KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







SystemBC, a commodity malware sold on underground marketplaces, is being used by ransomware-as-a-service (RaaS) operations to hide malicious traffic and automate ransomware payload delivery on the networks of compromised victims.
The malware, first spotted in 2018 and used in several 2019 campaigns as a “virtual private network”, has allowed ransomware gangs and their affiliates to deploy a persistent backdoor on the targets’ systems in the form of a Tor SOCKS5 proxy.
This helped them create obfuscated communication channels for automated ransomware payload staging and delivery, and data exfiltration.
According to information collected by Sophos researchers while investigating recent Ryuk and Egregor ransomware attacks, SystemBC has been deployed in all their attacks during the last months.
“We are increasingly seeing ransomware operators outsource the deployment of ransomware to affiliates using commodity malware and attack tools,” said Sophos security researcher Sean Gallagher in a report shared in advance with BleepingComputer.
“SystemBC is a regular part of recent ransomware attackers’ toolkits— Sophos has detected hundreds of attempted SystemBC deployments worldwide over the last few months.”
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
Ryuk is deploying SystemBC on the domain controller together via multiple malware strains including Buer Loader, BazarLoader, and Zloader, while Egregor operators preferred using the Qbot information stealer.
The attacks investigated by Sophos used several multiple malware-as-a-service providers as a launching pad to deliver the initial malicious payloads and, according to the researchers, “they involved days or weeks of time on the targets’ networks and data exfiltration.”
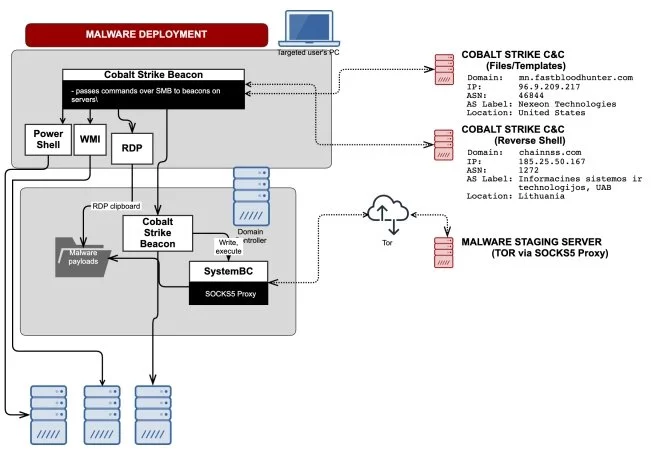
The ransomware operators use this persistent backdoor as a remote administration tool (RAT) together with the Cobalt Strike post-exploitation tool in the lateral movement stage of their attacks after gaining access to victims’ networks.
SystemBC is also used as a dedicated persistence and execution tool to automate various tasks including the deployment of the ransomware on network endpoints after exfiltrating stolen data.
Attackers also use it to execute commands on infected Windows devices sent over a Tor connection, as well as for delivering malicious scripts, dynamic link libraries (DLLs), and scripts that get automatically executed without requiring the operators’ manual intervention.
While these automation capabilities were originally designed to be used in mass exploitation attacks, RaaS operations have tweaked it to be used for mass deployment on the network of singular victims.
