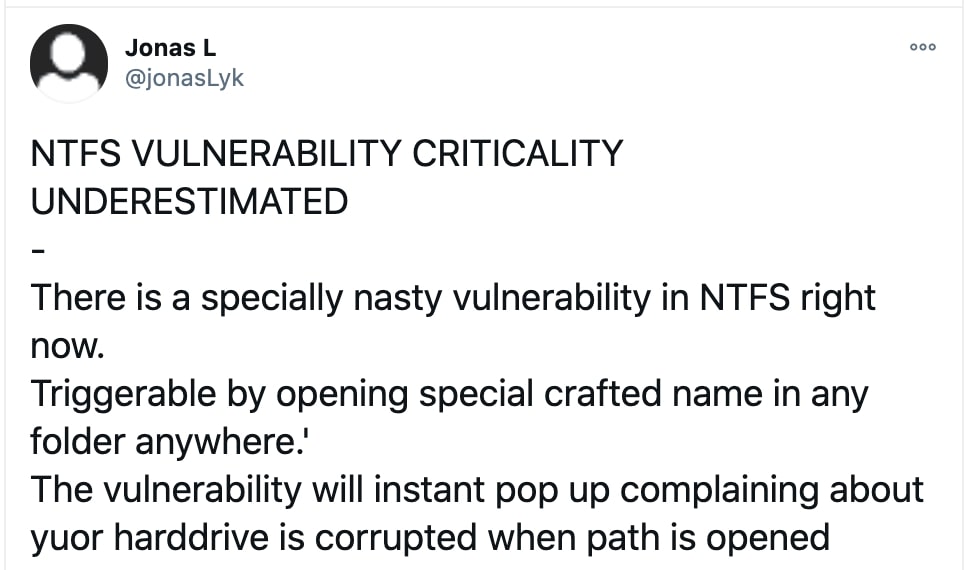
A drive can become corrupted by merely trying to access the $i30 NTFS attribute on a folder in a certain way.
*WARNING* Executing the below command on a live system will corrupt the drive and possibly make it inaccessible. ONLY test this command in a virtual machine that you can restore to an earlier snapshot if the drive becomes corrupted.*WARNING*
An example command that corrupts a drive is shown below.
The Windows NTFS Index Attribute, or ‘$i30‘ string, is an NTFS attribute associated with directories that contains a list of a directory’s files and subfolders. In some cases, the NTFS Index can also include deleted files and folders, which comes in handy when conducting an incident response or forensics.
It is unclear why accessing this attribute corrupts the drive, and Jonas told BleepingComputer that a Registry key that would help diagnose the issue doesn’t work.
‘I have no idea why it corrupts stuff and it would be a lot of work to find out because the reg key that should BSOD on corruption does not work. So, I’ll leave it to the people with the source code,’ Jonas told BleepingComputer.
After running the command in the Windows 10 command prompt and hitting Enter, the user will see an error message stating, “The file or directory is corrupted and unreadable.”
Windows 10 will immediately begin displaying notifications prompting the user to restart their PC and repair the corrupted disk volume. On reboot,the Windows check disk utility runs and starts repairing the hard drive, as demonstrated in the video below.
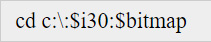
After the drives become corrupted, Windows 10 will generate errors in the Event Log stating that the Master File Table (MFT) for the particular drive contains a corrupted record.
BleepingComputer’s tests also show that you can use this command on any drive, not only the C: drive and that drive will subsequently become corrupted.
In tests conducted by BleepingComputer, threat actors can use the command maliciously in various PoC exploits.
One striking finding shared by Jonas with us was that a crafted Windows shortcut file (.url) that had its icon location set to C:\:$i30:$bitmap would trigger the vulnerability even if the user never opened the file!
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
As observed by BleepingComputer, as soon as this shortcut file is downloaded on a Windows 10 PC, and the user views the folder it is present in, Windows Explorer will attempt to display the file’s icon.
To do this, Windows Explorer would attempt to access the crafted icon path inside the file in the background, thereby corrupting the NTFS hard drive in the process.
Next, “restart to repair hard drive” notifications start popping up on the Windows PC—all this without the user even having opened or double-clicked on the shortcut file.
Creative attackers can also deliver this payload in a variety of ways to the victim.
While the same-origin policy on most browsers would limit such attacks being served from a remote server (e.g., a remote HTML document referencing file:///C:/:$i30:$bitmap), creative means exist to work around such restrictions.
The researcher briefly stated that other vectors could be used to trigger this exploit remotely, such as via crafted HTML pages that embed resources from network shares or shared drives that have references to the offending $i30 path.
In some cases, according to the researcher, it is possible to corrupt the NTFS Master File Table (MFT).
During our research, BleepingComputer came across a caveat.
In some tests, after the Windows 10 chkdsk utility had “repaired” the hard drive errors on reboot, the contents of the exploit file, in this case, the crafted Windows shortcut with its icon set to C:\:$i30:$bitmap would be cleared and replaced with empty bytes.
This means the crafted Windows shortcut file was enough to pull a one-off attack if this happens.
