KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Iranian-backed hacking group Fox Kitten has been linked to the Pay2Key ransomware operation that has recently started targeting organizations from Israel and Brazil.
“We estimate with medium to high confidence that Pay2Key is a new operation conducted by Fox Kitten, an Iranian APT group that began a new wave of attacks in November-December 2020 that entailed dozens of Israeli companies,” threat intelligence firm ClearSky says.
According to the report published today, “this campaign is part of the ongoing cyber confrontation between Israel and Iran, with the most recent wave of attacks causing significant damage to some of the affected companies.”
The Iranian-backed Fox Kitten hacking group (also tracked as Parisite by ICS cybersecurity company Dragos) has been active since at least 2017 and is known for orchestrating and being involved in cyber-espionage and data theft campaigns.
They’ve also sold access to compromised corporate networks to other threat actors on underground forums and were detected while using CVE-2020-5902 exploits in attacks targeting vulnerable F5 BIG-IP devices.
Fox Kitten also provides access to the networks of compromised entities to another Iranian hacking group tracked as APT33 (aka Elfin, Magnallium).
Pay2Key is a relatively new ransomware operation that has targeted Israeli and Brazilian organizations over the past month.
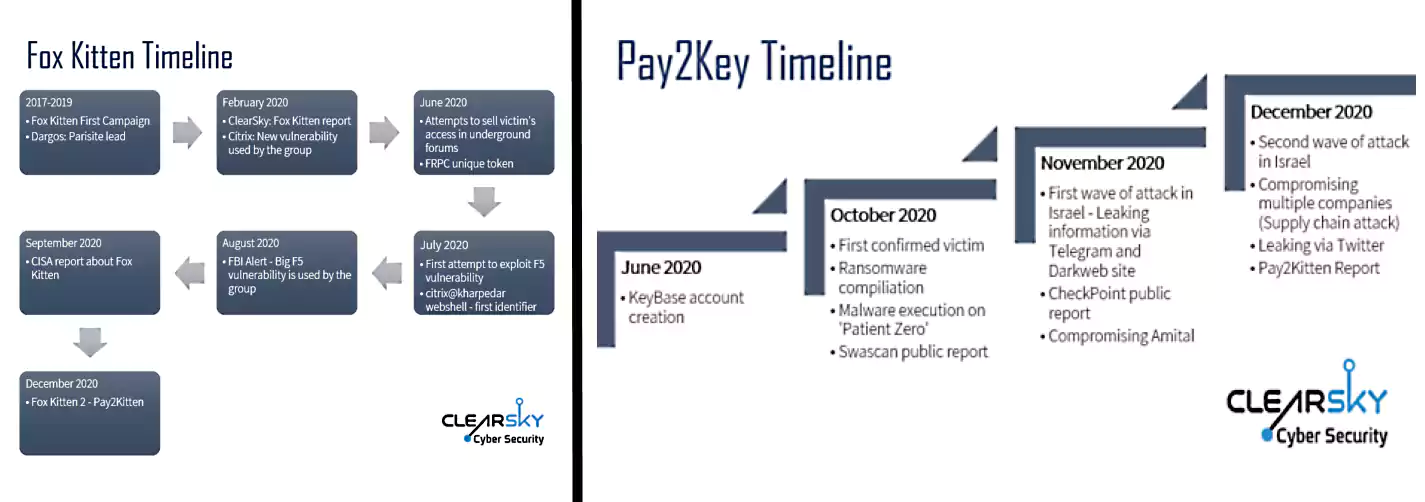
Starting with October 2020, Fox Kitten has been using Pay2Key ransomware attacks as cover for stealing sensitive information from industry, insurance, and logistics companies.
The group has exploited vulnerabilities in Pulse Secure, Fortinet, F5, and Global Protect VPN products or publicly exposed Remote Desktop Protocol (RDP) to gain access to the targets’ networks and deploy malware payloads.
The Pay2Key operators’ “ability to make a rapid move of spreading the ransomware within an hour to the entire network,” as discovered by Check Point, also provides hints at the group most likely being a state-sponsored operation with APT-grade skills and resources.
They also set up a pivot device to be used as an outgoing communication proxy between the infected devices and the C2 servers which helps them evade or reduce the risk of detection before encrypting all reachable network systems.
Indicators of compromise spotted during the Pay2Key ransomware attacks also link them to previous Iranian destructive attacks according to Israeli cybersecurity firms Profero and Security Joes.
Also Read: 10 Principles On How To Build A Good Governance Model
Another hint at the information theft focus of Pay2Key operations is that the group hasn’t even deployed ransomware payloads on the networks of recent victims but, instead, only used the stolen data for extortion purposes.
Israeli media has reported that threat actors (believed to be Pay2Key operators) breached Israeli shipping and cargo software company Amital earlier this month and used the gained access to compromise 40 Amital clients in a supply chain attack.
Another threat actor tracked as BlackShadow claimed a cyberattack against Israeli insurance company Shirbit and demanded $1 million to stop leaking stolen.
While the attack that compromised Shirbit’s systems is quite similar to Pay2Key’s attacks, it is not yet known if they are linked in any way.
“No, we didn’t find any link yet between Fox Kitten, Pay2Key, to BlackShadow,” ClearSky Lead Cyber Intelligence Researcher Ohad Zaidenberg told BleepingComputer.
“We assess that the course of action was to create panic, information warfare and not getting the ransom itself.”
Israeli cybersecurity researchers believe that these attacks have escalated due to the recent assassination of an Iranian nuclear scientist.
Profero also linked the Pay2Key attacks to Iranian threat actors in November after tracking the group’s ransom payment wallets to Iranian bitcoin exchanges.
“We estimate with a medium level of confidence that this campaign (Pay2Key) is part of Iran information warfare aimed to create panic to Israel and in other countries world-wide,” ClearSky added.
“The ransomware group pay2key publicly threatened Israel, this might indicate that this operation is only a propaganda campaign to cause fear with diversion from the real adversary.”
Also Read: The Importance of DPIA And Its 3 Types Of Processing
More information on the overlaps between the tools and techniques used by Fox Kitten and the Pay2Key group can be found in ClearSky’s Pay2Kitten report [PDF].