KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Capcom has released a new update for their data breach investigation and state that up to 390,000 people may now be affected by their November ransomware attack.
On November 2nd, Capcom suffered a cyberattack by the Ragnar Locker ransomware operation who stated they stole 1TB of data from the company. The ransomware operation demanded an $11 million ransom in bitcoins to not release the stolen files and provide a decrypter.
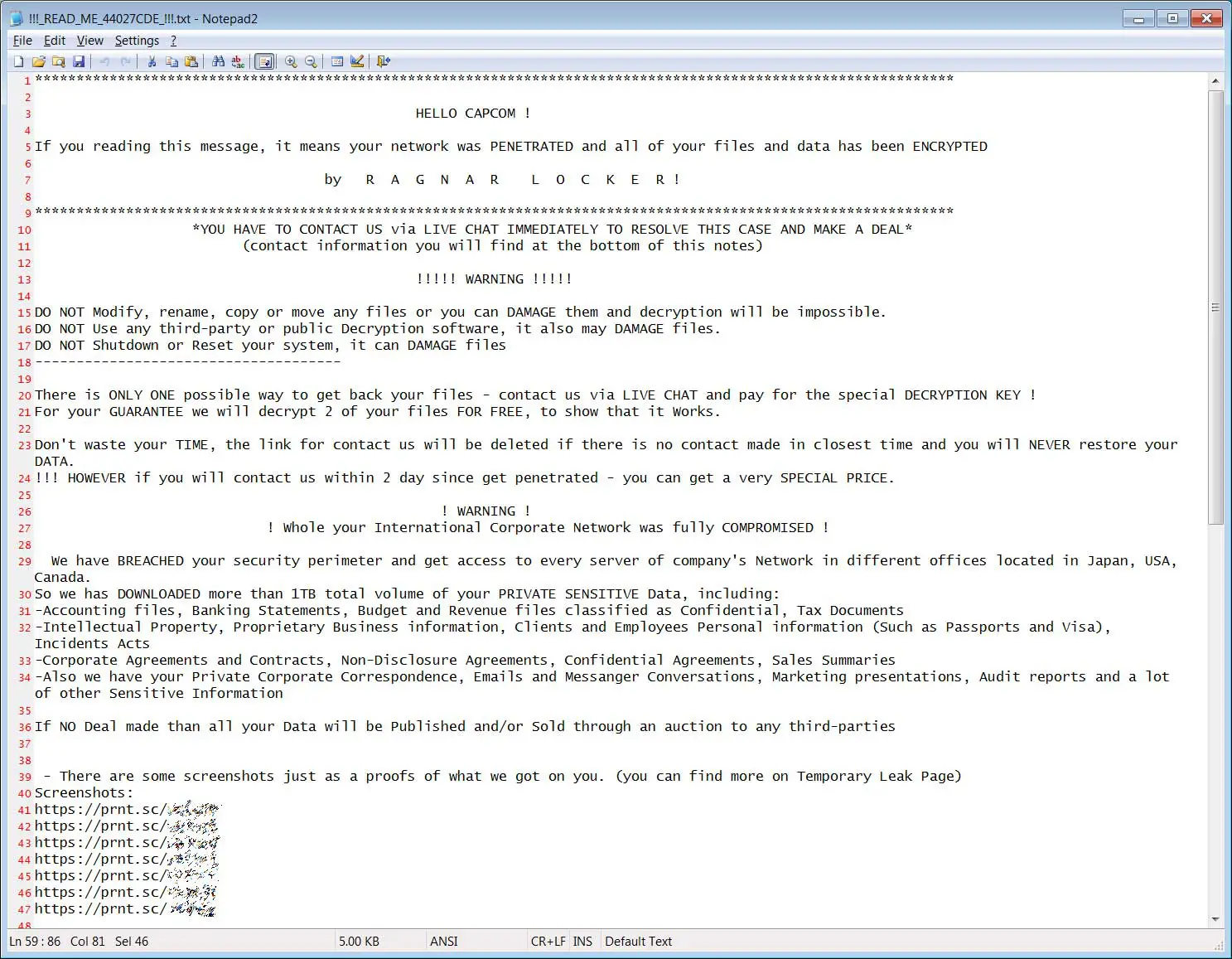
Soon after Ragnar Locker leaked Capcom’s stolen data, the company disclosed that they suffered a data breach where nine types personal information were exposed.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
In an update to the investigation released today, Capcom states that they have confirmed 16,415 people whose personal information was exposed, with a possible total number of affected people to be 390,000.
“As an update to its ongoing investigation, the company has verified that the personal information of an additional 16,406 people has been compromised, making the cumulative number since this investigation began 16,415 people.”
“Further, the company has also ascertained that the potential maximum number of customers, business partners, and other external parties etc., whose personal information may have been compromised in the attack is approximately 390,000 people,” Capcom’s latest update reveals.
For the confirmed 16,406 people, Capcom states the exposed data could be a mix of names, addresses, phone numbers, HT information, and email addresses.
| i. Personal Information | 16,406 people *cumulative total since investigation began: 16,415 peopleBusiness partners, etc.: 3,248 people At least one of the following: name, address, phone number, email address, etc.Former employees and related parties: 9,164 people At least one of the following: name, email address, HR information, etc.Employees and related parties: 3,994 people At least one of the following: name, email address, HR information, etc. |
|---|---|
| ii. Other Information | Sales reports, financial information, game development documents, other information related to business partners |
Capcom has provided the following estimates of additional people that may have been breached.
| i. Personal Information | Applicants: approx. 58,000 people At least one of the following: name, address, phone number, email address, etc.*Cumulative maximum number of potentially compromised data for customers, business partners and other external parties: 390,000 people*Regarding the cumulative maximum number of potentially compromised data above: as part of its ongoing investigation, Capcom has determined that it currently does not see evidence for the possibility of data compromise for the approximate 18,000 items of personal information from North America (Capcom Store member information and esports operations website members) that the company included in its November 16, 2020 announcement. As such, these have been removed from this cumulative maximum number of potentially compromised data. |
|---|
When ransomware operations perform their attacks, they steal almost all of the files and databases that they can get their hands on.
BleepingComputer has been told by ransomware gangs that they save more valuable data for online auctions or to use in further attacks. This means that the data that was leaked may not be all of the data that they stole.
Also Read: How a Smart Contract Audit Works and Why it is Important
Therefore, it is safer to assume that your data was breached during the attack and be on the lookout for targeted phishing attacks. While there is no indication that passwords were exposed, it is also advised that you change your Capcom password, and if used at other sites, change them there as well.