KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Subway UK has disclosed that a hacked system used for marketing campaigns is responsible for the malware-laden phishing emails sent to customers yesterday.
Starting yesterday, Subway UK customers received strange emails from ‘Subcard’ about a Subway order that was placed. Included in the email were links to documents allegedly containing confirmation of the order.
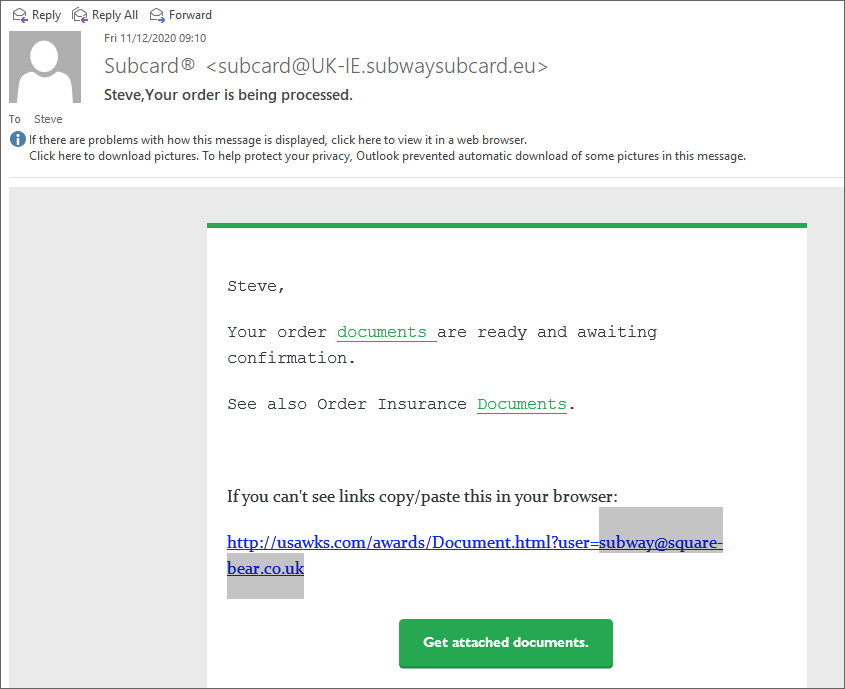
After analyzing these phishing emails, it was discovered that they were distributing malicious Excel documents that would install the latest version of the TrickBot malware.
TrickBot is a nasty malware infection that allows attackers to steal saved browser passwords, spread throughout a network, steal browser cookies, steal RDP, VNC, and PuTTY Credentials, and much more. Even worse, TrickBot may eventually provide access to the Ryuk or Conti ransomware operations.
Also Read: How Bank Disclosure Of Customer Information Work For Security
As these emails contained a customer’s name and were using email addresses that some users created specifically for Subway, it caused suspicion that Subway had been breached somehow.
When we contacted Subway yesterday about this phishing campaign, we received a response that alluded to a ‘disruption’ of some sort on their email systems.
“We are aware of some disruption to our email systems and understand some of our guests have received an unauthorised email. We are currently investigating the matter and apologise for any inconvenience. As soon as we have more information, we will be in touch, until then, as a precautionary measure, we advise guests delete the email,” a Subway spokesperson told BleepingComputer.