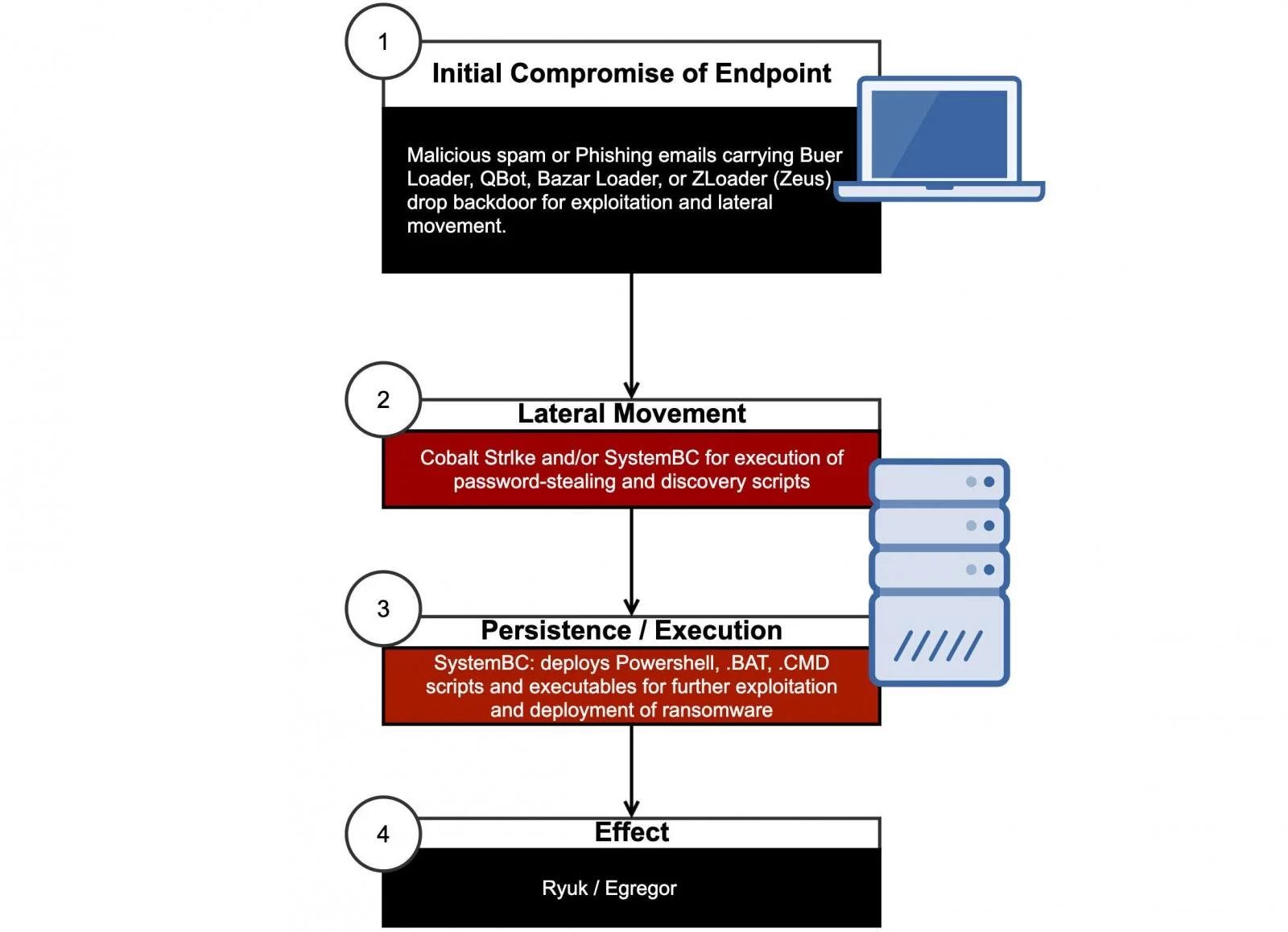
This enables the ransomware operators to manage attacks targeting multiple victims at a time, “allowing for hands-off deployment of ransomware using Windows built-in tools if the attackers gain the proper credentials.”
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
Even though some Windows anti-malware tools detect and block SystemBC deployment attempts, ransomware gangs are still able to drop them on their targets’ networks by using legitimate credentials stolen in the initial stages of their attacks or by taking advantage of less capable antivirus solutions.
“The use of multiple tools in ransomware-as-a-service attacks creates an ever more diverse attack profile that is harder for IT security teams to predict and deal with,” Gallagher said.
“Defense-in-depth, employee education and human-based threat hunting are essential to detecting and blocking such attacks.”