KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Project Zero, Google’s 0day bug-hunting team, revealed a hacking campaign coordinated by “a highly sophisticated actor” and targeting Windows and Android users with zero-day and n-day exploits.
The Project Zero team, in collaboration with the Google Threat Analysis Group (TAG), discovered a watering hole attack using two exploit servers in early 2020, each of them using separate exploit chains to compromise potential targets.
“These exploit chains are designed for efficiency & flexibility through their modularity,” Project Zero said after analyzing them for several months.
“They are well-engineered, complex code with a variety of novel exploitation methods, mature logging, sophisticated and calculated post-exploitation techniques, and high volumes of anti-analysis and targeting checks. We believe that teams of experts have designed and developed these exploit chains.”
Project Zero researchers were able to collect a trove of information from the two exploit servers including:
One of the exploit server used in those hacking operation was used to target Windows users, while the other specifically attempt to compromise Android devices.
In both cases, the attackers made use of Chrome exploits to remotely execute malicious code on the targets’ devices remote code execution, zero-days for Windows devices, and n-day ones for Android.
While no Android zero-days were used in the Android exploit chain, “[b]ased on the actor’s sophistication, we think it’s likely that they had access to Android 0-days, but we didn’t discover any in our analysis,” Project Zero said.
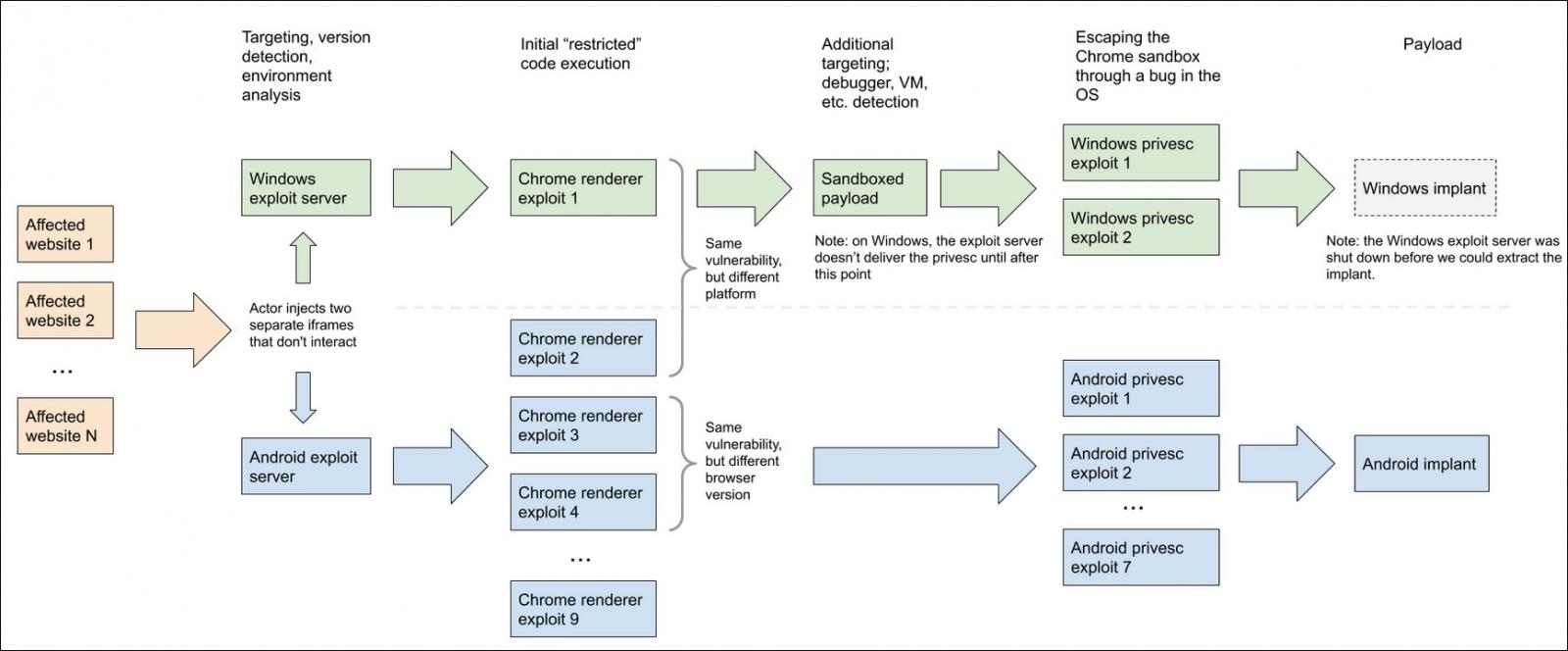
“Exploitation aside, the modularity of payloads, interchangeable exploitation chains, logging, targeting and maturity of this actor’s operation set these apart,” Project Zero added.
“We hope that by sharing this information publicly, we are continuing to close the knowledge gap between private exploitation (what well resourced exploitation teams are doing in the real world) and what is publicly known.”
The four zero-days exploited in these attacks and patched last year are:
All three Windows zero-days were addressed by Microsoft in the April 2020 Patch Tuesday, while the Chrome zero-day was patched by Google in February 2020 with the release of Chrome 80.0.3987.122 after discovering an exploit in the wild.
The Project Zero team also published separate reports about the Chrome “Infinity Bug” used to target Android users, the Chrome, Android, and Windows exploit chains, as well as the post-exploitation procedure used on rooted and compromised Android devices, as observed in the attacks.