KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Vulnerability submissions have increased over the past 12 months on at least one crowdsourced security platform, with critical issue reports recording a 65% jump.
The data comes from the Bugcrowd platform and also reflects growth in payouts as ethical hackers are hunting down more critical vulnerabilities by chaining bugs and developing proof-of-concept exploit code.
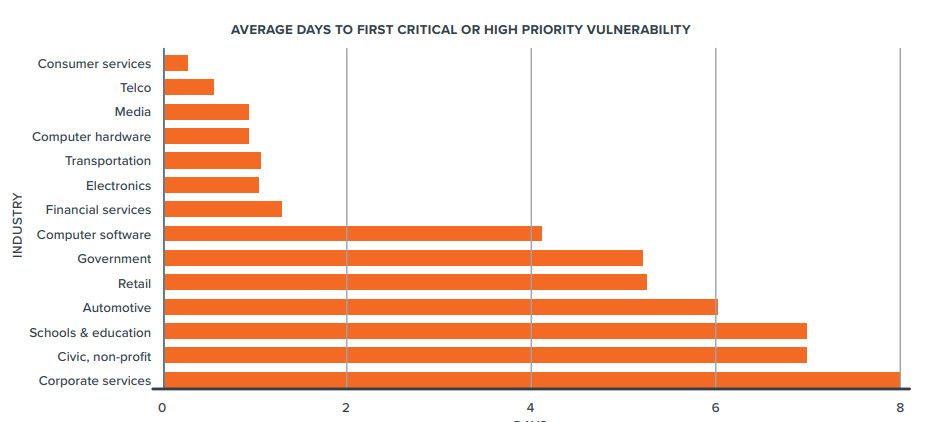
Bugcrowd says that companies offering consumer services and in the media industry receive critical reports for critical issues in less than a day.
For organizations in the government and automotive sectors, high-risk bugs are submitted in a matter of days and often represent “far higher stakes.”
This year, submissions for vulnerability submissions through Bugcrowd recorded a 50% increase, while for Priority 1 (the most critical) reports there was a growth of 65%.
Web apps remain in the hackers’ top preferences, although they are diversifying the targets to stay competitive.
Also Read: Trusted Data Sharing Framework IMDA Announced In Singapore
“In the last year, Bugcrowd saw submissions to all targets increase, though notably API vulnerabilities doubled, while those found in Android targets more than tripled”
– Bugcrowd
Between January and October 2020, organizations in the financial services saw more submissions than through the entire 2019. Payouts for P1 vulnerabilities in this sector doubled in the second quarter of this year.
Threat actors also intensified their attacks, driving companies to increase payouts for severe issues. Overall, payouts for critical vulnerabilities (P1) spiked by 31% from the first to the second quarter. The same happened for P2 bugs between Q2 and Q3.
At the top of the list of most submitted vulnerabilities through Bugcrowd is the human-driven broken access controls, taking down cross-site scripting (XSS).
Subdomain takeover also jumped two positions on the list, from six to four, the reason behind the jump being the hackers’ increased use of automation for their bug hunting sessions.
One trend prefiguring in bug hunting is the “outside in” approach that opens the bounty scope to obscure or forgotten assets (shadow IT) that expand a company’s cyber risk.
Bugcrowd observed this trend with companies that have a mature cybersecurity program, recognizin that their attack surface changed so frequently that it led to assets being overlooked.
Companies fitting this profile have added Attack Surface Management (ASM) to their crowdsourced security solution, to allow bug hunters to run reconnaissance activity and uncover unknown assets they own that may pose a risk.
Although zero-day vulnerabilities grab all the attention as they are typically associated with attacks from an advanced persistent threat (APT – usually government-backed hackers), most of the time these adversaries rely on known exploits.
“Bugcrowd data shows that our hunters were uncovering these vulnerabilities as they were deployed by the APT, acting as an important line of defense that ultimately overlaps with national security”
One example in the report refers to the remote code execution vulnerabilities in F5’s BIG-IP solutions (CVE-2020-5902). Bugcrowd says that bounty hunters had reported the issue on the platform before it was announced.
Also Read: The Importance Of Knowing Personal Data Protection Regulations
Bugcrowd notes that the changes recorded this year are in tune with the challenges of remote work imposed by the pandemic. By spending more time at home bug hunters were able to be more active and find higher-severity bugs as well as submit better quality reports.