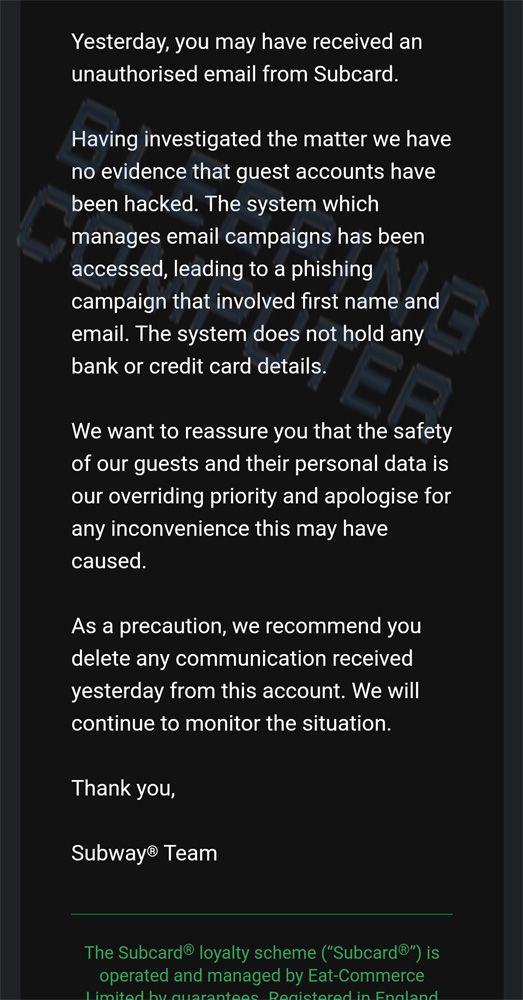
After sending multiple emails to Subway about the ‘disruption’ seen on their system, the company disclosed that a server responsible for their email campaigns had been hacked to send out the phishing emails.
“Having investigated the matter, we have no evidence that guest accounts have been hacked. However, the system which manages our email campaigns has been compromised, leading to a phishing campaign that involved first name and email. The system does not hold any bank or credit card details.”
“Crisis protocol was initiated and compromised systems locked down. The safety of our guests and their personal data is our overriding priority and we apologise for any inconvenience this may have caused,” Subway said in a statement to BleepingComputer.
Subway has also started to send disclosure emails to affected customers that states that the customer’s first name and last name were exposed in the attack.
If you received this email and mistakenly opened the malicious Excel document, you can check for the current version of TrickBot by opening Task Manager and looking for a process named ‘Windows Problem Reporting.’ If that process is found, click on the ‘End Task’ button, as shown by the red arrow below, to terminate it.
Also Read: Data Protection Framework: Practical Guidance For Businesses
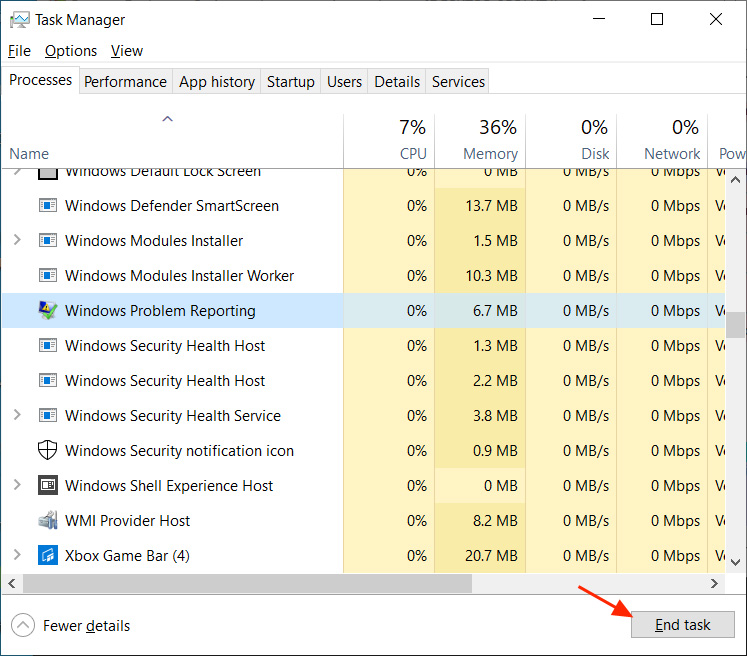
Now perform a thorough scan of your computer using antivirus software and clean anything that is found.
BleepingComputer has once again reached out to Subway to determine how many people were affected and if any other customer information was stored on that server. We have not received a response at this time.