Besides, a victim is not likely to download a Windows shortcut (.url) file from the internet.
To make the attack more realistic and persistent, attackers could trick users into downloading a ZIP archive to deliver the crafted file.
An attacker can, for example, sneak in their malicious Windows shortcut file with a large number of legitimate files inside a ZIP archive.
Not only is a user more likely to download a ZIP file, but the ZIP file is likely to trigger the exploit every single time it is extracted.
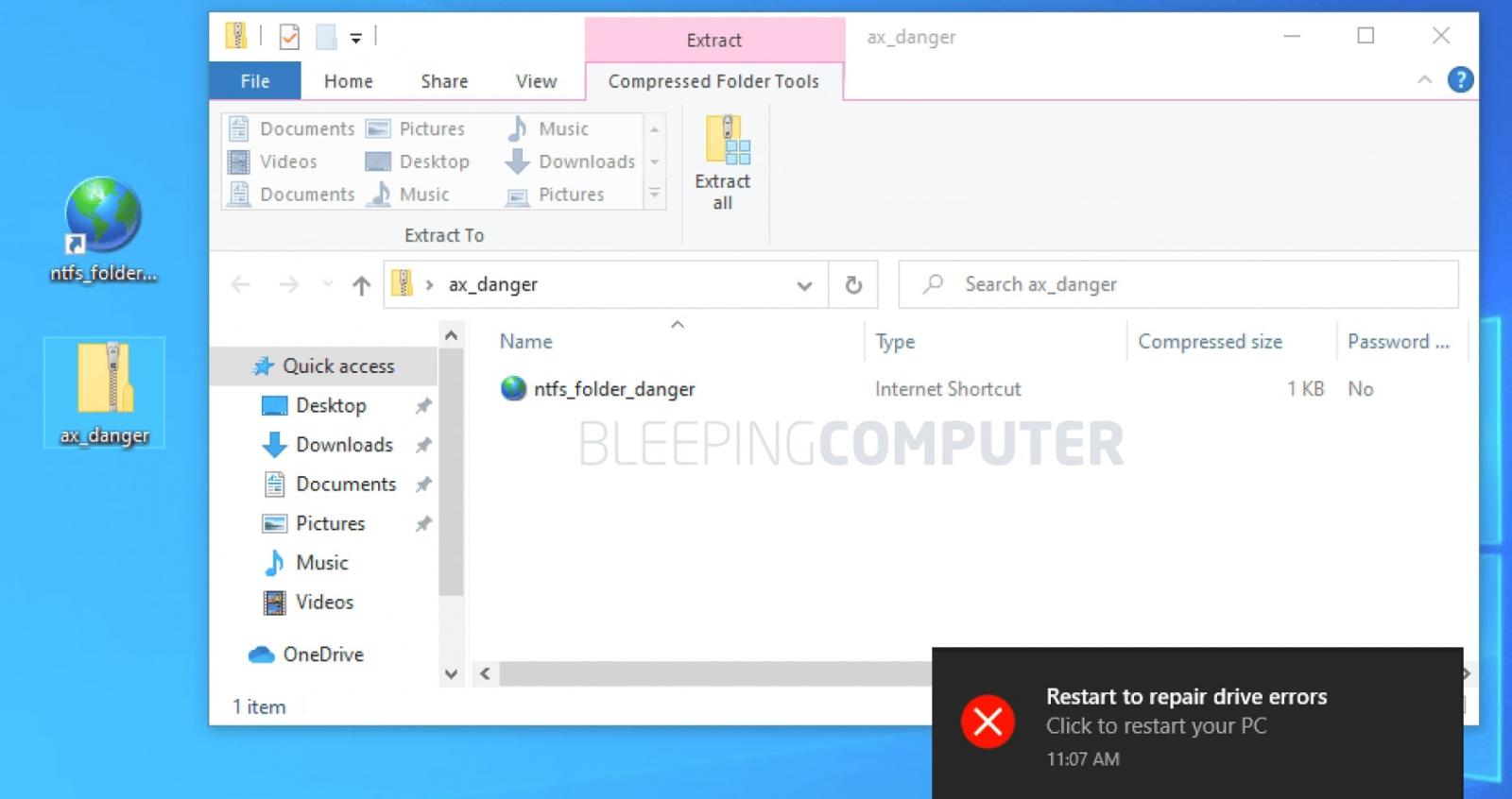
This is because the compressed (and possibly encrypted) contents of the ZIP file, including the Windows shortcut, would not trigger the exploit unless extracted.
And even when extracted, the hard drive repairing process would empty the extracted Windows shortcut file without touching the compressed copy present inside the ZIP archive until the user attempts to re-extract the ZIP.
According to sources in the infosec community, serious vulnerabilities like these have been known for years and reported to Microsoft earlier but remain unpatched.
BleepingComputer reached out to Microsoft to learn if they knew of the bug already and if they would fix the bug.
“Microsoft has a customer commitment to investigate reported security issues and we will provide updates for impacted devices as soon as possible,” a Microsoft spokesperson told BleepingComputer.